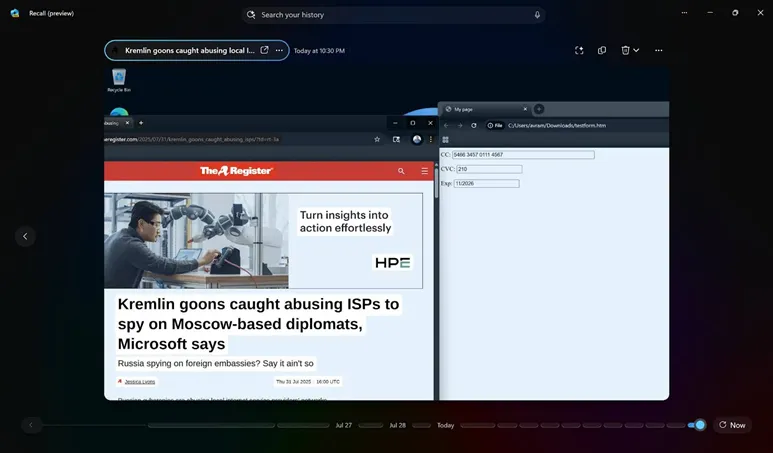
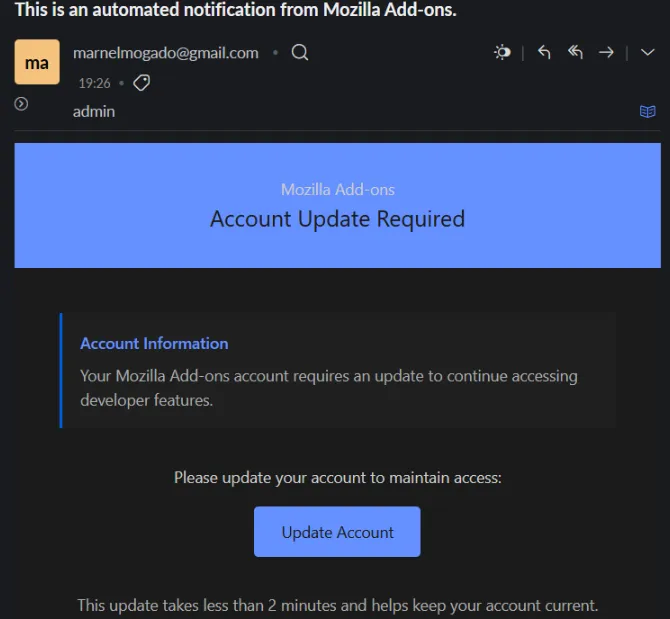
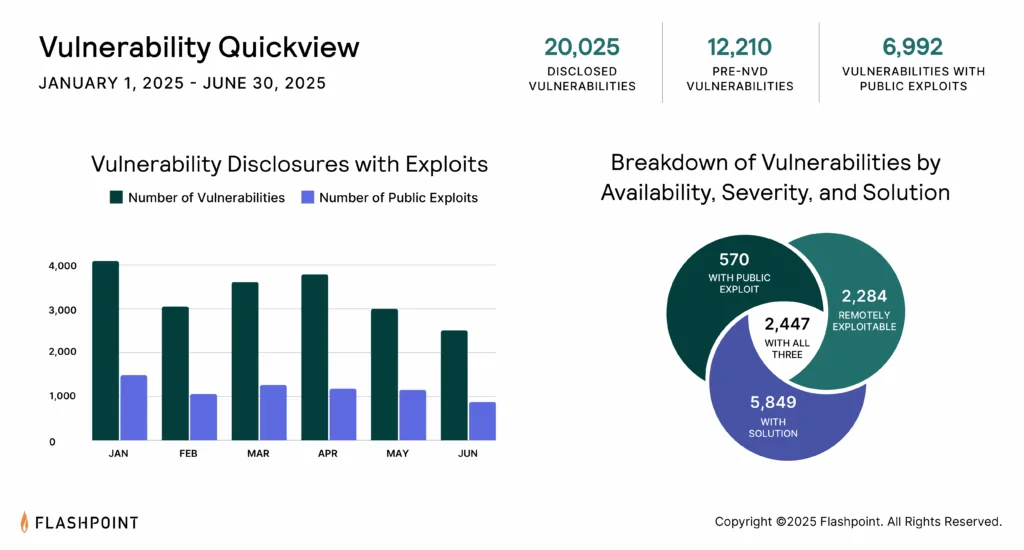
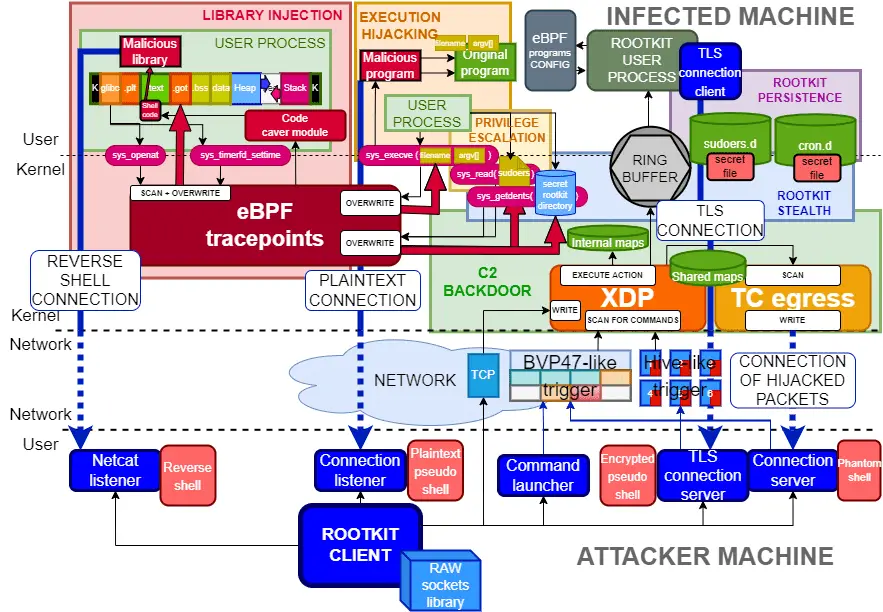
The Dark Side of Recall: Microsoft’s AI Feature is Still Capturing Sensitive Data and Poses Grave Security Risks
In the autumn of 2024, Microsoft reintroduced a controversial feature in Windows called Recall—an artificial intelligence system that periodically captures screenshots, allowing users to later search through their entire on-screen activity. Marketed as a...