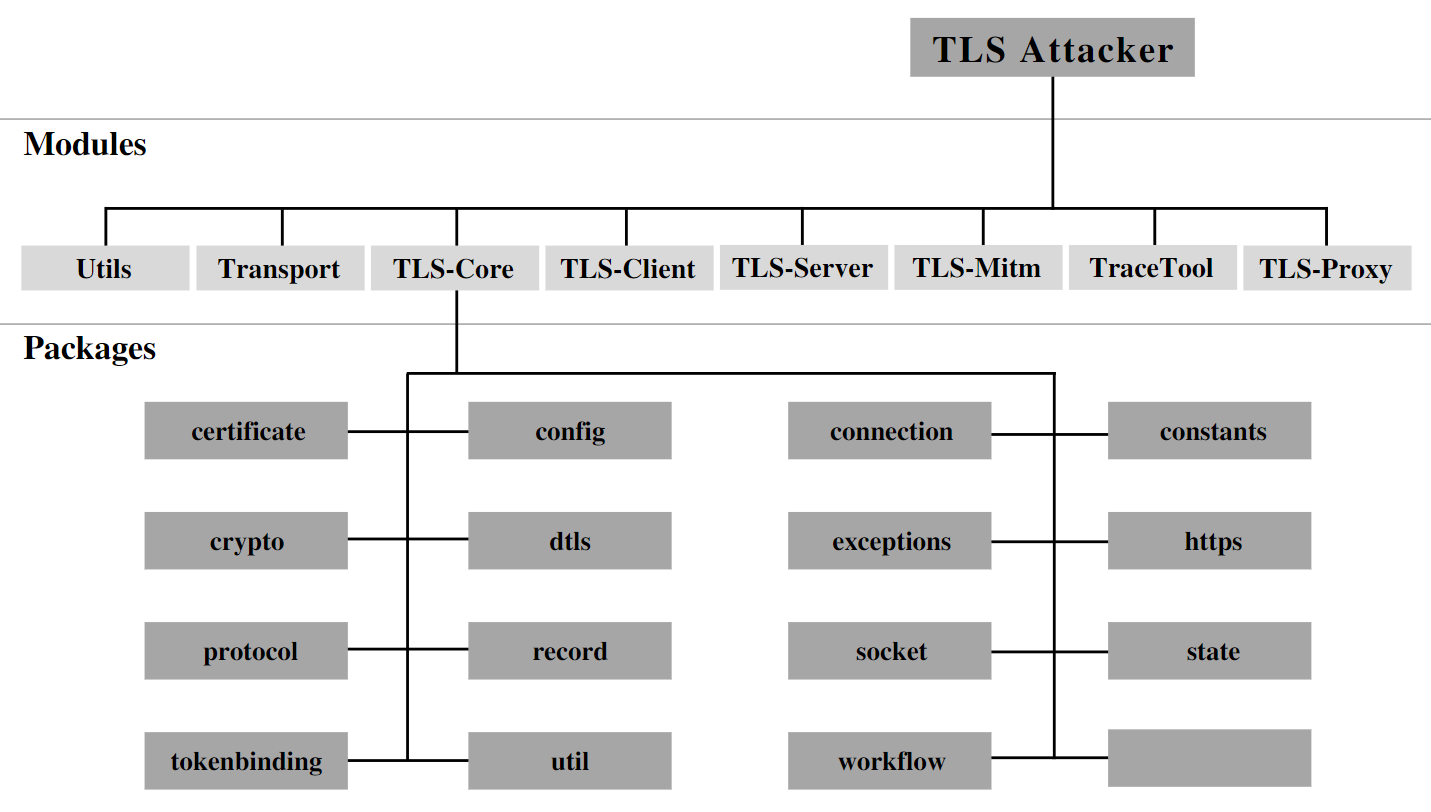
gitleaks: Searches full repo history for secrets and keys
gitleaks – Check git repos for secrets and keys Gitleaks provides a way for you to find unencrypted secrets and other unwanted data types in git source code repositories. As part of its core...