Phishing Waters Rise: Pikabot Malware Casts Net for Black Basta Deployment
Trend Micro has documented the active proliferation of the malicious software PikaBot by the group Water Curupira. Their operations commenced in the first quarter of 2023 and continued until the end of June, resuming again in September.
PikaBot, employed in phishing campaigns, comprises two components: a loader and a main module. This structure facilitates unauthorized remote access and the execution of arbitrary commands through a connection with a command-and-control server, reducing the risk of detection.
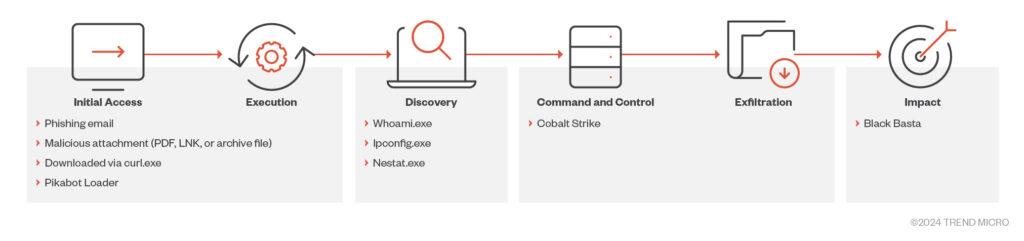
Image: Trend Micro
The activities of Water Curupira intersect with previous campaigns that employed similar tactics for delivering QakBot, conducted by groups TA571 and TA577. The escalation in PikaBot activities is linked to the termination of QakBot in August and the emergence of the malware DarkGate.
Primarily functioning as a loader, PikaBot initiates other malicious programs, including the post-exploitation tool Cobalt Strike, often used before the deployment of ransomware.
The tactic for disseminating PikaBot is painfully simple and familiar: hackers integrate malicious attachments into emails and downloading and executing these leads to the computer being infected with malware.
Notably, before initiating the infection chain, the loader checks the language of the Windows operating system and halts execution if it detects Russian or Ukrainian languages. This raises intriguing questions about the possible origins of the Water Curupira group.
If a computer is vulnerable, PikaBot gathers detailed information about the victim’s system and sends it to the command-and-control server in JSON format. The objective of Water Curupira’s malicious campaigns is the deployment of Cobalt Strike, often leading to subsequent ransomware attacks, particularly with Black Basta.
Furthermore, Trend Micro notes that Water Curupira conducted several campaigns using DarkGate and a small number of IcedID campaigns at the beginning of the third quarter of 2023, after which the group completely transitioned to using PikaBot.





