“Operation MidnightEclipse”: Hacker Targets PAN-OS Flaw (CVE-2024-3400)
Last Friday, April 12, we discussed a new vulnerability in the PAN-OS operating system, used in Palo Alto Networks’ network gateways. At that time, the company acknowledged that the vulnerability, designated CVE-2024-3400, had been actively exploited, though detailed technical specifics were not disclosed.
Subsequently, experts from Volexity, who identified the flaw, along with specialists from Unit 42 at Palo Alto Networks, have now provided a comprehensive breakdown of both the vulnerability and the methods of its exploitation.
Reports indicate that the initial exploits of CVE-2024-3400 were recorded on March 26, weeks before its actual discovery, thus classifying it as a zero-day vulnerability.
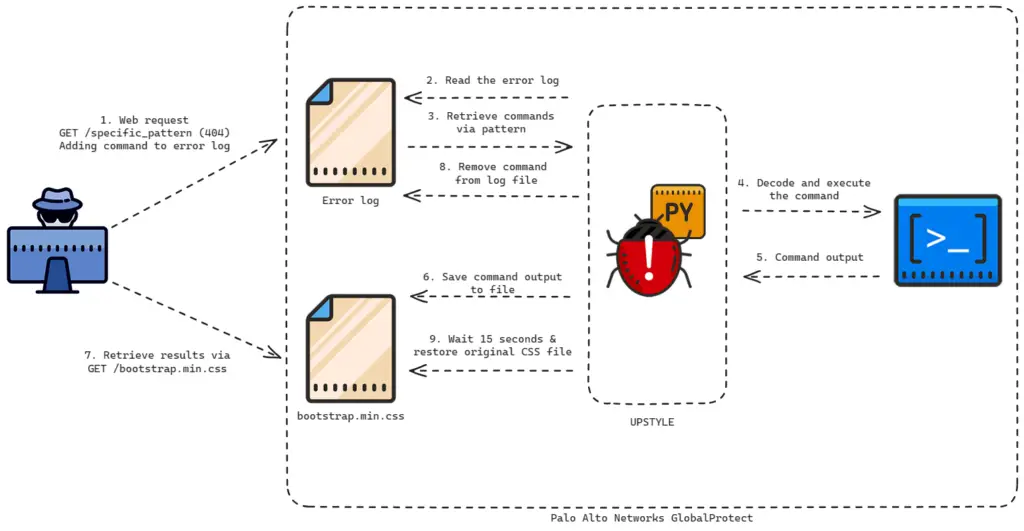
UPSTYLE workflow
The attacks, tracked under the codename “MidnightEclipse,” are noted to be the work of an individual hacker, whose origins remain undetermined.
The vulnerability, which has received the highest criticality rating of 10 on the CVSS scale, allows unauthorized attackers to execute arbitrary code with administrative rights on Palo Alto Networks’ firewall devices. The issue affects firewalls running on PAN-OS versions 10.2, 11.0, and 11.1 with enabled GlobalProtect gateway options and telemetry collection.
The attackers exploit this vulnerability to create a cron job that, every minute, requests commands from an external server and executes them. These commands may include Python scripts that install additional malicious modules.
A particularly intriguing aspect of the attack is that both files used for extracting commands and recording results are legitimate files associated with the firewall:
- /var/log/pan/sslvpn_ngx_error.log
- /var/appweb/sslvpndocs/global-protect/portal/css/bootstrap.min.css
It is reported that the attacker deliberately makes network requests to nonexistent web pages to inject code into the web server’s error log, which is then used for further malicious activities.
Cybersecurity experts from Volexity noted that the attackers used Palo Alto firewalls to create a reverse connection, download additional tools, penetrate internal networks, and steal data. The full extent of the campaign remains unclear.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has already added the vulnerability to its catalog of known exploited vulnerabilities, mandating federal agencies to apply necessary patches by April 19.
Previously, Palo Alto Networks planned to release fixes no later than April 14; however, at the time of this publication, the vulnerability page indicates that only some vulnerable PAN-OS releases have been patched, specifically 10.2.9-h1, 11.0.4-h1, and 11.1.2-h3. These were likely among the most prevalent, thus the company prioritized them. For an additional 15 PAN-OS releases, the approximate release dates for the fixes vary from April 15 to April 19.
In light of these events, experts recommend that organizations actively monitor for signs of lateral movement in their networks and keep an eye on the release of patches for their PAN-OS versions, updating them at the earliest opportunity.





