RA World Ransomware Strikes Latin American Healthcare
Trend Micro recently unveiled a new wave of activity by the ransomware group RA World, also known as the RA Group. This group initiated its malicious operations in April 2023 and has, over its tenure, launched attacks on numerous organizations, predominantly within the healthcare and financial sectors across the United States, Germany, India, and Taiwan.
Researchers discovered that the latest offensive by RA World targeted several healthcare organizations in Latin America. The attacks were executed in phases to maximize the overall chances of a successful operation.
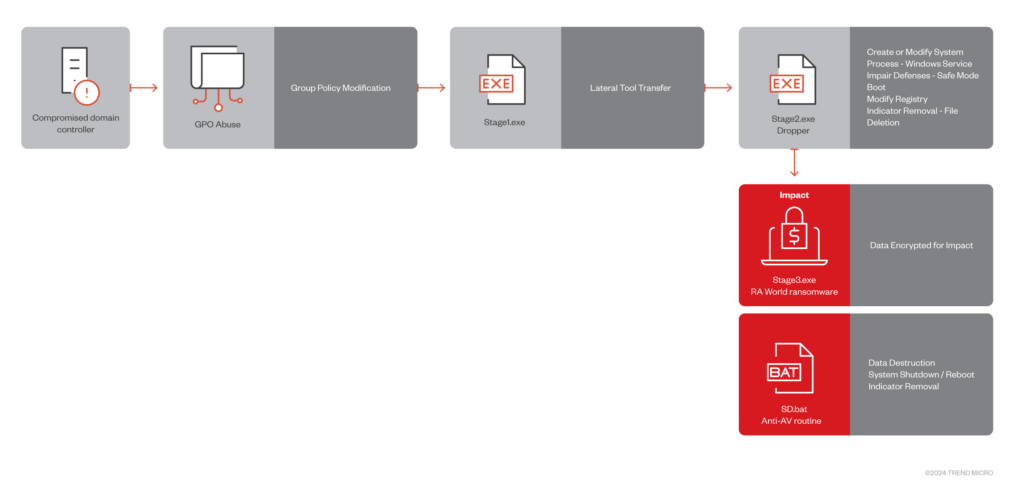
The RA World attack chain
The initial access phase begins with hackers penetrating the computer system via domain controllers. Here, the editing of Group Policy Objects (GPO) plays a critical role, enabling the perpetrators to impose their rules within the victim’s system.
In the first stage, utilizing the “Stage1.exe” file, the malware assesses and prepares the network for further assault. This includes inspecting domain controllers and setting the stage for copying the next phase of the malware.
The second stage sees the malware replicating itself across other machines within the network and preparing for file encryption. “Stage2.exe” is tasked with spreading the malicious code throughout the target network, laying the groundwork for the primary attack.
The final phase, executed by “Stage3.exe,” activates the malware, encrypting files on infected computers and demanding a ransom for their recovery. It employs complex encryption methods, rendering the files inaccessible to both users and systems.
Moreover, the malware can reboot the system in a special safe mode to evade detection by antivirus software. It also erases traces of its presence post-attack, complicating analysis efforts for researchers.
To minimize the risk of falling victim to RA World’s attacks, it is recommended to employ best defensive practices: restrict administrative privileges, promptly update software, regularly backup data, exercise caution when interacting with emails and websites, and train company staff in the fundamentals of cybersecurity.
Adopting a comprehensive approach to security significantly strengthens potential access points into the system, markedly enhancing corporate protection.





