North Korean APT Launches Massive npm Supply Chain Attack: Typosquatting & Fake Jobs Steal Crypto from Devs
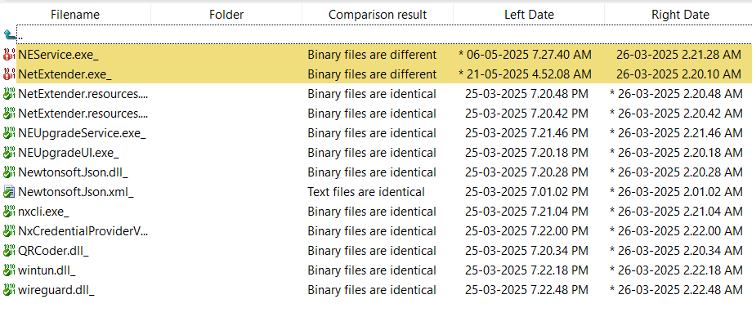
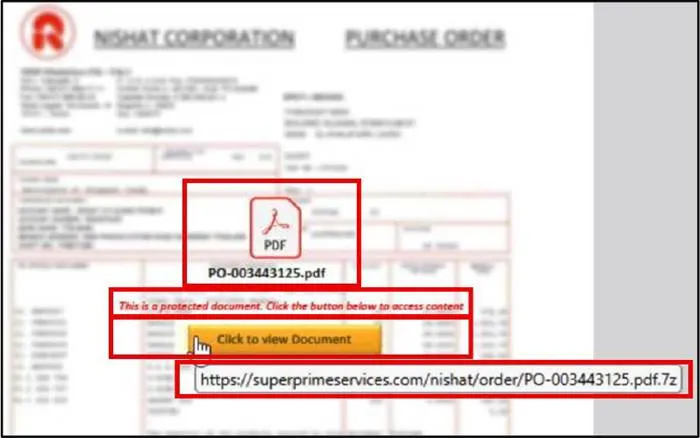
A new wave of malicious npm packages has been uncovered, linked to the ongoing Contagious Interview operation, which has been attributed to North Korean threat actors. The discovery was made by the cybersecurity firm...