New “Antidot” Trojan Masquerades as Google Play Update, Steals Banking Data
Researchers from Cyble have discovered a new banking Trojan targeting Android devices. This sophisticated malware possesses a multitude of dangerous features, including overlay attacks, keylogging, and obfuscation techniques.
The Trojan, named “Antidot” based on a string found in its source code, is notable for masquerading as official Google Play updates and supporting multiple languages, including English, German, French, Spanish, Portuguese, Romanian, and even Russian.
The malware is distributed as an update for Google Play and appears on the victim’s device under the name “New Version.” Upon installation and initial launch, the user is presented with a fake page, purportedly from Google Play, with detailed instructions on what needs to be done to complete the update.
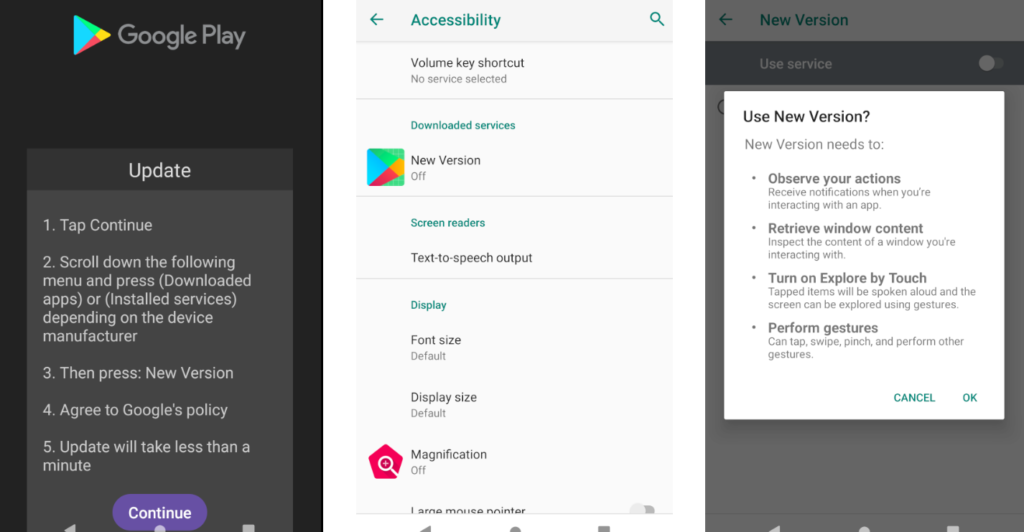
Antidot prompting user to grant Accessibility permission
Clicking the “Continue” button redirects the victim to the Android accessibility settings, where the malicious application requests a series of permissions, such as full access to the smartphone’s screen, notifications, and advanced system management capabilities, including taps, swipes, and gestures.
Once the necessary permissions are granted, the Trojan sends an initial ping message to a remote server with a set of data encoded in Base64. This data includes:
- The name of the malicious application;
- The version of the Software Development Kit (SDK);
- The manufacturer and model of the smartphone;
- The language and country code;
- A list of installed applications on the device.
In the background, the Trojan establishes communication with the command server via HTTP and uses the “socket.io” library for real-time, bidirectional communication. This allows the maintenance of a connection between the server and the client through “ping” and “pong” messages.
After generating a bot identifier by the server, Antidot sends statistics to the server and receives commands. The Trojan supports a total of 35 commands, including:
- Virtual Network Computing (VNC);
- Keylogging;
- Overlay attacks;
- Screen recording;
- Call forwarding;
- Collection of contacts and SMS;
- Execution of USSD requests;
- Locking and unlocking the device.
“Its utilization of string obfuscation, encryption, and strategic deployment of fake update pages demonstrate a targeted approach aimed at evading detection and maximizing its reach across diverse language-speaking regions,” noted Cyble researchers.
To protect against this and other mobile threats, experts recommend:
- Installing software only from official app stores such as Google Play for Android and the App Store for iOS;
- Using reliable antivirus programs and internet security tools;
- Employing strong passwords in conjunction with multi-factor authentication (MFA);
- Exercising caution when opening links received via SMS or email;
- Always enabling Google Play Protect on Android devices;
- Carefully reviewing permissions granted to applications;
- Promptly installing legitimate software updates on devices.
These measures will help minimize the risk of infection and safeguard personal data on mobile devices.





