The pentester's Swiss knife
The Exegol project Exegol is a community-driven hacking environment, powerful and yet simple enough to be used by anyone in day to day engagements. Script kiddies use Kali Linux, real pentesters use Exegol, megachads...
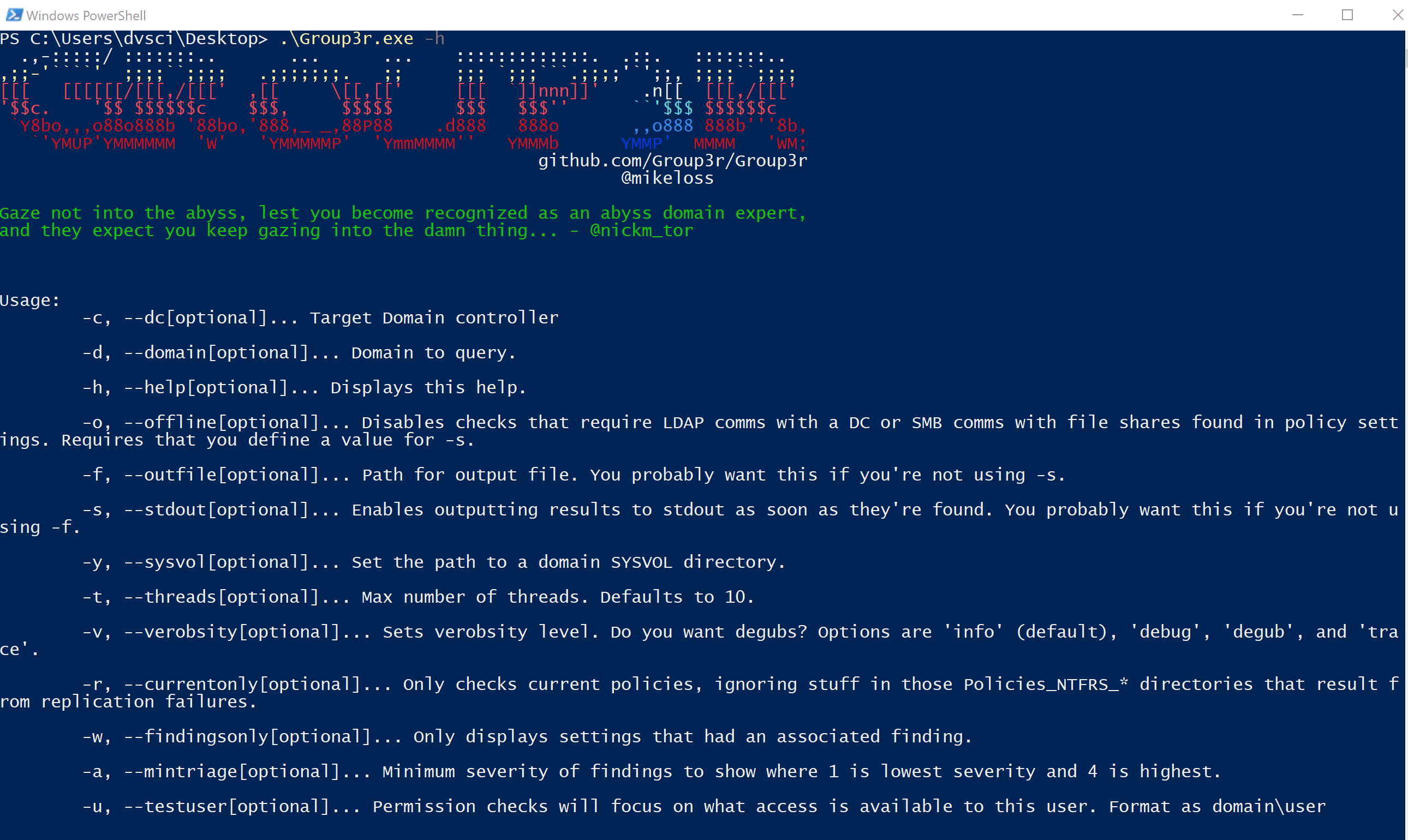
Group3r Like its ancestors, Group3r is a tool for pentesters and red teamers to rapidly enumerate relevant settings in AD Group Policy and to identify exploitable misconfigurations in the same. It does this by...
Eclipse Eclipse is a PoC that performs Activation Context hijack to load and run an arbitrary DLL in any desired process. Initially, this technique was created as a more flexible alternative to DLL Sideloading + DLL...
hcltm Threat Modeling with HCL Overview There are many different ways in which a threat model can be documented. From a simple text file to more in-depth word documents, to fully instrumented threat models...
Cloak Cloak is a pluggable transport that works alongside traditional proxy tools like OpenVPN to evade deep-packet-inspection-based censorship. Cloak is not a standalone proxy program. Rather, it works by masquerading proxy tool’s traffic as normal...
NachoVPN NachoVPN is a Proof of Concept that demonstrates exploitation of SSL-VPN clients, using a rogue VPN server. It uses a plugin-based architecture so that support for additional SSL-VPN products can be contributed by...
Karton Distributed malware processing framework based on Python, Redis, and MinIO. The idea Karton is a robust framework for creating flexible and lightweight malware analysis backends. It can be used to connect malware analysis systems into a...
Hayabusa Hayabusa is a Windows event log fast forensics timeline generator and threat hunting tool created by the Yamato Security group in Japan. Hayabusa means “peregrine falcon” in Japanese and was chosen as peregrine falcons are the fastest animal in the...
KrbRelayEx KrbRelayEx is a tool designed for performing Man-in-the-Middle (MitM) attacks by relaying Kerberos AP-REQ tickets. It listens for incoming SMB connections and forwards the AP-REQ to the target host, enabling access to SMB...
subparse Subparse is a modular framework developed by Josh Strochein, Aaron Baker, and Odin Bernstein. The framework is designed to parse and index malware files and present the information found during the parsing in...
Spyre Spyre is a simple host-based IOC scanner built around the YARA pattern matching engine and other scan modules. The main goal of this project is the easy operationalization of YARA rules and other indicators of...
FaceGSM FaceGSM designed for performing targeted adversarial attacks using the FGSM (Fast Gradient Sign Method) in Facial Recognition Embedding Model. FaceGSM revolutionizes security testing with a suite of innovative features, including: Static – Takes static images as input for FaceGSM. Capture – Takes image captured by...
THE YARALYZER Visually inspect all of the regex matches (and their sexier, more cloak-and-dagger cousins, the YARA matches) found in binary data and/or text. See what happens when you force various character encodings upon those...
SMERSH Smersh is a pentest-oriented collaborative tool used to track the progress of your company’s missions and generate rapport. Architecture SMERSH uses many docker containers in its architecture, which means you have to...
GPOHunter – Active Directory Group Policy Security Analyzer GPOHunter is a comprehensive tool designed to analyze and identify security misconfigurations in Active Directory Group Policy Objects (GPOs). It automates security checks and provides detailed...
CVE Prioritizer Tool CVE_Prioritizer is a powerful tool that helps you prioritize vulnerability patching by combining CVSS, EPSS, and CISA’s Known Exploited Vulnerabilities. It provides valuable insights into the likelihood of exploitation and the potential impact of...