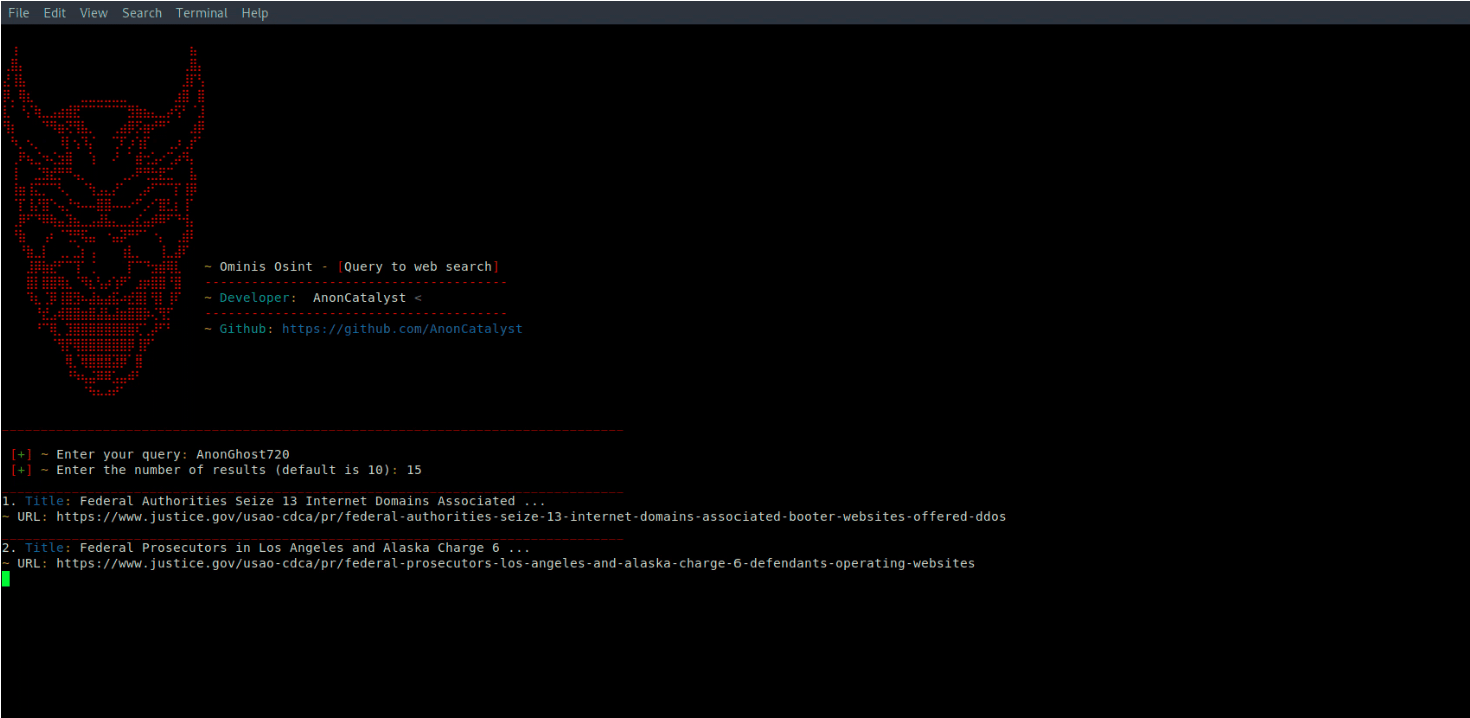
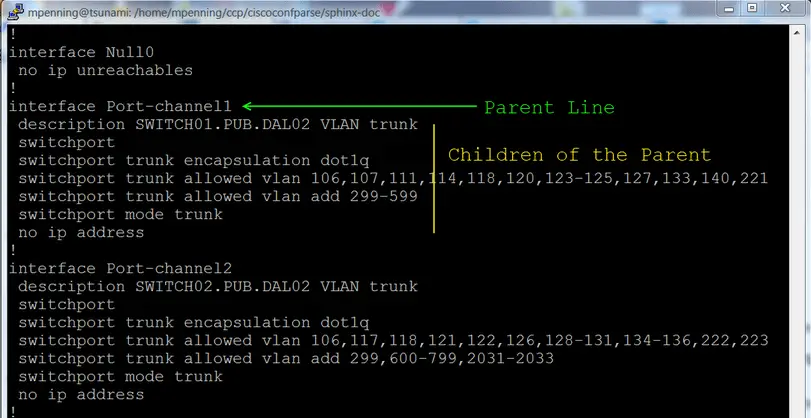
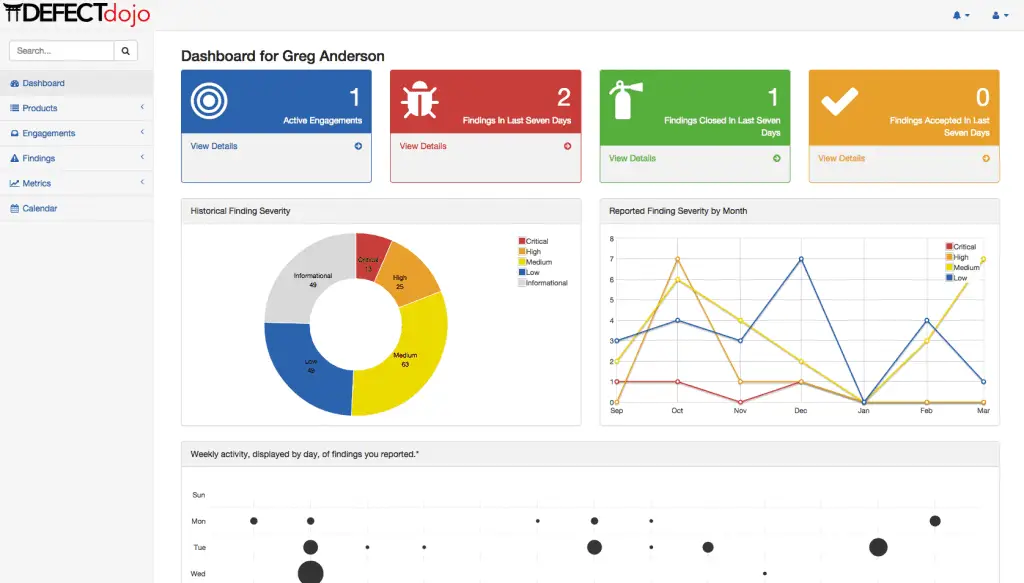
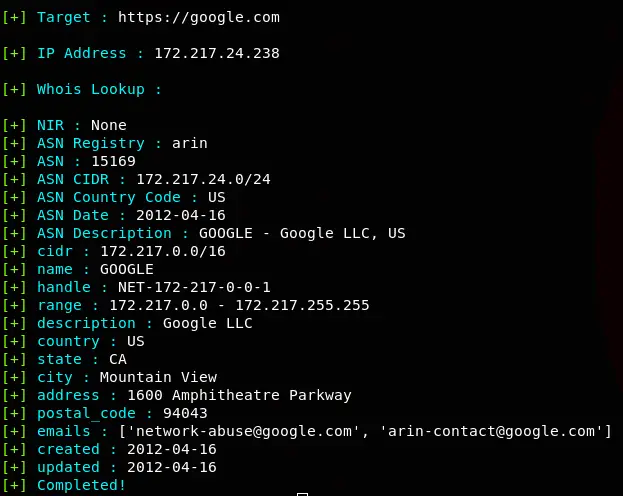
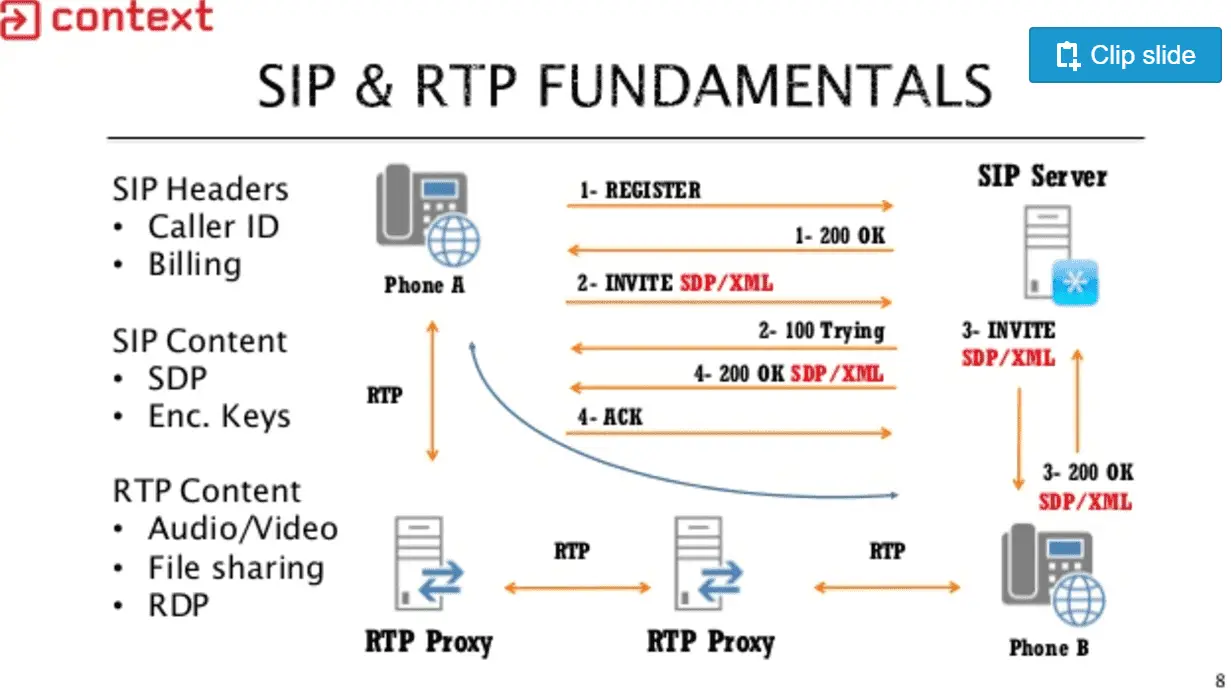
CrowdSec: Real-time & crowdsourced protection against aggressive IPs
CrowdSec The CrowdSec Security Engine is an open-source, lightweight software that detects and blocks malicious actors from accessing your systems at various levels, using log analysis and threat patterns called scenarios. CrowdSec is a modular framework,...