Polish researcher releases new tools that automatically bypass 2FA for phishing attacks
Piotr Duszyński, a Polish security researcher released a new penetration testing tool called Modlishka. This tool makes it easy to automate phishing attacks and even break accounts that are protected by 2FA (two-factor authentication).
Modlishka is a flexible and powerful reverse proxy, that will take your phishing campaigns to the next level (with minimal effort required from your side).
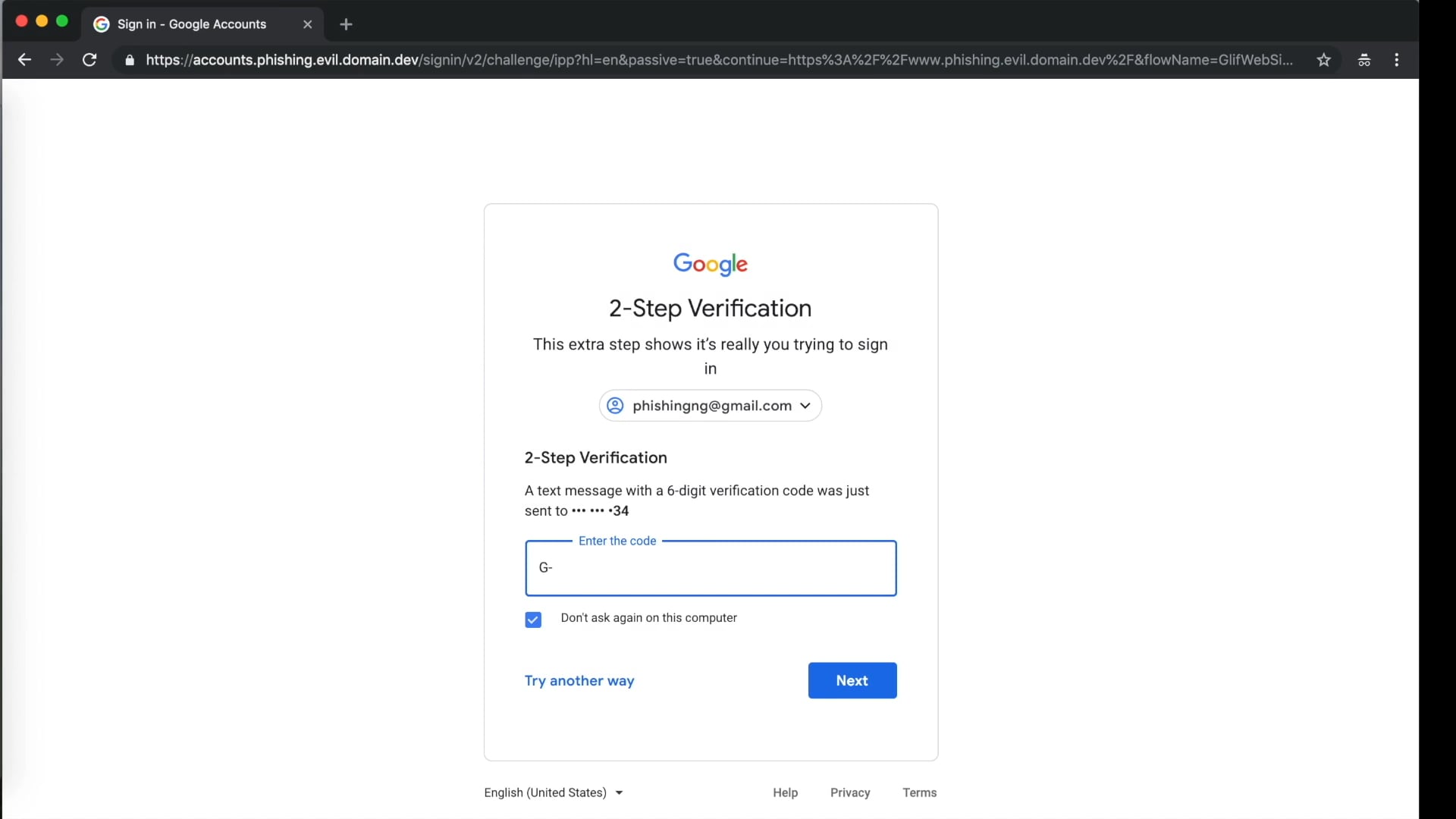
Modlishka is located between the user and the target website (such as Gmail, Yahoo or ProtonMail). When the victim connects to the Modlishka server (hosted phishing domain), the reverse proxy component behind it sends a request to the simulated site. Although the victim receives the real content from the legitimate site, all traffic and interaction information between the victim and the legitimate site passes through and is recorded on the Modlishka server. The password entered by the user will be automatically recorded to the Modlishka backend panel. When the user applies for an account 2FA token, the reverse proxy also prompts the user to enter a 2FA token. If an attacker can collect these 2FA tokens in real time, they can log in to the victim’s account and establish a new legitimate session.
Modlishka is designed to be simple and does not require any templates. All content can be obtained in real time from legitimate sites, so the attacker does not need to spend a lot of time updating and adjusting the template. The attacker only needs a phishing domain (for the Modlishka server) and a valid TLS certificate to avoid the user receiving a warning that the HTTPS connection is missing.
Phishing with Modlishka (bypass 2FA) from Piotr Duszynski on Vimeo.
According to the info on the Github page,
Some of the most important ‘Modlishka’ features :
- Support for majority of 2FA authentication schemes (by design).
- No website templates (just point Modlishka to the target domain – in most cases, it will be handled automatically).
- Full control of “cross” origin TLS traffic flow from your victims browsers.
- Flexible and easily configurable phishing scenarios through configuration options.
- Pattern based JavaScript payload injection.
- Striping website from all encryption and security headers (back to 90’s MITM style).
- User credential harvesting (with context based on URL parameter passed identifiers).
- Can be extended with your ideas through plugins.
- Stateless design. Can be scaled up easily for an arbitrary number of users – ex. through a DNS load balancer.
- Web panel with a summary of collected credentials and user session impersonation (beta).
- Written in Go.
Modlishka is now available on GitHub, you can also get more info on the researcher’s blog.