PixPirate Trojan Exposed: Stealing From Brazilian Android Users
IBM has unveiled details about the Trojan program PixPirate, which targets Android users in Brazil, circumventing security systems on infected devices and pilfering financial information.
PixPirate employs a cunning strategy that allows it to conceal its application icon from the victim’s device’s main screen, rendering it invisible to the user during the reconnaissance and attack phases. This technique enables PixPirate to operate in the background without arousing the victim’s suspicion.
PixPirate is capable of:
- Exploiting Android accessibility services to perform unauthorized financial transfers via the PIX instant payment platform;
- Stealing online banking credentials;
- Capturing bank card information;
- Registering keystrokes (keylogging);
- Intercepting SMS messages to access two-factor authentication codes.
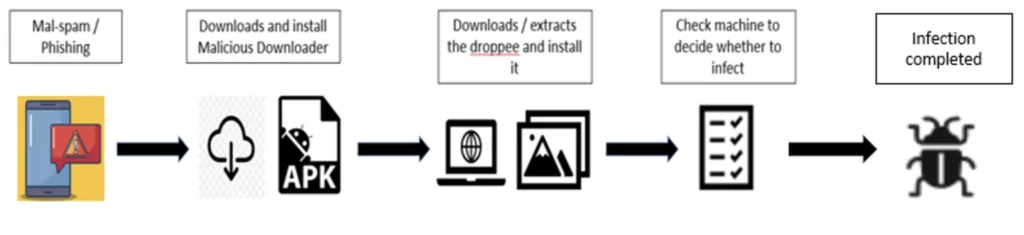
PixPirate spreads via SMS and WhatsApp, using a loader application to install the main component responsible for financial fraud. Unlike traditional attacks where the loader only serves to download and install, in the case of PixPirate, it actively participates in fraudulent operations, executing commands and exchanging messages with the main component.
Upon launch, the loader APK prompts the victim to update the application, either to retrieve the PixPirate component from the attacker’s server or to install the component if it is embedded within the application itself.
The latest version of the malware lacks an activity that would allow launching the application from the main screen, making it even more covert. Even if the loader is removed from the device, the main component continues to function, thanks to persistence mechanisms activated by various system events.
PixPirate was first documented by Cleafy in February 2023. At that time, experts noted that PixPirate belongs to the latest generation of banking Trojans for Android, as it can not only disable Google Play Protect but also perform Automated Transfer System (ATS) functions. This feature allows attackers to automate the process of malicious financial transfers through the Pix instant payment platform, actively used by several Brazilian banks.