On August 24, 2025, the world marked the 30th anniversary of Windows 95—Microsoft’s first truly mass-market 32-bit...
The creator of the spyware TheTruthSpy—the Vietnamese company 1Byte Software, led by Vanh (Vardi) Tiu—has once again...
The Auchan retail chain has fallen victim to a cyber incident targeting its customer loyalty program. This...
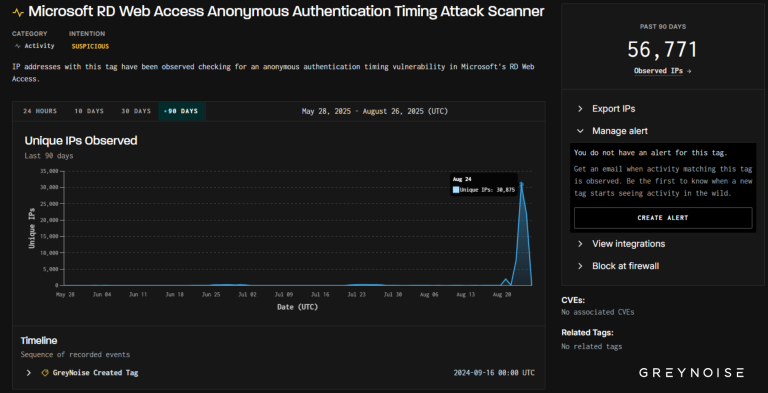
GreyNoise has observed a sharp and highly atypical surge in reconnaissance activity targeting Microsoft Remote Desktop Web...
A new study by specialists at The Trail of Bits has revealed a previously unknown vulnerability in...
Microsoft has issued a warning over the growing surge of large-scale ClickFix phishing attacks and has recommended...
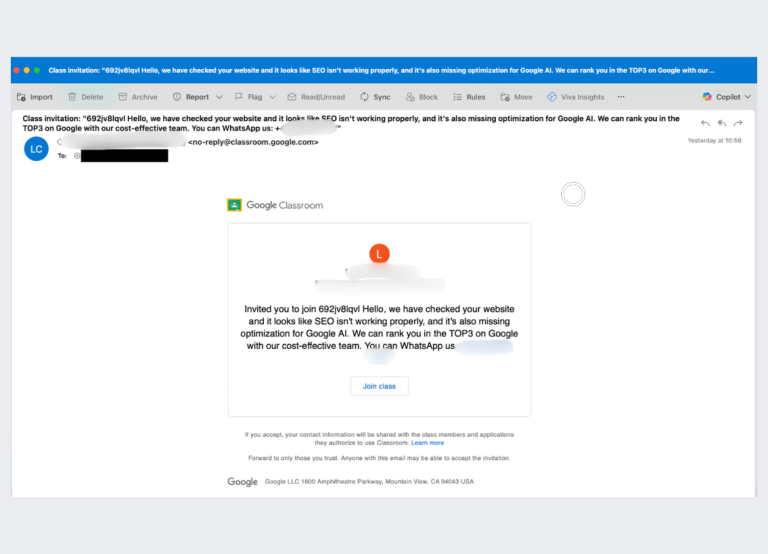
An attack on Google Classroom has escalated into one of the largest phishing campaigns in recent months....
CloudSEK researchers have uncovered a new attack vector, dubbed ClickFix, which exploits invisible prompt injection and the...
With each passing year, the number of cryptocurrency-related attacks orchestrated by North Korean groups continues to grow....
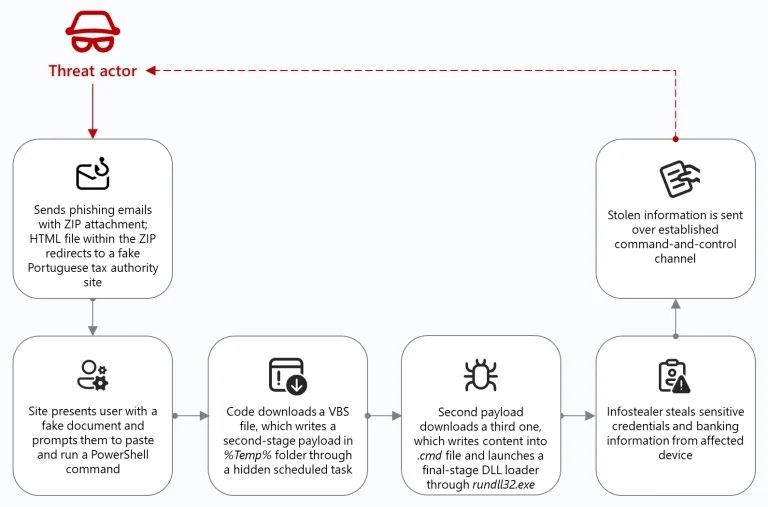
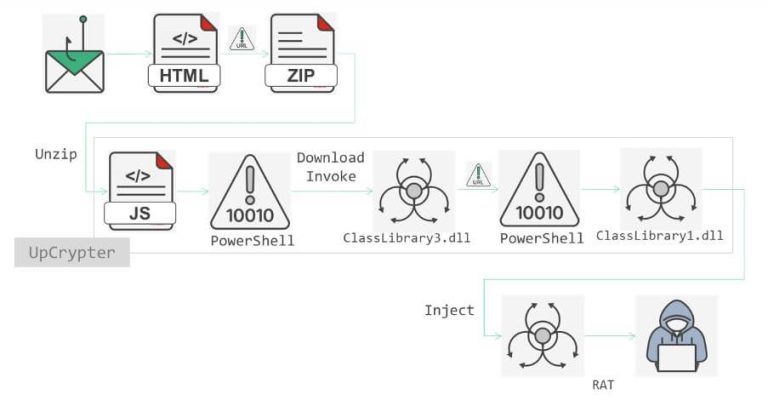
In early August 2025, specialists at Fortinet FortiGuard Labs detected a large-scale phishing campaign distributing the UpCrypter...
GhostBSD has unveiled an updated release, version 25.02-R14.3p2. Built upon FreeBSD 14.3, this iteration delivers bug fixes...
Authorities in the U.S. state of Maryland are investigating a cyberattack that has compromised information systems used...
The Android mobile ecosystem has been struck by a new wave of threats driven by the evolution...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added three new vulnerabilities to its Known Exploited...
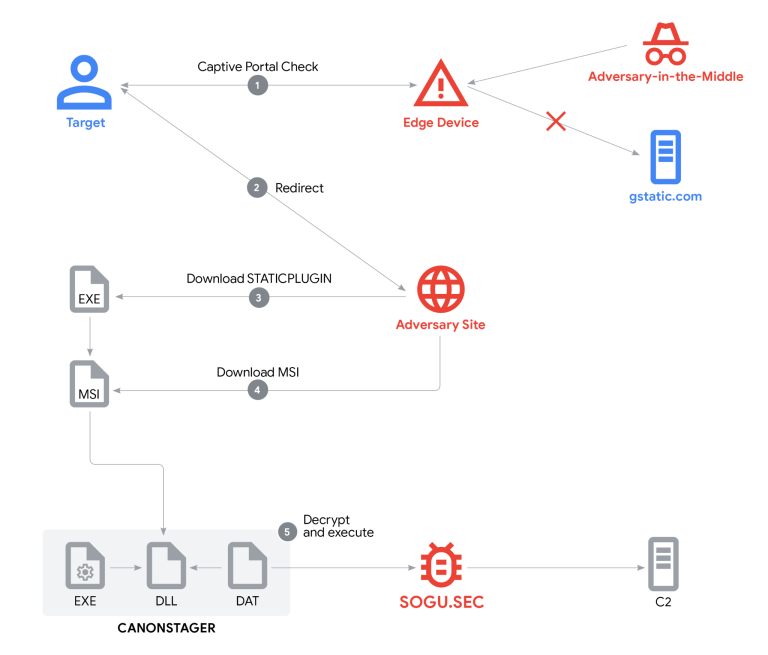
The Chinese group UNC6384 has launched a series of attacks against diplomats in Southeast Asia and several...
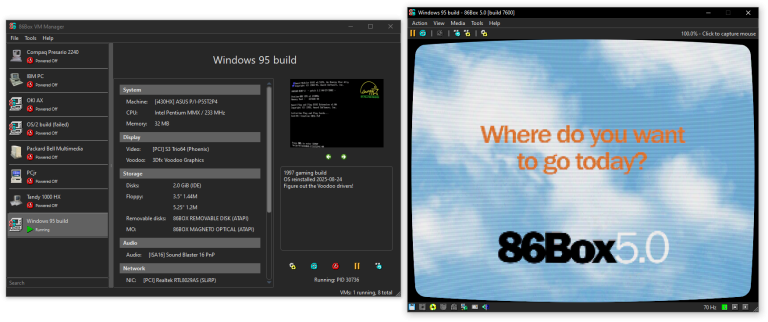
The 86Box project has released version 5.0 of its x86-based computer emulator, enabling users to run legacy...