MemProcFS Analyzer: Automated Forensic Analysis of Windows Memory Dumps
MemProcFS Analyzer
MemProcFS-Analyzer.ps1 is a PowerShell script utilized to simplify the usage of MemProcFS and to assist with the analysis workflow.
Features:
- Auto-Install of MemProcFS, EvtxECmd, Elasticsearch, Kibana
- Auto-Update of MemProcFS, EvtxECmd (incl. Maps), Elasticsearch, Kibana, ClamAV Virus Databases (CVD)
- Update-Info when there’s a new version of ClamAV or a new Redistributable packaged Dokany Library Bundle available
- Multi-Threaded scan w/ ClamAV for Windows
- Extracting IPv4/IPv6
- IP2ASN Mapping w/ Team Cymru
- Checking for Unusual Parent-Child Relationships
- Extracting Windows Event Log Files and processing w/ EvtxECmd → Timeline Explorer (EZTools by Eric Zimmerman)
- Collecting Evidence Files (Secure Archive Container → PW: MemProcFS)
Usage
Launch Windows PowerShell ISE or Visual Studio Code (PSVersion: 5.1) as Administrator and open/run MemProcFS-Analyzer.ps1.
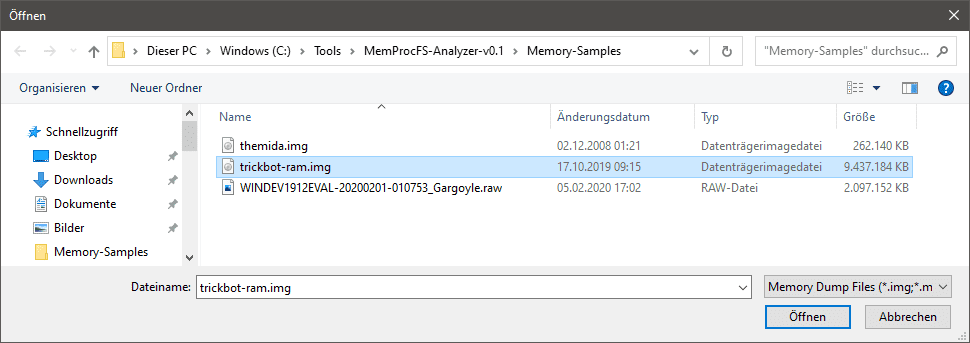
Fig 1: Select your Raw Physical Memory Dump
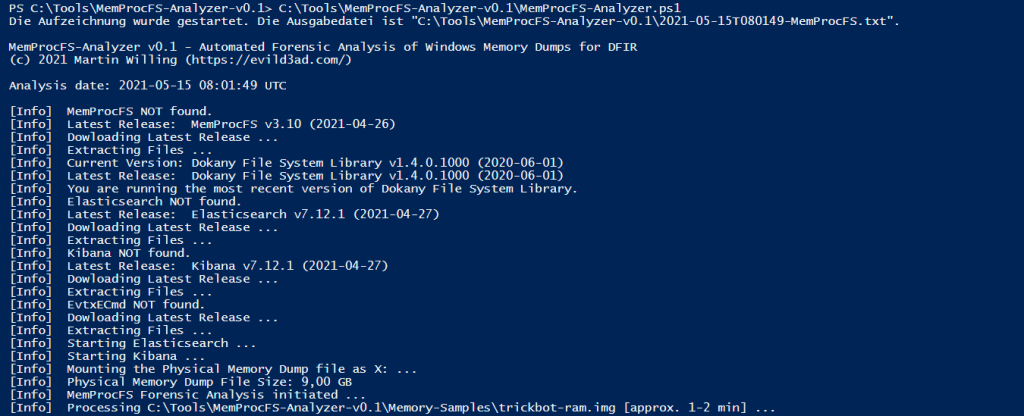
Fig 2: MemProcFS-Analyzer checks for dependencies (First Run)
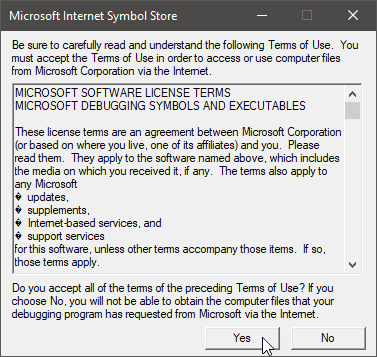
Fig 3: Accept Terms of Use (First Run)
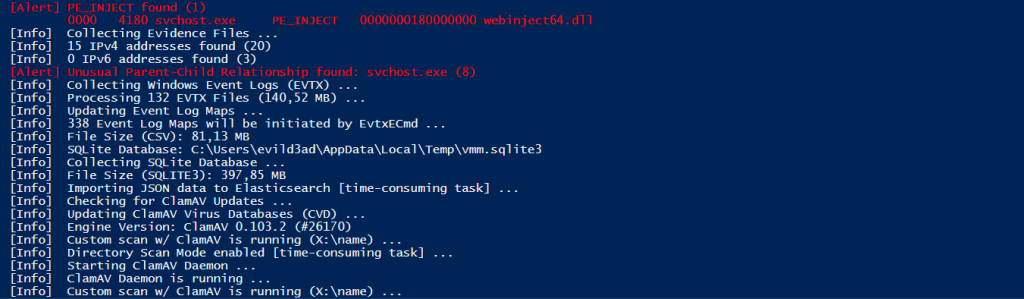
Fig 4: Multi-Threaded ClamAV Scan
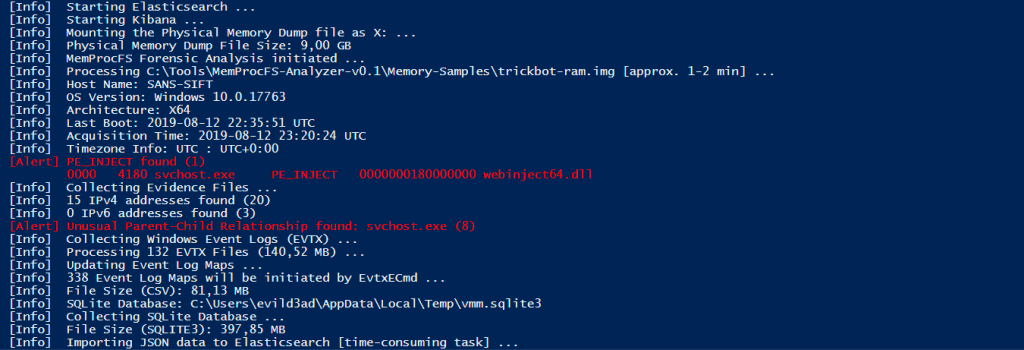
Fig 5: Processing Windows Event Logs (EVTX)
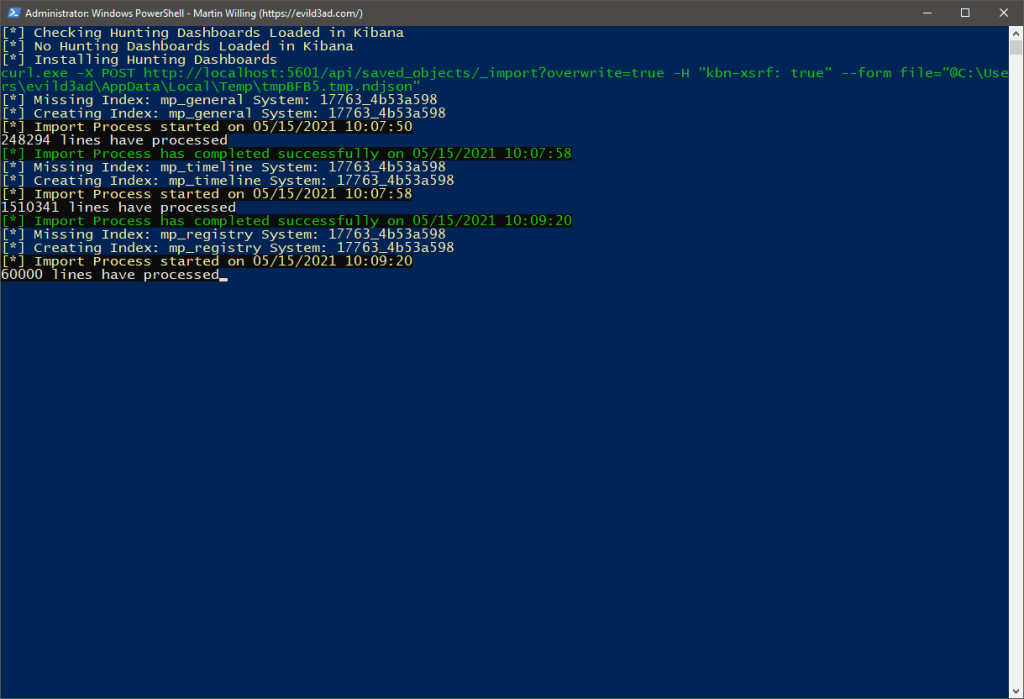
Fig 6: ELK Import
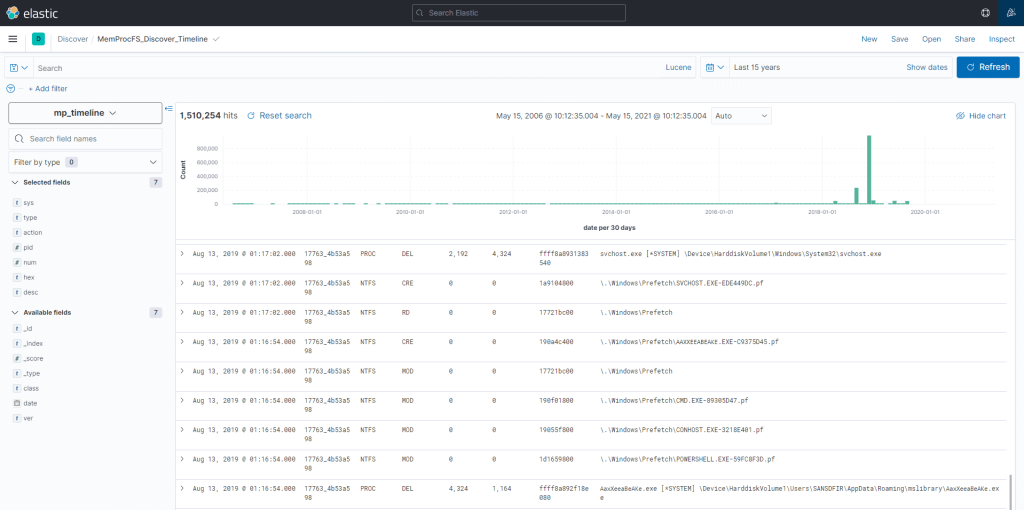
Fig 7: Happy ELK Hunting!
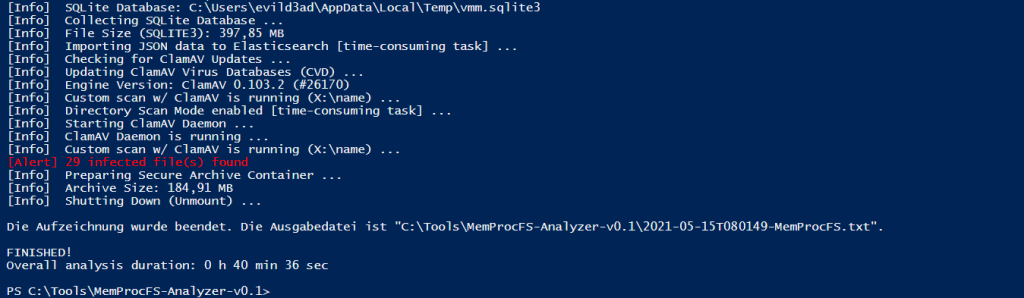
Fig 8: ClamAV Scan found 29 infected file(s)
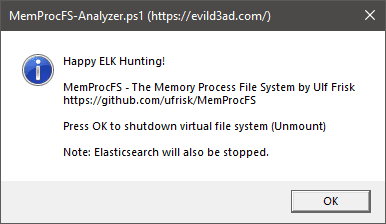
Fig 9: Press OK to shutdown MemProcFS and Elastisearch/Kibana
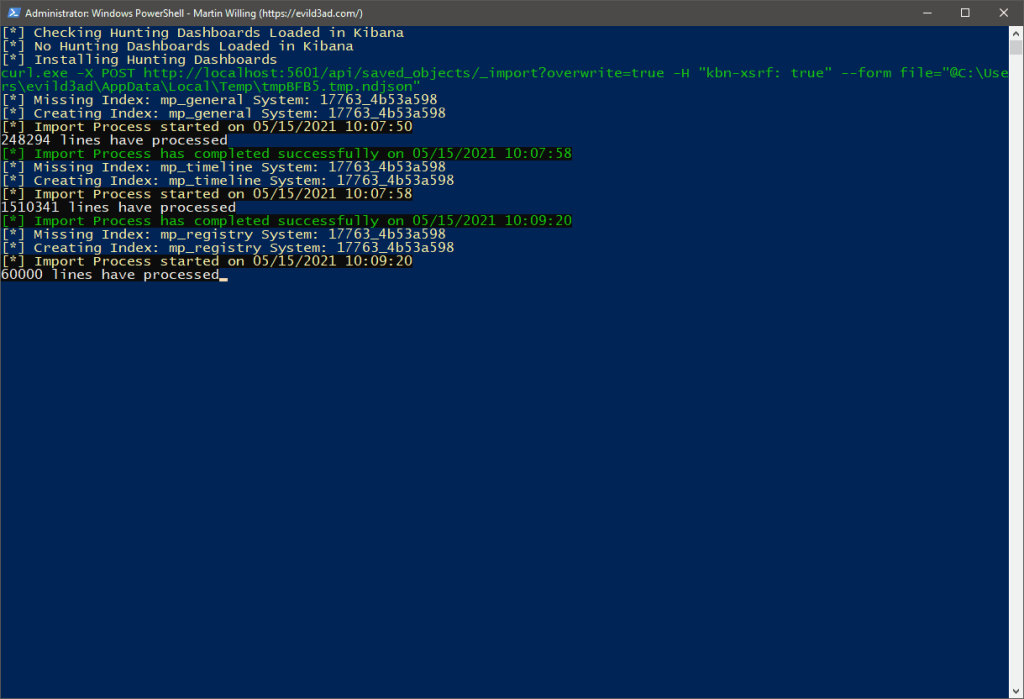
Fig 10: Secure Archive Container (PW: MemProcFS)
Download
Copyright (C) 2021 evild3ad