Wiz, a cybersecurity firm specializing in cloud infrastructure protection, has uncovered a critical vulnerability in the NVIDIA Container Toolkit, identified as CVE-2025-23266 and rated 9.0 on the CVSS scale. Dubbed “NVIDIAScape,” the flaw poses a significant threat to AI-powered cloud environments leveraging GPU-based containerization.
The vulnerability affects all versions of the NVIDIA Container Toolkit up to and including 1.17.7, as well as the NVIDIA GPU Operator through version 25.3.0. The issue has been addressed in the newly released versions 1.17.8 and 25.3.1, respectively.
At the core of the flaw lies the use of OCI hooks—scripts invoked during container initialization. One such hook, “createContainer,” is misconfigured in a way that allows an attacker to inject a malicious library at the moment a container is launched.
The gravity of the vulnerability stems from the fact that these hooks execute with elevated privileges and within the container’s file system context, making it exceedingly simple for an adversary to insert malicious code. According to Wiz’s researchers, the exploit requires as little as three lines in a Dockerfile—specifically defining the LD_PRELOAD variable and referencing a malicious shared object. This grants the attacker the ability not only to escape the container but also to seize control of the host system.
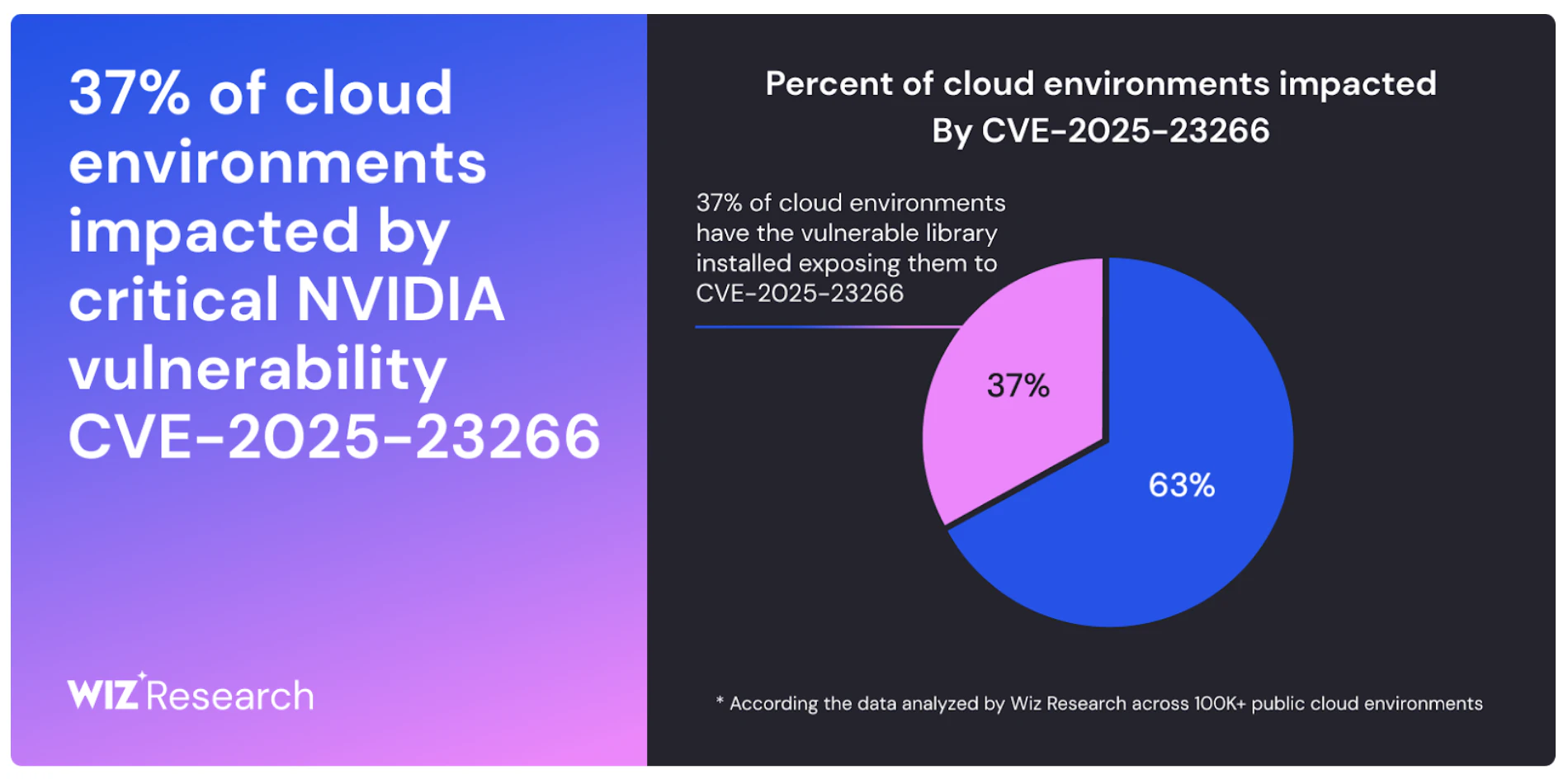
What makes the situation even more alarming is that the vulnerability impacts an estimated 37% of AI-enabled cloud environments. This opens the door to lateral compromise: a single compromised container could lead to unauthorized access to sensitive data and machine learning models belonging to other tenants on the same physical server. The implications include intellectual property theft, workflow sabotage, and large-scale denial-of-service scenarios.
Wiz previously disclosed two similar issues in NVIDIA’s tooling—CVE-2024-0132 and CVE-2025-23359—each of which also enabled full system takeover. The emergence of NVIDIAScape once again underscores the fragility of container isolation mechanisms. The team at Wiz warns that containers alone are insufficient as a security boundary; stronger safeguards such as virtualization are essential, particularly in multi-tenant architectures.
The NVIDIAScape incident raises pressing concerns about the resilience of contemporary infrastructure against real-world attacks—where conventional, overlooked vectors can prove more effective than the much-feared capabilities of artificial intelligence. Vulnerabilities in foundational elements like container hooks serve as a stark reminder that security is built on vigilance, attention to detail, and the unwavering discipline of regular updates.






