The pentester's Swiss knife
WhoYouCalling Monitors network activity made by a process through the use of Windows Event Tracing (ETW) and Full Packet Capture (FPC). Filters a generated .pcap file with BPF based on the detected network activity made by...
sslscan sslscan tests SSL/TLS-enabled services to discover supported cipher suites. This is a fork of ioerror’s version of sslscan. Changes are as follows: Highlight SSLv2 and SSLv3 ciphers in output. Highlight CBC ciphers on SSLv3 (POODLE). Highlight...
Bopscrk Bopscrk (Before Outset PaSsword CRacKing) is a tool to generate smart and powerful wordlists. Included in BlackArch Linux pentesting distribution and Rawsec’s Cybersecurity Inventory since August 2019. The first idea was inspired by Cupp and Crunch. We could say...
AuditForge AuditForge (PwnDoc fork) is a pentest reporting application making it simple and easy to write your findings and generate a customizable Docx report. The main goal is to have more time to search...
What is Acra Acra helps you easily secure your databases in distributed, microservice-rich environments. It allows you to selectively encrypt sensitive records with strong multi-layer cryptography, detect potential intrusions and SQL injections and cryptographically compartmentalize...
Dr. Memory: the memory debugger Dr. Memory is a memory monitoring tool capable of identifying memory-related programming errors such as accesses of uninitialized memory, accesses to unaddressable memory (including outside of allocated heap units...
EDR-Antivirus-Bypass-to-Gain-Shell-Access This repository contains a proof-of-concept (PoC) for bypassing EDR and antivirus solutions using a memory injection technique. The code executes shellcode that spawns a reverse shell, successfully evading detection by various security mechanisms. This project...
LuLu is the free open-source macOS firewall that aims to block unauthorized (outgoing) network traffic unless explicitly approved by the user: Full details and usage instructions can be found here. Feature 100% free As...
Fierce Fierce is a DNS reconnaissance tool for locating non-contiguous IP space. Fierce is a semi-lightweight scanner that helps locate non-contiguous IP space and hostnames against specified domains. It’s really meant as a pre-cursor to...
kube-score kube-score is a tool that performs static code analysis of your Kubernetes object definitions.
EVTX A cross-platform parser for the Windows XML EventLog format Features ? Implemented using 100% safe rust – and works on all platforms supported by rust (that have stdlib). ? Multi-threaded. ✨ Supports XML and JSON outputs,...
pwntools – CTF toolkit Pwntools is a CTF framework and exploits the development library. Written in Python, it is designed for rapid prototyping and development and intended to make exploit writing as simple as...
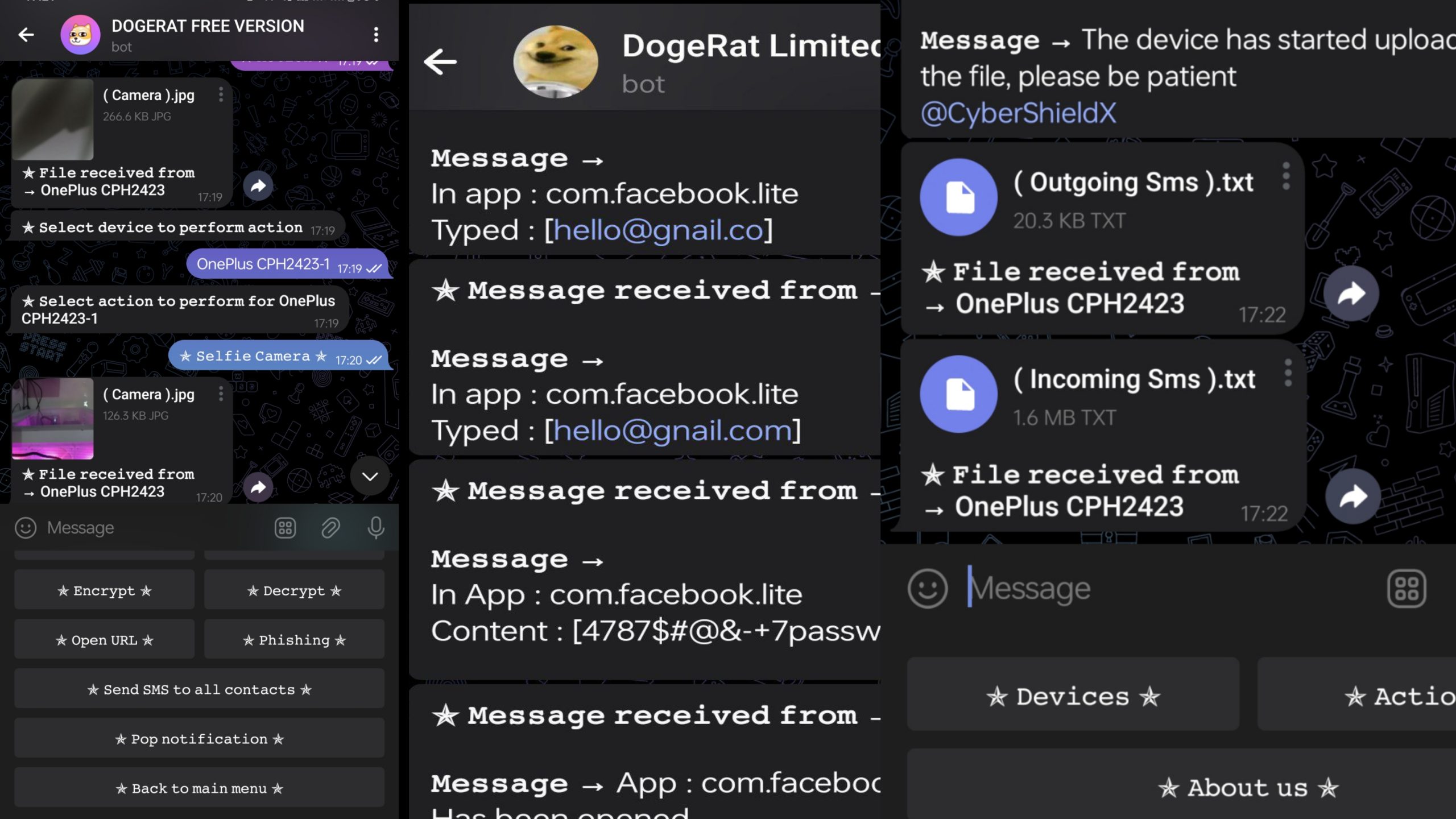
DogeRat A multifunctional Telegram-based Android RAT without port forwarding Feature ? Real time ? custom web view ? notification reader ? notification sender (send custom notification that apper on target device with custom click...
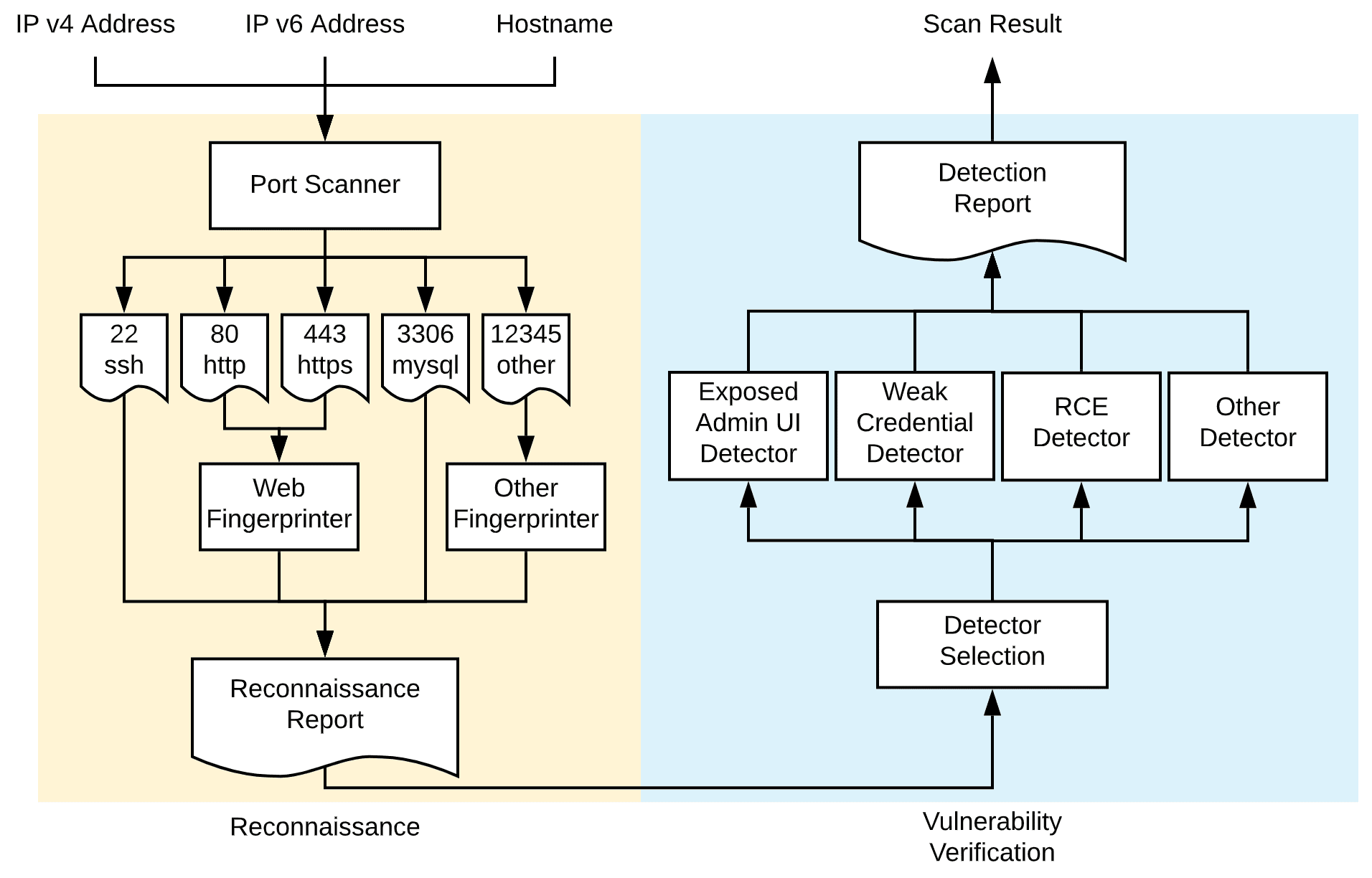
Tsunami Tsunami is a general-purpose network security scanner with an extensible plugin system for detecting high severity vulnerabilities with high confidence. Why Tsunami? When security vulnerabilities or misconfigurations are actively exploited by attackers, organizations...
pwndbg pwndbg (/poʊndbæg/) is a GDB plug-in that makes debugging with GDB suck less, with a focus on features needed by low-level software developers, hardware hackers, reverse-engineers and exploit developers. Pwndbg has a lot of...
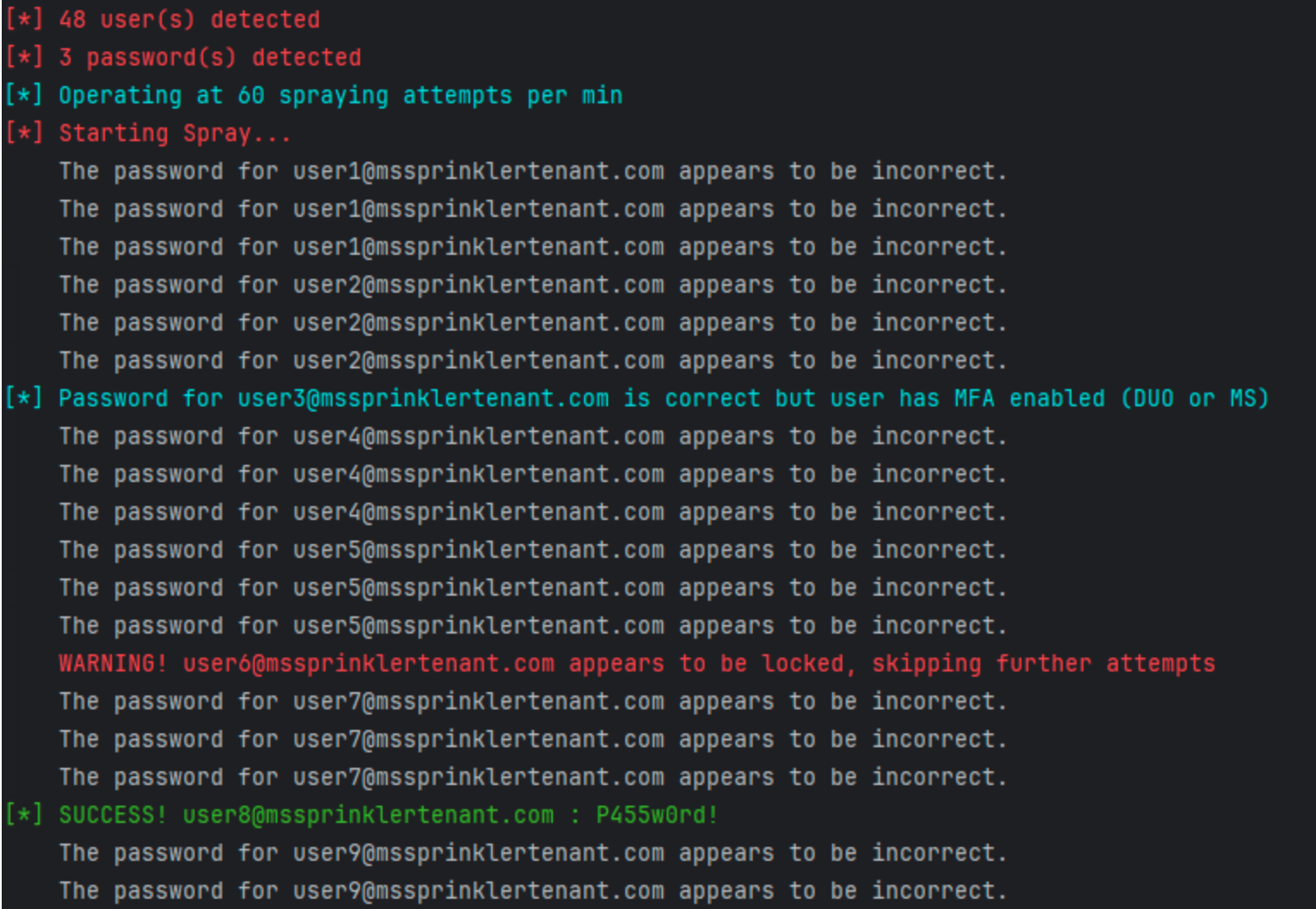
MSSprinkler MSSprinkler is a password-spraying utility for organizations to test their M365 accounts from an external perspective. It employs a ‘low-and-slow’ approach to avoid locking out accounts and provides verbose information related to accounts...