Rapid7 Uncovers Social Engineering Campaign Linked to Black Basta Ransomware
Researchers have identified an actively evolving social engineering campaign aimed at gaining initial access to corporate IT systems for further exploitation. The perpetrators bombard enterprises with spam emails to capture the attention of employees.
According to Rapid7, hackers inundate victims with useless emails and then call them, posing as IT specialists offering assistance to resolve the issue. Users are asked to install remote management software like AnyDesk or use the built-in Windows tool Quick Assist.
This campaign has been ongoing since late April 2024. The spam primarily consists of subscription confirmation emails from legitimate organizations. This method also aims to overwhelm spam protection mechanisms on corporate servers.
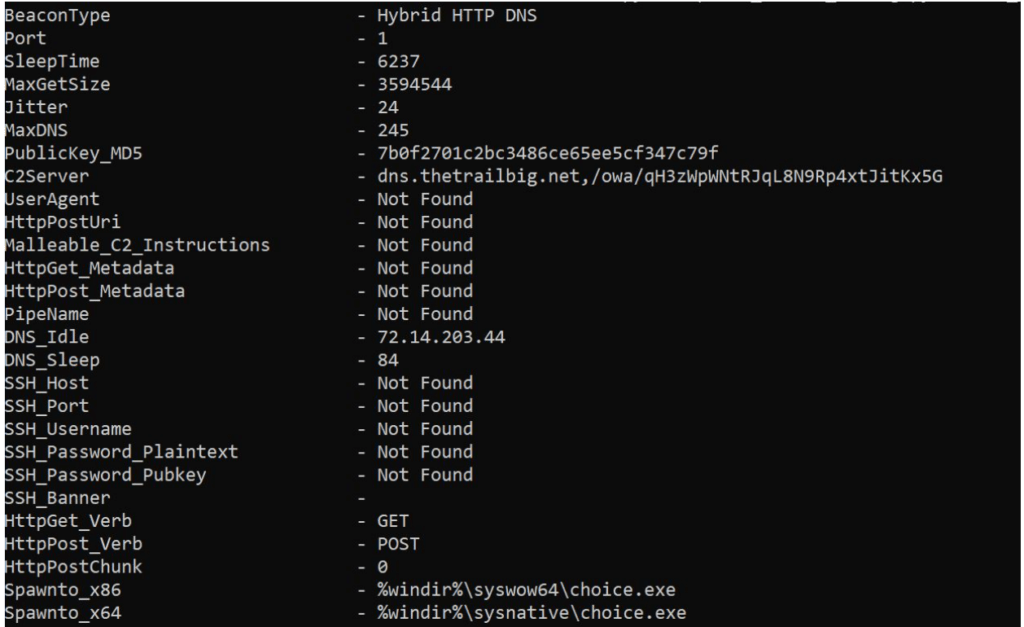
Sample Cobalt Strike Configuration
Once remote access is gained, cybercriminals deploy malware to steal credentials and maintain persistent access to compromised systems. Various batch scripts are used for this purpose, one of which establishes a connection with a command server, downloads OpenSSH for Windows, and initiates a reverse web shell.
In one documented instance, the attackers attempted to deploy Cobalt Strike malware to propagate across the corporate network, but this attempt was unsuccessful. Remote administration tools such as ConnectWise ScreenConnect and the NetSupport RAT were also utilized.
Researchers note that the campaign bears a strong resemblance to previous operations associated with the Black Basta ransomware. There are also indications of involvement by the FIN7 hacking group, which recently used NetSupport RAT in a malvertising campaign.
Initially, FIN7 specialized in financial fraud using software to steal data from payment terminals. However, the group has recently shifted towards ransomware operations, acting either as an affiliate partner or independently under the names DarkSide and BlackMatter.
Although there is no evidence of ransomware activity in the described operation, experts warn that the participants possess all the necessary capabilities to conduct such attacks.





