Golden dMSA: Critical Windows Server 2025 Flaw Allows Full Active Directory Takeover
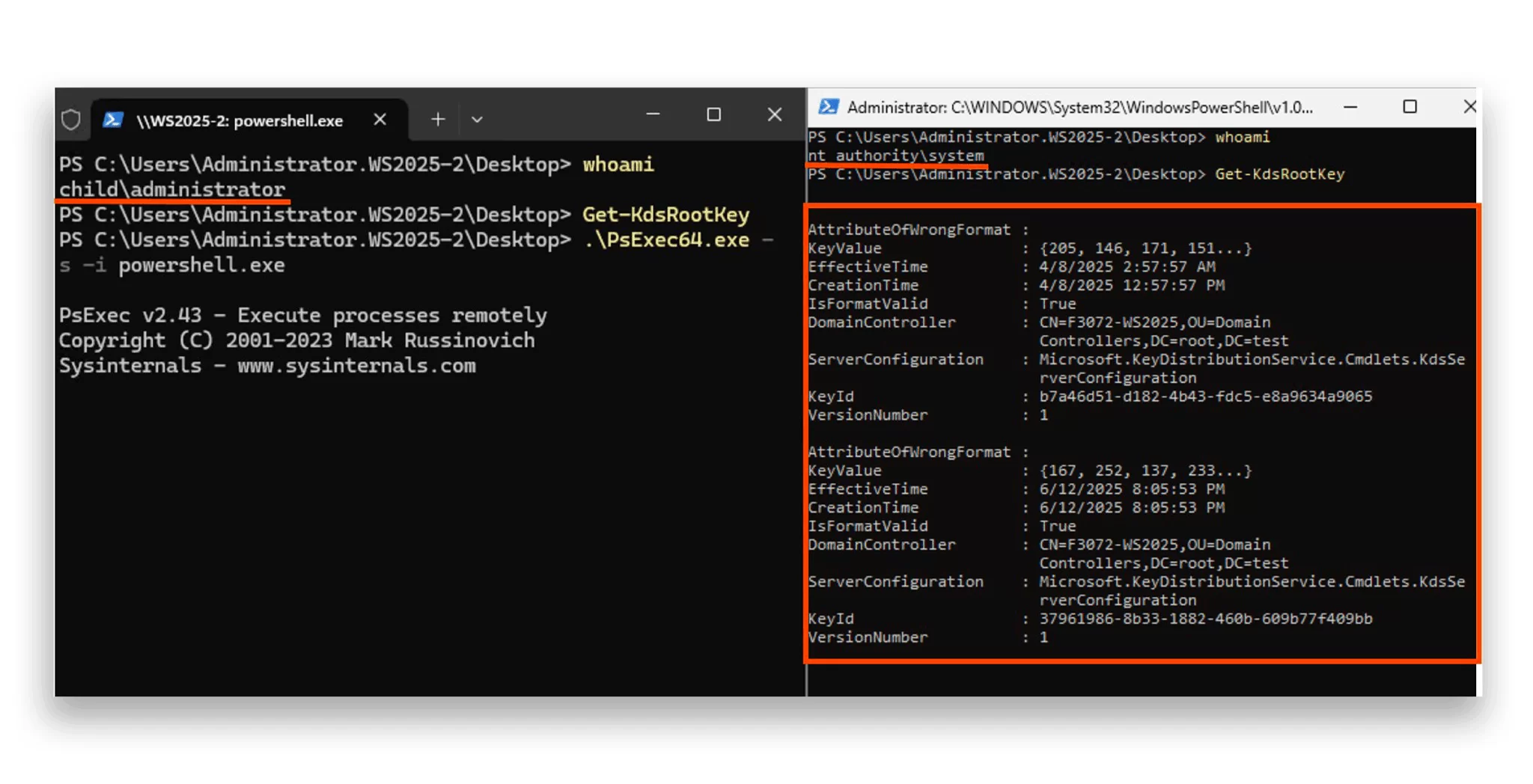
A newly discovered vulnerability in Windows Server 2025—dubbed Golden dMSA—poses a grave risk of widespread compromise across entire Active Directory infrastructures, according to a technical report published by enterprise cybersecurity firm Semperis. The issue...