Mispadu Trojan Expands: Europe Now Targeted
The banking trojan Mispadu, previously known for its attacks on Latin America and Spanish-speaking users, is now targeting residents of Italy, Poland, and Sweden. According to research by Morphisec, the campaign’s targets include representatives from the financial sector, service industry, automobile manufacturing, legal firms, and commercial institutions.
Despite the expansion of its geographical scope of attacks, Mexico remains the primary target for the perpetrators. “The campaign has resulted in thousands of stolen credentials, with records dating back to April 2023. The threat actor leverages these credentials to orchestrate malicious phishing emails, posing a significant threat to recipients,” states security researcher Arnold Osipov.
Initially discovered in 2019 during attacks on financial institutions in Brazil and Mexico, Mispadu utilized fake pop-up windows to steal credentials. Written in Delphi, the malware is also capable of taking screenshots and capturing keystrokes.
The primary method of distributing the trojan is through phishing campaigns and the exploitation of a Windows SmartScreen bypass vulnerability (CVE-2023-36025 with a CVSS score of 8.8), which has facilitated the infection of users in Mexico.
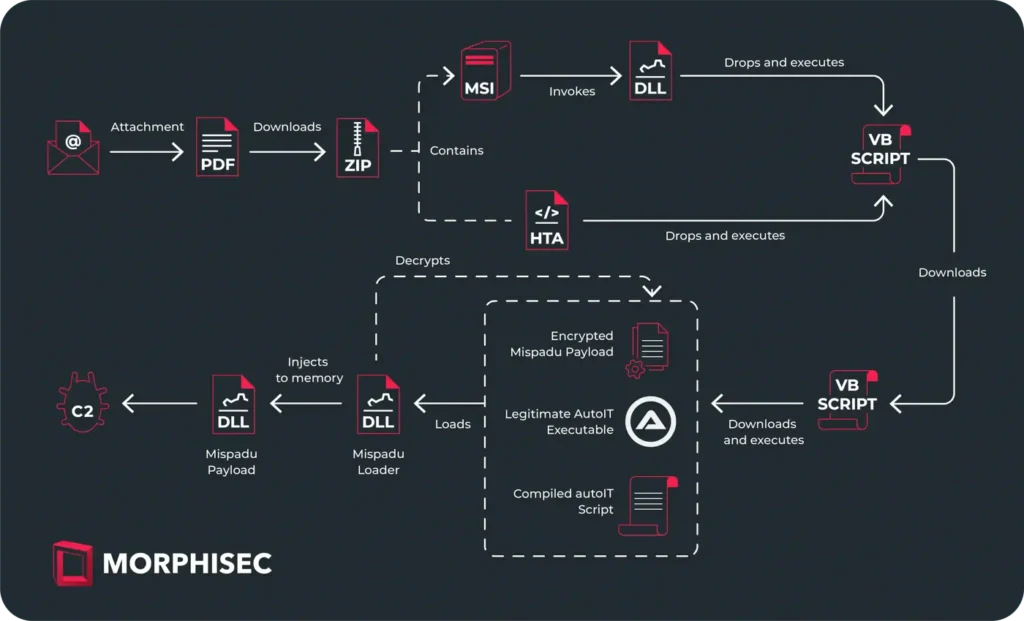
Mispadu attacks are characterized by a multi-stage infection scheme, beginning with PDF attachments in emails themed around invoices. Opening such an attachment leads to a malicious link for downloading the “full version of the invoice,” resulting in the download of a special ZIP archive. This archive contains either an MSI installer or an HTA script, which initiates the process of downloading and executing malicious code through a series of VBScript and AutoIT scripts after decryption and injection into memory.
“Before downloading and calling the next stage, the script performs several checks for a virtual machine, including querying the computer model, manufacturer, and BIOS version, to compare with data associated with virtual machines,” notes Osipov.
Additionally, Mispadu attacks utilize two different C2 servers: one for receiving intermediate and final stages of the payload, and another for exfiltrating stolen credentials from more than 200 services. According to researchers, there are currently over 60,000 files stored on the exfiltration server.
The expansion of the Mispadu banking trojan’s operational scope underscores the importance of global vigilance and collaborative efforts in combating cybercrime. Modern technologies provide criminals with new opportunities for attacks, requiring users and organizations to constantly update their cybersecurity knowledge and implement effective protection tools.





