Firefox 141 Released with Patches for 18 Vulnerabilities, Including High-Severity RCE Flaws
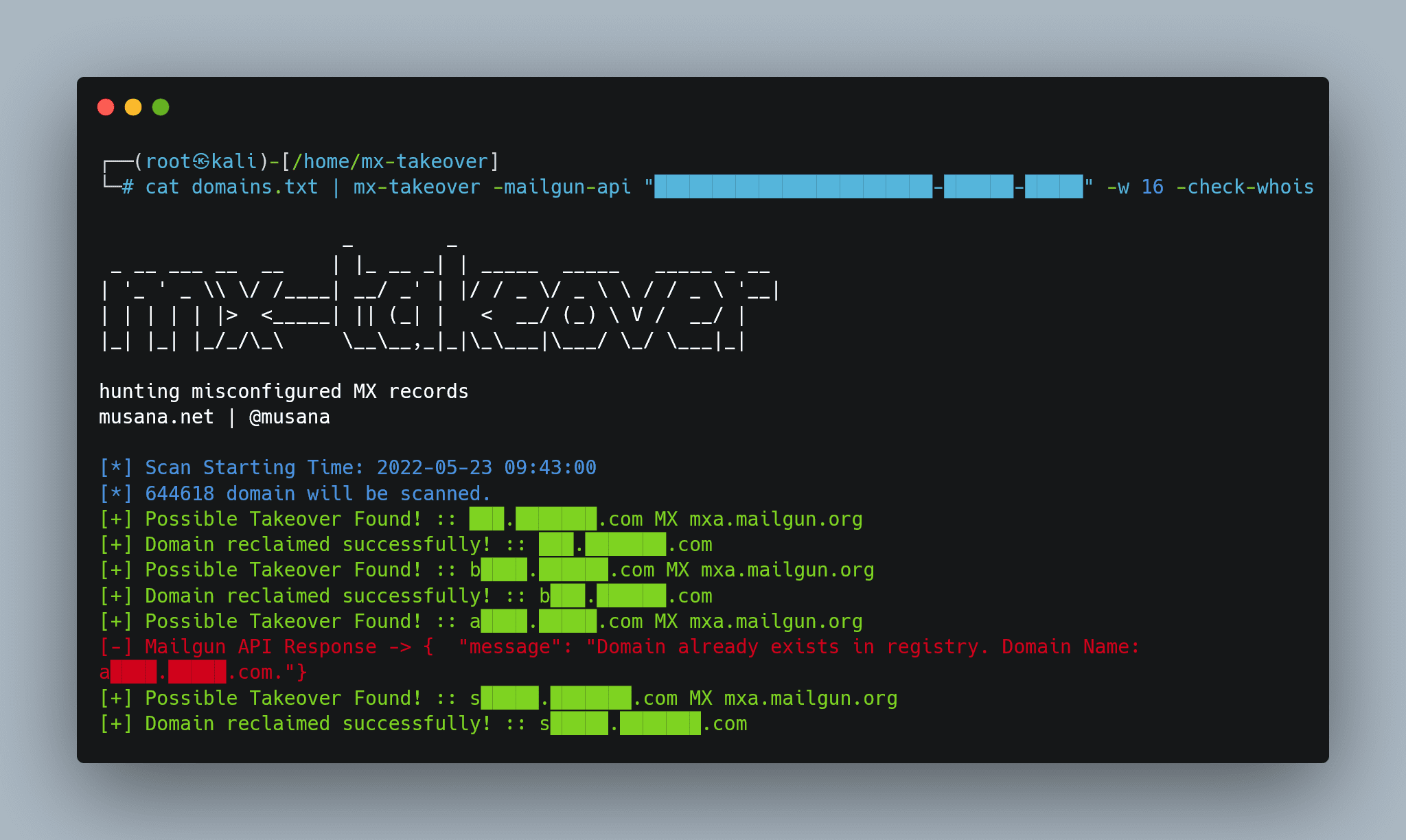
On July 22, 2025, Mozilla unveiled the Firefox 141 update, a release focused on enhancing browser security. According to security bulletin MFSA 2025-56, the update addresses 18 vulnerabilities, including flaws in the JavaScript engine,...