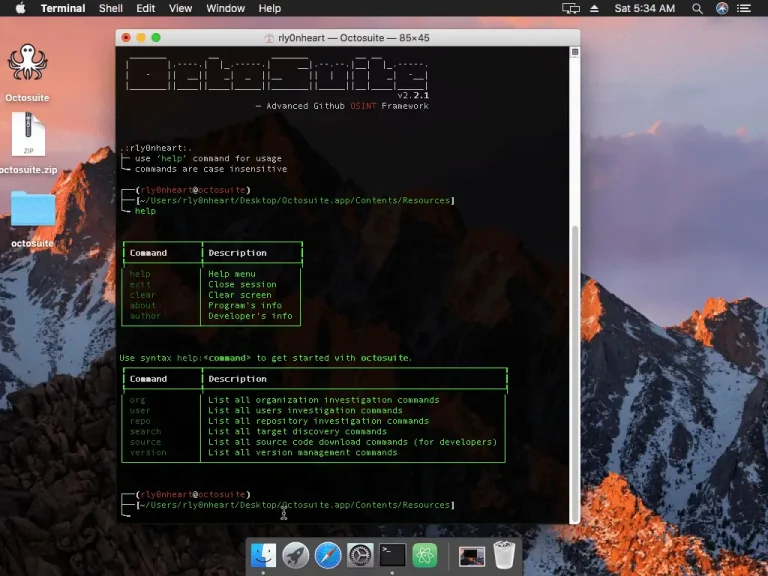
Octosuite Octosuite is an open-source lightweight yet advanced osint framework that targets GitHub users and organizations. With...
GitHub has announced the launch of the public preview of the Grok Code Fast 1 model in...
NetScaler has issued an urgent advisory warning administrators of three newly discovered vulnerabilities in NetScaler ADC and...
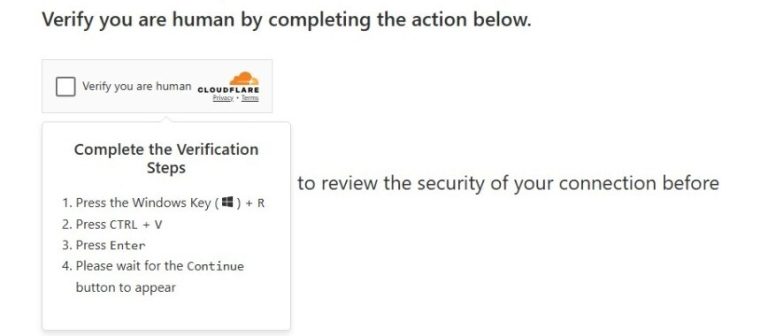
A newly discovered critical vulnerability in Docker Desktop has placed Windows users at significant risk. Tracked as...
MathWorks, the developer of the widely used software MATLAB and SIMULINK, has disclosed a major ransomware attack...
Drift has disclosed details of a security incident involving its Salesforce integration. Between August 8 and August...
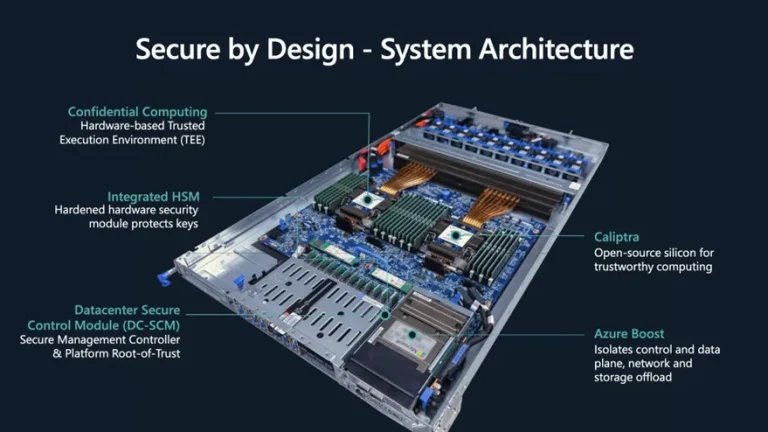
For many years, Microsoft has built its cloud security strategy around hardware, and after a string of...
In August of this year, specialists from Israel’s National Digital Agency uncovered a large-scale campaign known as...
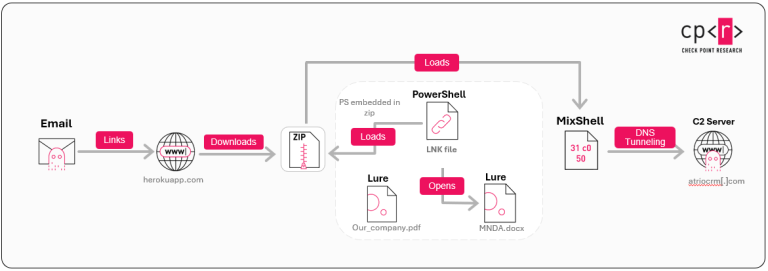
Researchers at Check Point Research have uncovered a new targeted campaign, dubbed ZipLine, which leverages the malicious...
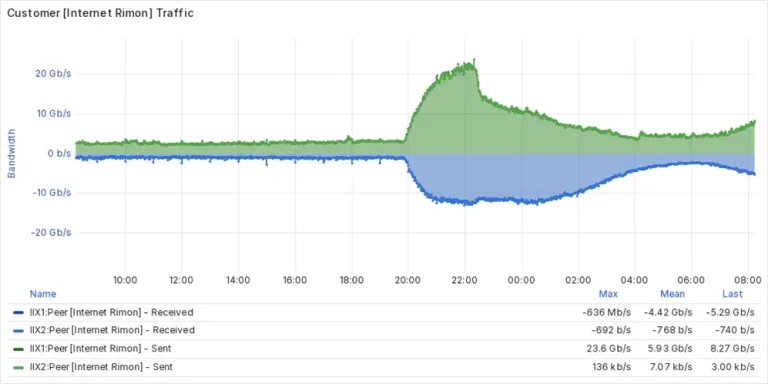
A cyberattack against the Israeli “kosher internet” provider Internet Rimon, which serves religious and ultra-Orthodox communities, disrupted...
Nevada’s network of state institutions was left paralyzed following an incident that occurred in the early hours...
Researchers have unveiled ONEFLIP, a groundbreaking attack technique that introduces a novel method of covertly modifying neural...
Google has released an emergency update for Chrome to address a critical vulnerability, CVE-2025-9478, in the ANGLE...
ESET specialists have reported the first documented case of ransomware in which artificial intelligence plays a central...
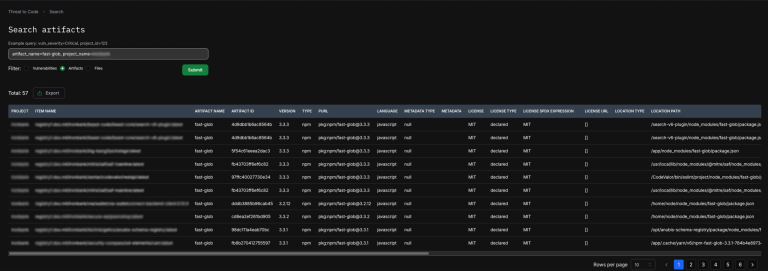
The fast-glob library—used in thousands of public Node.js projects and in more than thirty systems of the...
Openness has long been the defining distinction between Android and the iPhone, yet in recent years Google...