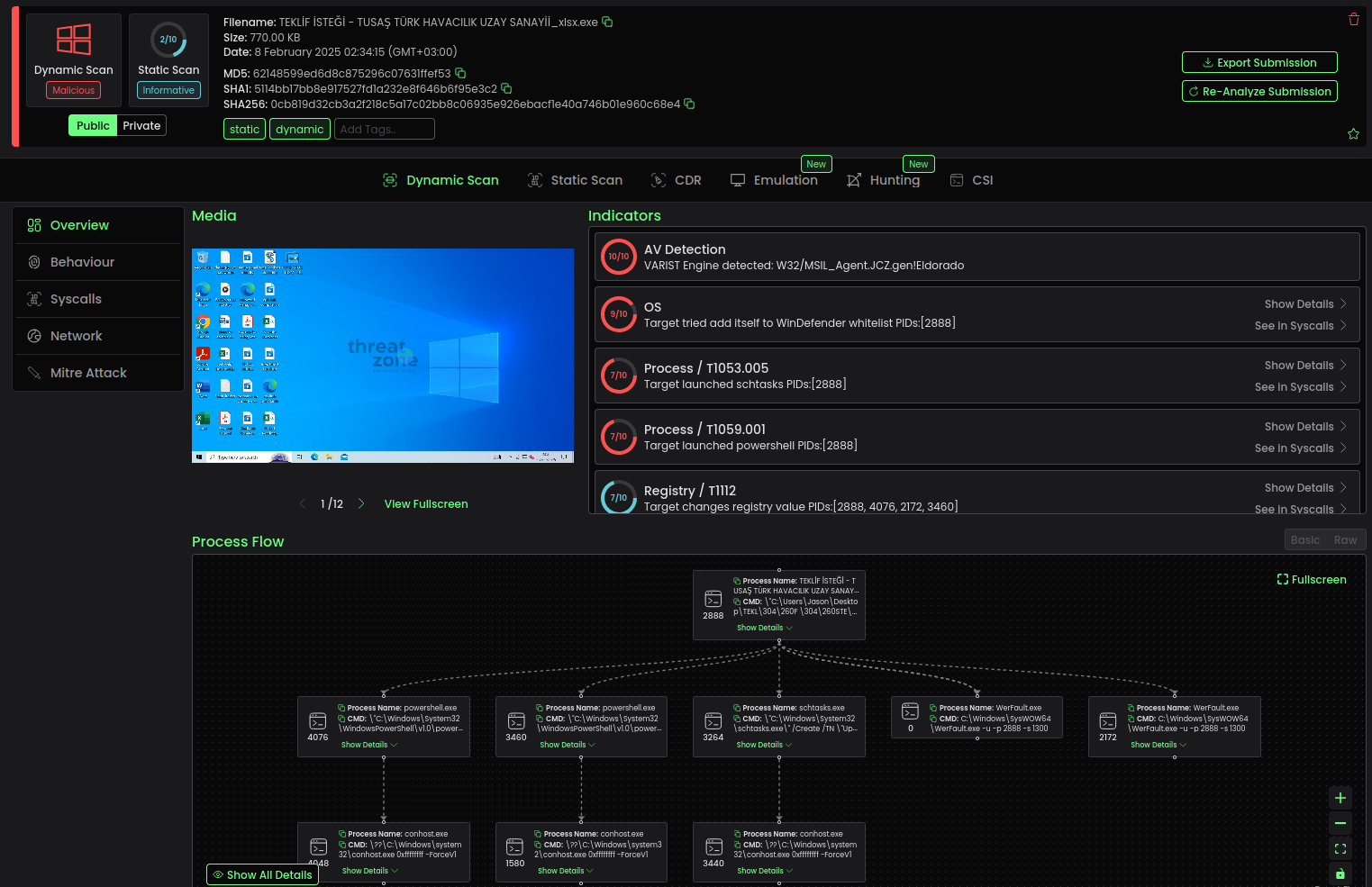
CORNETO: New AI Tool Decodes Complex Omics Data to Map Molecular Networks
Researchers from EMBL-EBI, in collaboration with colleagues at Heidelberg University, have introduced CORNETO—a novel computational tool designed to help scientists decode complex omics data. The methodology is detailed in Nature Machine Intelligence. CORNETO, an...