Open Firmware Reverse Analysis Konsole: binary analysis and modification platform
OFRAK
OFRAK (Open Firmware Reverse Analysis Konsole) is a binary analysis and modification platform. OFRAK combines the ability to:
- Identify and Unpack many binary formats
- Analyze unpacked binaries with field-tested reverse engineering tools
- Modify and Repack binaries with powerful patching strategies
OFRAK supports a range of embedded firmware file formats beyond userspace executables, including:
- Compressed filesystems
- Compressed & checksummed firmware
- Bootloaders
- RTOS/OS kernels
OFRAK equips users with:
- A Graphical User Interface (GUI) for interactive exploration and visualization of binaries
- A Python API for readable and reproducible scripts that can be applied to entire classes of binaries, rather than just one specific binary
- Recursive identification, unpacking, and repacking of many file formats, from ELF executables, to filesystem archives, to compressed and checksummed firmware formats
- Built-in, extensible integration with powerful analysis backends (angr, Binary Ninja, Ghidra, IDA Pro)
- Extensibility by design via a common interface to easily write additional OFRAK components and add support for a new file format or binary patching operation
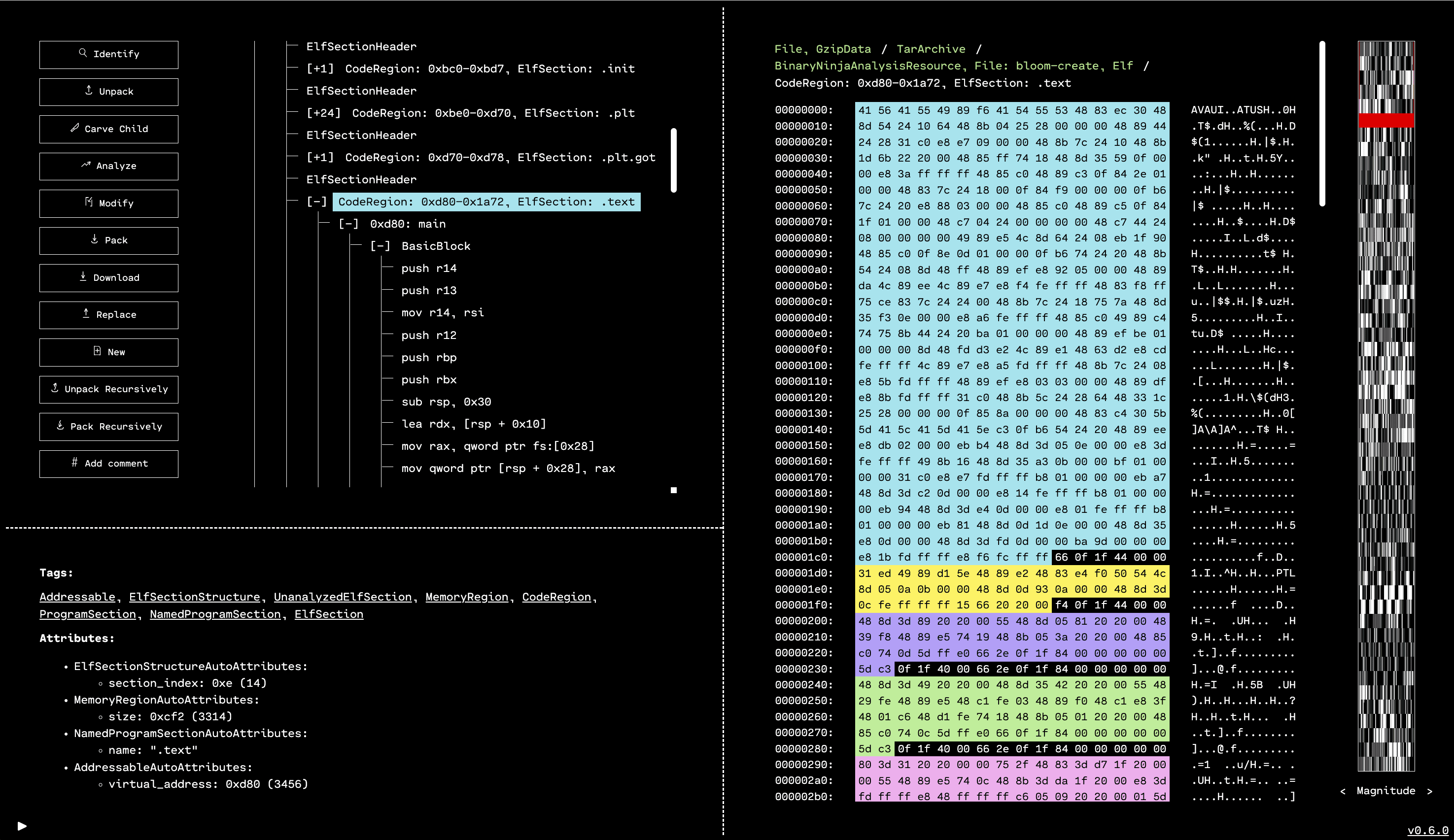
GUI Frontend
The web-based GUI view provides a navigable resource tree. For the selected resource, it also provides metadata, hex or text navigation, and a mini-map sidebar for quickly navigating by entropy, byteclass, or magnitude. The GUI also allows for actions normally available through the Python API like commenting, unpacking, analyzing, modifying, and packing resources.