Experts have uncovered disconcerting connections between the recently emerged Alpha ransomware and the criminal group Netwalker, which was dismantled several years ago.
Netwalker operated from October 2019 to January 2021, offering its software to other malefactors under a “ransomware-as-a-service” (RaaS) model. Following law enforcement’s blockade of the group’s darknet sites, Netwalker’s operators ceased their illicit activities and vanished from the radar.
The Alpha ransomware first appeared in February 2023, initially operating covertly, eschewing promotion on hacker forums, and refraining from conducting widespread attacks. Over time, the criminals launched a website to publish stolen company data, demanding ransom for its return.
Currently, the Alpha site lists information about 9 cyber attacks, with stolen data already posted in 8 instances. According to a January 29 report by Neterich, the ransomware has been progressively refined. The latest version appends a random 8-character alphanumeric extension to encrypted files.

Ransom demands now include instructions for contacting cybercriminals. According to Neterich, amounts vary from $13,200 to $100,000, depending on the revenue of the targeted organization.
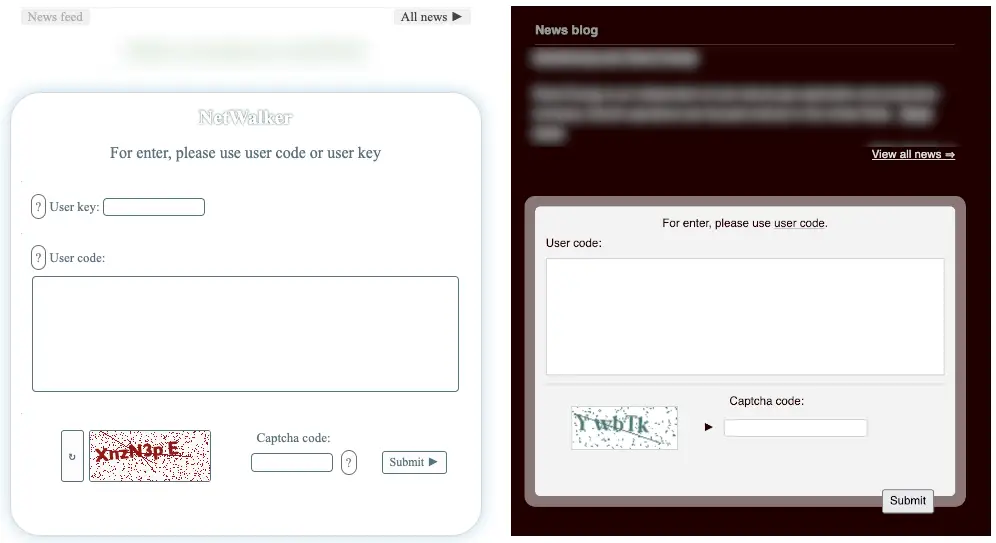
Symantec has identified connections between the Alpha ransomware and Netwalker’s criminal activities in its recent report. This link is evident in the tools and cyberattack methods employed by the new group.
Key similarities include:
- The use of similar PowerShell-based loaders for stealthy ransomware delivery.
- Matching structure and code snippets, particularly in file encryption functions, disabling processes and services, and invoking system APIs.
- Similar configurations for excluding files, folders, processes, and services from the encryption process.
- The malware automatically deletes itself after encryption using special temporary batch files.
- Identical messages on payment pages regarding the need for a user code.
Moreover, in recent attacks, Alpha has actively utilized built-in Windows tools, a tactic common to many hacker groups.
Thus, researchers have substantial grounds to believe that the developers of Netwalker and Alpha are closely linked. Either Alpha represents a rebranding of Netwalker, or its code is being utilized by a new group of cybercriminals. According to Symantec’s experts, someone may have illicitly acquired Netwalker’s code and adapted it for their purposes.
Although Alpha is not currently a major player in the ransomware market, analysts assess the potential of this new cyber threat as significantly high and rapidly growing.






