The pentester's Swiss knife
The hacker group behind the Grandoreiro banking Trojan for Windows has resumed its global campaign as of March 2024, following a law enforcement operation that dismantled its infrastructure in January. According to IBM X-Force,...
Students Alexander Sherbrooke and Iakov Taranenko from the University of California, Santa Cruz, discovered a critical vulnerability in the payment system of CSC ServiceWorks laundries, allowing anyone to use the machines for free. Despite...
A group of scientists from Singapore has developed a method to interfere with the operation of autonomous vehicles that use computer vision for road sign recognition. The new technique, called GhostStripe, poses a potential...
A recent video by the popular YouTuber Eric Parker sparked a storm of emotions among internet users. Parker vividly demonstrated the dangers of connecting old operating systems to the internet without any protection, including...
Researchers from Cyble have discovered a new banking Trojan targeting Android devices. This sophisticated malware possesses a multitude of dangerous features, including overlay attacks, keylogging, and obfuscation techniques. The Trojan, named “Antidot” based on...
The hacker group Pink Drainer has announced the conclusion of their activities, claiming to have achieved their goal of stealing $85 million in cryptocurrency. The group promised to dismantle the infrastructure used in their...
The United States is offering a reward of up to $5 million for information that helps disrupt the employment scheme of North Korean hackers in remote IT positions within American companies. The U.S. State...
The Kinsing cryptojacking group continues to evolve, posing a persistent threat in the digital realm. AquaSec reports that since 2019, Kinsing has been orchestrating illicit cryptocurrency mining campaigns, swiftly integrating new vulnerabilities to expand...
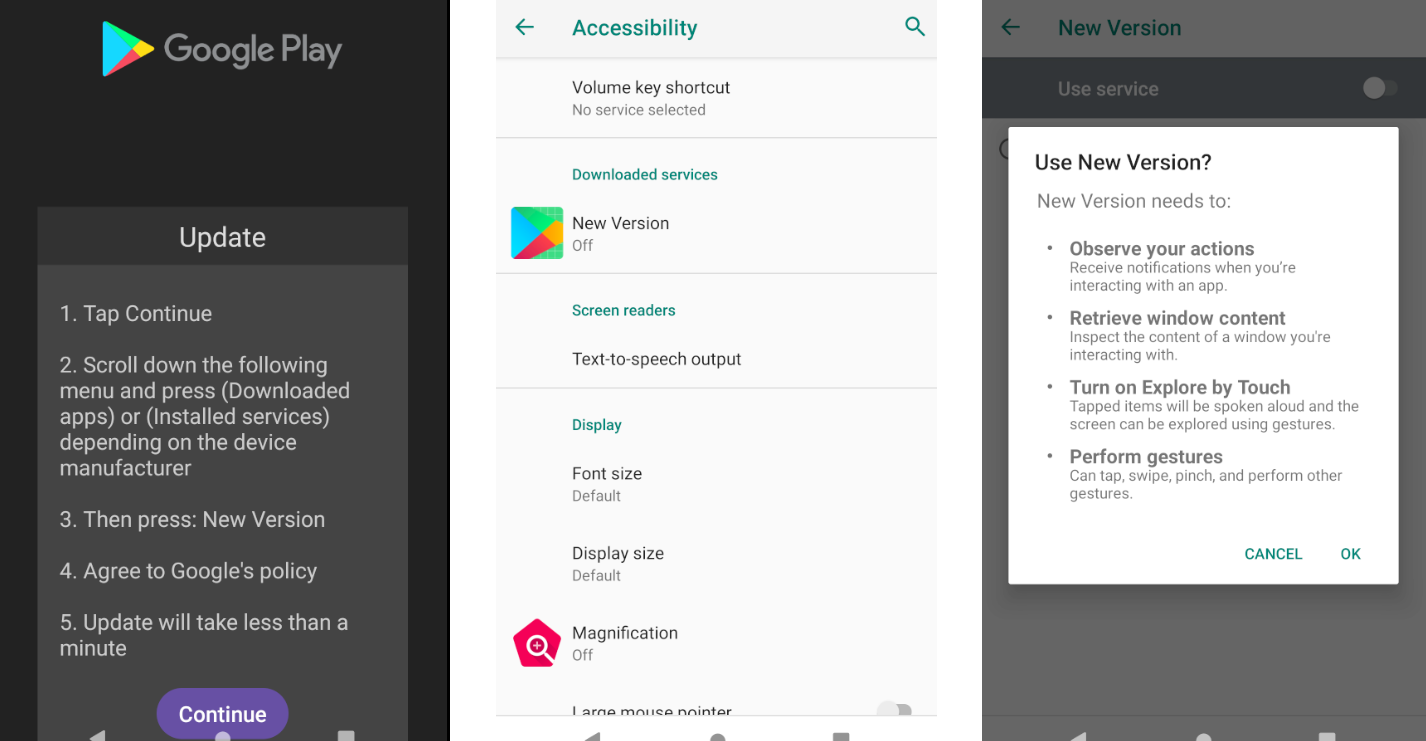
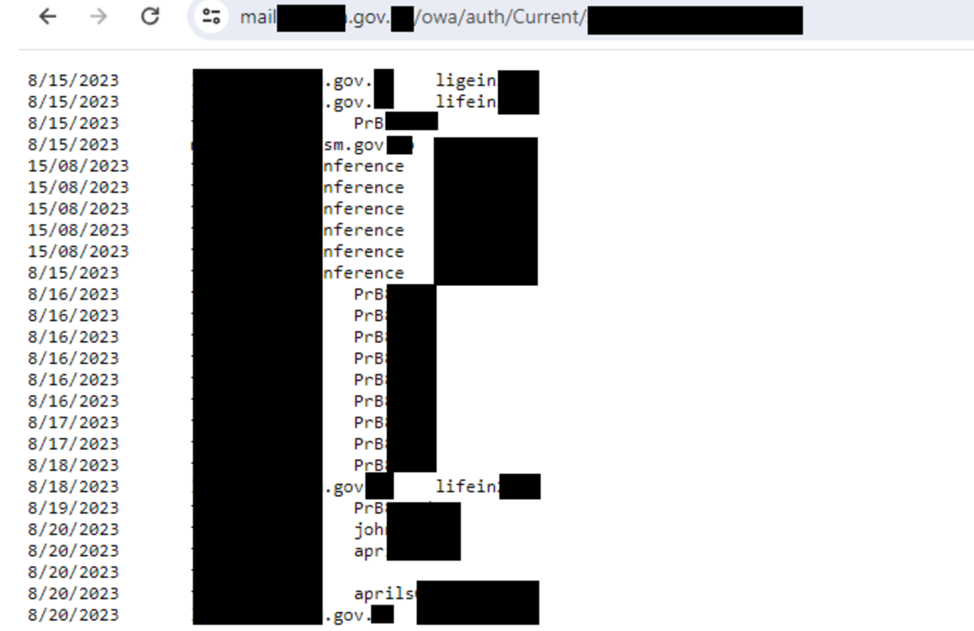
The Positive Technologies Expert Security Center (PT Expert Security Center) reported the discovery of a previously unknown keylogger embedded in the main page of Microsoft Exchange Server, which collected account input data in a...
Recently, Samsung unveiled the Galaxy Book4 Edge series laptops, proclaiming them “designed for AI.” Available in 14-inch and 16-inch variants, both models feature the Qualcomm Snapdragon X Elite processor and a 3K OLED display....
Many investors choose the BVI (British Virgin Islands) to register an investment fund. The BVI strategy is focused on providing high level professional services rather than simply providing traditional offshore services. The BVI...
Cybersecurity researchers have unveiled new details about a remote access Trojan called Deuterbear RAT, used by the China-affiliated hacker group BlackTech in a cyber-espionage campaign targeting the Asia-Pacific region. BlackTech, active since at least...
The Norwegian National Cyber Security Centre (NCSC) strongly advises organizations to replace SSL VPN/WebVPN with more secure alternatives due to the frequent exploitation of vulnerabilities in network devices. This measure aims to protect corporate...
The Cybersecurity and Infrastructure Security Agency (CISA) has added two new vulnerabilities in D-Link routers to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of their active exploitation. The CSRF vulnerability CVE-2014-100005 affects...
Security researchers from Proofpoint have discovered that a hacker group, presumably operating in the interest of China, is using a new version of the SugarGh0st RAT malware to steal information from artificial intelligence experts...
In March, North Korea laundered $147.5 million through the cryptocurrency mixer Tornado Cash, stolen from the cryptocurrency exchange HTX in 2023. This was reported by Reuters, citing confidential UN sanctions monitoring documents. According to...