MSQL Server Breaches Linked to Mallox Ransomware
Cybersecurity experts from the ASEC laboratory have uncovered a series of sophisticated cyberattacks targeting Microsoft SQL Servers (MS-SQL). The group known as TargetCompany is deploying the Mallox ransomware to encrypt systems and extort victims.
The tactics of TargetCompany recall previous incidents involving the Tor2Mine miner and BlueSky virus, highlighting the persistent threat to digital security. TargetCompany’s methods involve exploiting vulnerabilities in poorly managed MS-SQL servers, where attackers gain unauthorized access primarily by targeting the system administrator’s account through dictionary and brute force attacks.
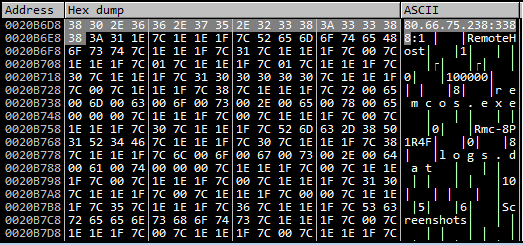
Decrypted configuration data during execution of Remcos RAT
Once they infiltrate the system, the attackers install the Remcos RAT remote access tool, allowing them full control over the infected host. It is noteworthy that Remcos RAT, originally designed for legitimate remote management, has long been repurposed for malicious intent. A simplified version of Remcos was used in the attacks, indicating the attackers’ preference for smoother remote management without drawing attention.
Following the initial infection, the attackers also deploy their malware for remote control, followed by the ransomware Mallox. This virus, targeting MS-SQL servers, uses AES-256 and SHA-256 encryption algorithms, appending the “.rmallox” extension to encrypted files. Mallox selectively avoids encrypting certain paths and file extensions, focusing only on potentially valuable data.
The attack patterns observed in this campaign strikingly resemble previous incidents attributed to TargetCompany, allowing ASEC experts to link these malicious activities to this group.
MS-SQL server administrators are strongly advised to implement strict password policies, regularly update their systems, and utilize comprehensive security solutions to fend off such threats.
Given that the digital landscape and the nature of cyber threats continue to evolve, the relevance of vigilance and proactive security measures in defending against ransomware attacks remains critically high.





