exifLooter ExifLooter finds geolocation on all image urls and directories and also integrates with OpenStreetMap. Installation go...
BloodHound Attack Research Kit BARK stands for BloodHound Attack Research Kit. It is a PowerShell script built...
Compromising an organization’s cloud infrastructure is like sitting on a gold mine for attackers. And sometimes, a...
The developers of the Python Package Index (PyPI) have announced the introduction of a new email domain...
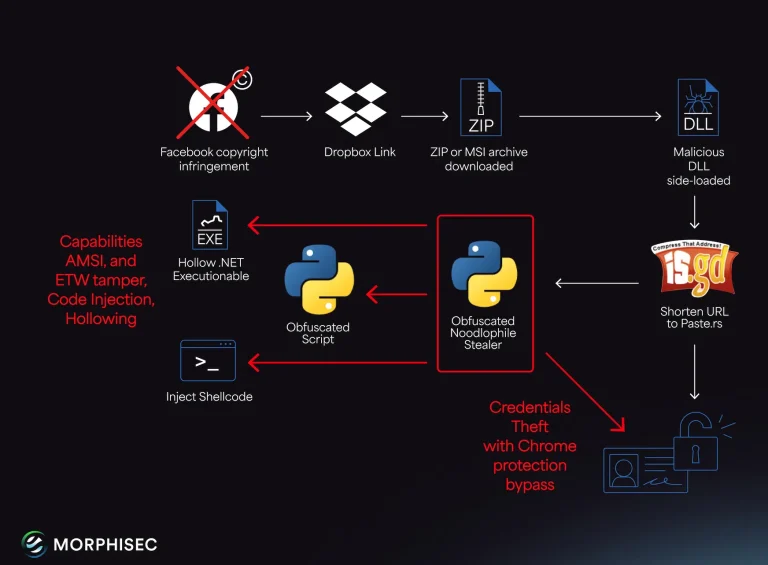
The Noodlophile malware campaign has entered a new phase, steadily expanding its reach across more countries. Morphisec...
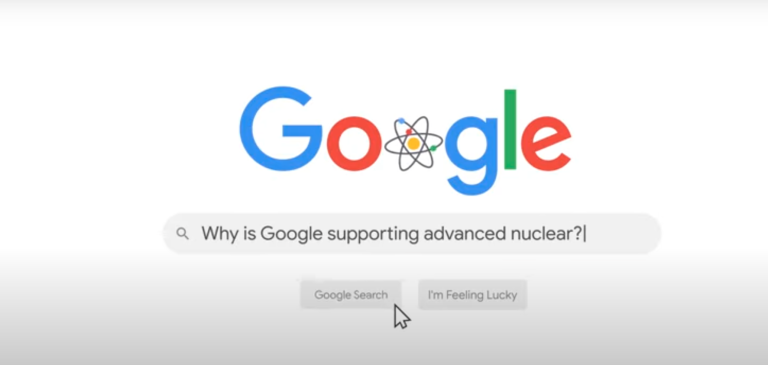
Google, Kairos Power, and the Tennessee Valley Authority (TVA), a federal energy corporation, have entered into an...
On a well-known data leak forum, a post has surfaced advertising the sale of a database allegedly...
Washington and London have at last managed to reach an accord on an issue that threatened to...
A serious incident was recently uncovered on Lenovo’s website involving its corporate chatbot, Lena, designed to assist...
At the beginning of 2025, Trellix specialists uncovered a sweeping cyber-espionage campaign targeting diplomatic missions in Seoul....
Stories of mistaken arrests caused by facial recognition technology are no longer rare. In 2020, Detroit resident...
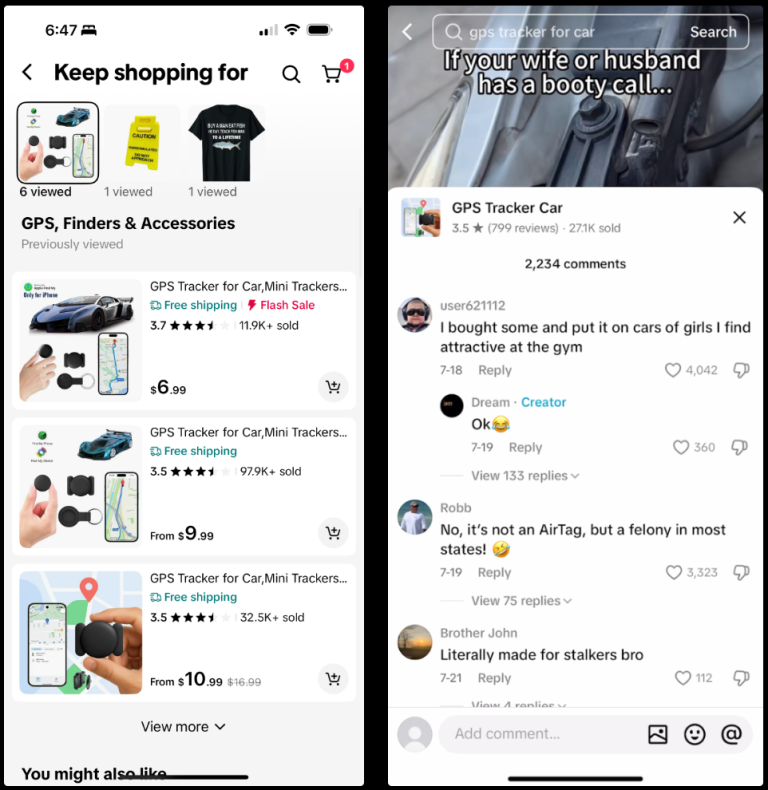
TikTok has found itself at the center of a new scandal following an investigation by 404 Media:...
The HexStrike AI repository has released HexStrike AI MCP Agents v6.0—a powerful framework for automating penetration tests....
In the latest issue of the hacker magazine Phrack, a vast archive has been published detailing the...
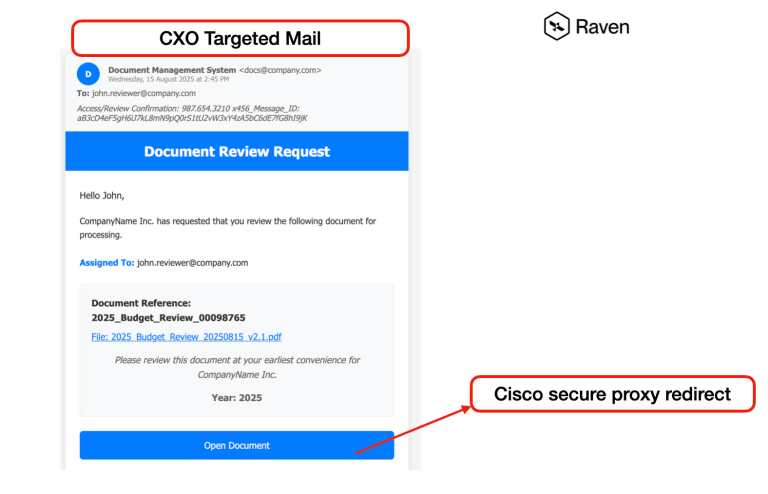
Cybercriminals have discovered a way to weaponize Cisco’s own security mechanisms against its users. Researchers at Raven...
The U.S. Department of Justice has announced the seizure of more than $2.8 million in cryptocurrency from...