Turkish cybersecurity experts at Malwation have uncovered a large-scale phishing campaign targeting enterprises in the defense and aerospace sectors. Threat actors are disguising malicious attachments as official documents purportedly issued by TUSAŞ, Turkey’s state-owned aerospace corporation, in an effort to deceive employees and gain access to internal corporate systems.
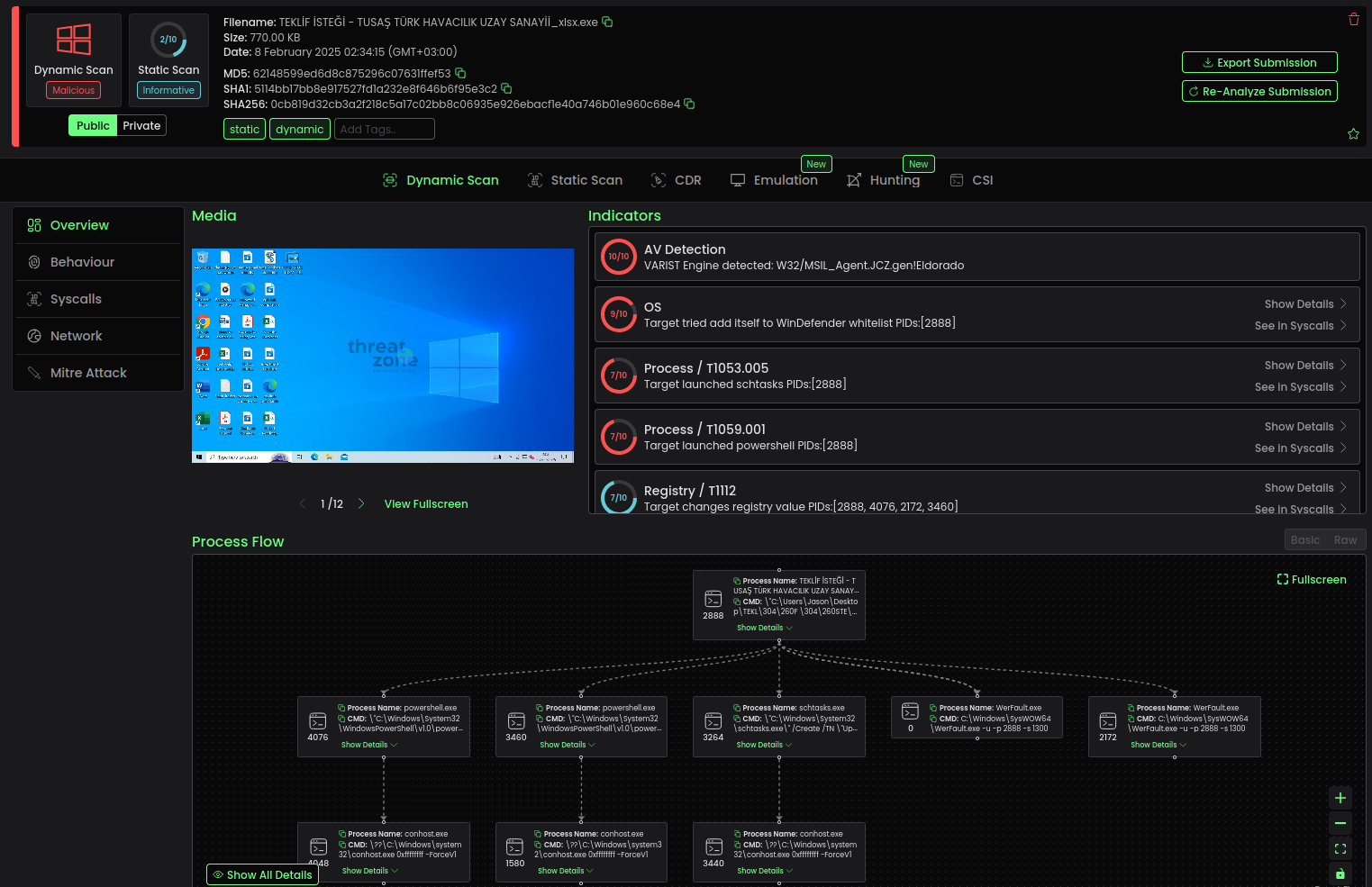
The phishing emails are accompanied by attachments masquerading as legitimate business documents—allegedly related to tenders and contracts on behalf of TUSAŞ. These files, which appear to be Excel spreadsheets or Word documents, are in fact executable PE32 programs for Windows, built on the .NET platform and embedding a modified variant of the Snake Keylogger malware.
Snake Keylogger is a malicious program designed to steal sensitive information, including login credentials, passwords, cookies, credit card data, and autofill entries. Its evasion techniques reflect a high degree of sophistication: immediately upon execution, the malware disables Windows Defender using PowerShell commands and adds itself to the exclusion list. It then establishes persistence by registering a task through the built-in Windows Task Scheduler, generating XML configuration files in temporary directories.
The incident was swiftly reported to Turkey’s national Computer Emergency Response Team (USOM), which is currently coordinating notifications to potential victims and spearheading efforts to neutralize the threat. A deeper analysis revealed that the initial executable launches a benign-looking Windows Forms application named “temperatureConverterForm,” which appears to perform only temperature conversions—an effective ruse to conceal the true intent of the malware until its malicious components are fully deployed.
Subsequent execution leads to the in-memory loading of embedded .NET assemblies via methods such as Assembly.Load and Activator.CreateInstance. The structure resembles a nesting doll—each code layer triggers the next until the final payload, dubbed “Remington,” is executed. While some of the anti-analysis mechanisms in this assembly are placeholders, their presence suggests potential for further development and sophistication.
The malware extracts data from email clients including Outlook, FoxMail, and Thunderbird. It scans the Windows Registry, retrieves encrypted passwords, and decrypts them using embedded routines. It also harvests information from over 30 web browsers—Chrome, Firefox, Edge, Vivaldi, Brave, and others—gathering cookies, download histories, autofill data, payment card details, and browsing records.
Additional capabilities include sandbox and virtual environment detection, along with checks against known sandbox IP addresses. Stolen data can be exfiltrated via SMTP email servers, FTP, or Telegram. One configuration file contained DES-encrypted credentials for email transmission, including the address “mail.htcp.homes” and the login “royals@htcp.homes.” Decryption is possible using Python scripts with MD5-derived keys.
To detect such activity, researchers recommend applying a tailored YARA rule capable of identifying samples obfuscated with the Cassandra Protector. Indicators include usage of the System.Drawing.Bitmap library and high entropy in the code. Analytical tools also detect system-level calls such as NtCreateUserProcess, PowerShell commands to disable security features, and the use of schtasks.exe for persistence.
This campaign underscores the growing sophistication of phishing attacks involving malicious attachments, particularly those aimed at sensitive industries. It also highlights the urgent need for stricter email filtering, behavioral detection systems, and runtime monitoring to effectively defend against such advanced threats.






