The pentester's Swiss knife
BLAKE3 BLAKE3 is a cryptographic hash function that is: Much faster than MD5, SHA-1, SHA-2, SHA-3, and BLAKE2. Secure, unlike MD5 and SHA-1. And secure against length extension, unlike SHA-2. Highly parallelizable across any number of...
Argus Argus is an all-in-one, Python-powered toolkit designed to streamline the process of information gathering and reconnaissance. With a user-friendly interface and a suite of powerful modules, Argus empowers you to explore networks, web...
Loki: like Prometheus, but for logs. Loki is a horizontally-scalable, highly-available, multi-tenant log aggregation system inspired by Prometheus. It is designed to be very cost-effective and easy to operate. It does not index the contents...
ssh-mitm – intercept ssh traffic ssh-mitm is an intercepting (mitm) proxy server for security audits. Redirect/mirror Shell to another ssh client supported in 0.2.8 Replace File in SCP supported in 0.2.6 Replace File in SFTP...
Kraken Kraken is a powerful, Python-based tool designed to centralize and streamline various brute-forcing tasks. Kraken provides a suite of tools for cybersecurity professionals to efficiently perform brute-force attacks across a range of protocols and...
Cryptomator Cryptomator is provided free of charge as an open-source project despite the high development effort and is therefore dependent on donations. Cryptomator offers multi-platform transparent client-side encryption of your files in the cloud....
kics KICS stands for Keeping Infrastructure as Code Secure, it is open source and is a must-have for any cloud-native project. Find security vulnerabilities, compliance issues, and infrastructure misconfigurations early in the development cycle of your infrastructure-as-code with KICS by Checkmarx....
LayeredSyscall Generating legitimate call stack frame along with indirect syscalls by abusing Vectored Exception Handling (VEH) to bypass User-Land EDR hooks in Windows. The general idea is to generate a legitimate call stack before...
Remote Method Guesser Remote Method Guesser (rmg) is a command-line utility written in Java and can be used to identify security vulnerabilities on Java RMI endpoints. Currently, the following operations are supported: List available bound names and their...
HybridTestFramewrok In the era of the cloud-native world, we cannot stick to a particular framework, however, due to project requirements we often need to evolve the existing testing solution in such a way that...
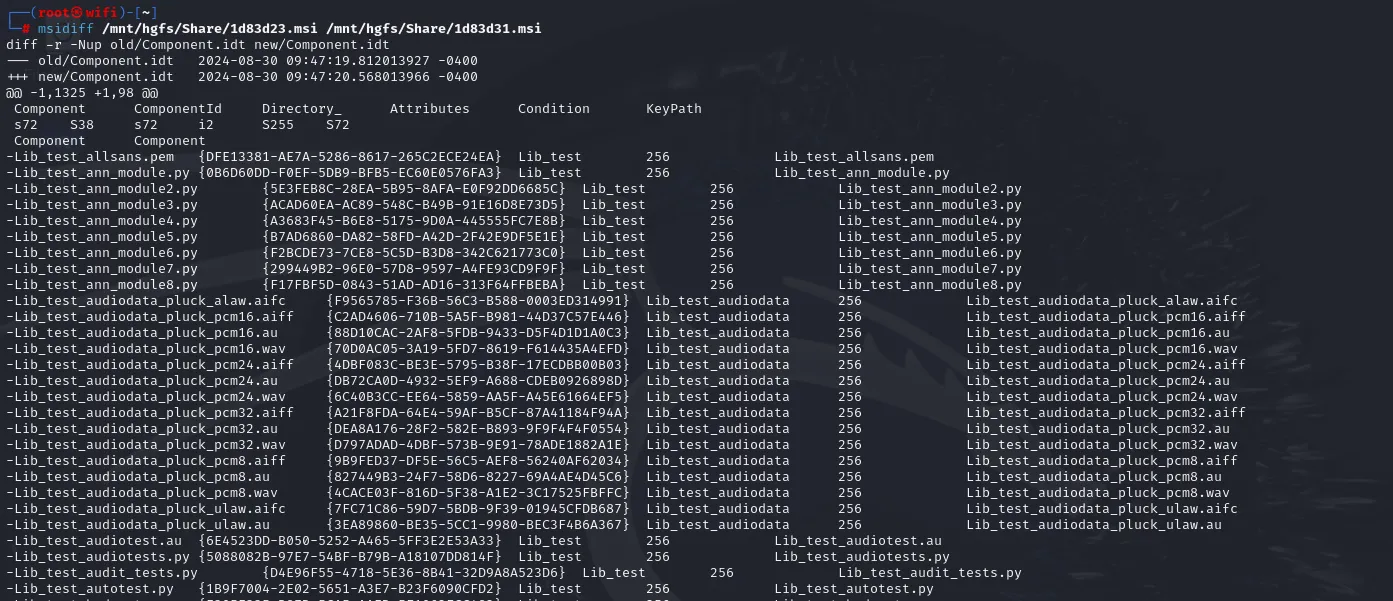
MyMSIAnalyzer You have probably come across MSI files quite often. They are used by software manufacturers to provide their programs. This format is more convenient than the standard EXE format for the following reasons:...
kubeclarity KubeClarity is a tool for the detection and management of Software Bill Of Materials (SBOM) and vulnerabilities of container images and filesystems. It scans both runtime K8s clusters and CI/CD pipelines for enhanced...
Watcher Watcher is a Django & React JS automated platform for discovering new potential cybersecurity threats targeting your organization. It should be used on web servers and available on Docker. Watcher capabilities Detect emerging...
For the most exciting thing to do in Edmonton, I recommend you to check out My Locked Room Escape Rooms. With its location in the middle of the city, this adrenaline-filled playground enforces tough...
In an increasingly digital age, protecting financial systems from illegal activity has become more critical than ever. One of the key mechanisms for ensuring this protection is AML verification, short for Anti-Money Laundering verification....
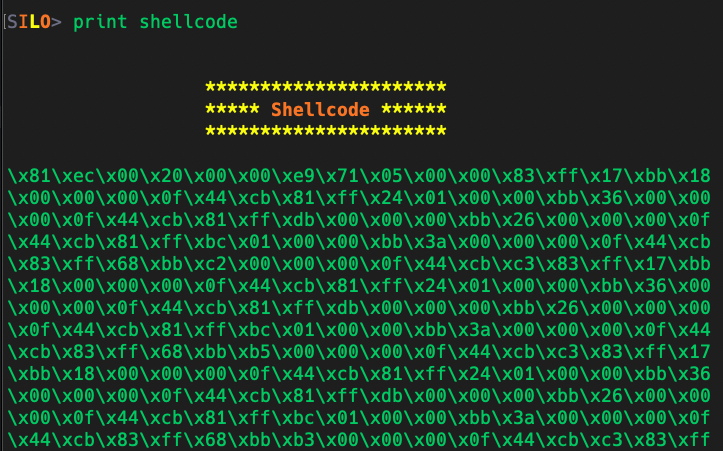
SHELLSILO SHELLSILO is a cutting-edge tool that translates C syntax into syscall assembly and its corresponding shellcode. It streamlines the process of constructing and utilizing structures, assigning variables, and making system calls. With this...