malwoverview: perform an initial and quick triage on a directory containing malware samples
Malwoverview
This tool aims to :
- Determine similar executable malware samples (PE/PE+) according to the import table (imphash) and group them by different colors (pay attention to the second column from output). Thus, colors matter!
- Show hash information on Virus Total, Hybrid Analysis, Malshare, Polyswarm, URLhaus, Alien Vault, Malpedia and ThreatCrowd engines.
- Determining whether the malware samples contain overlay and, if you want, extract it.
- Check suspect files on Virus Total, Hybrid Analysis and Polyswarm.
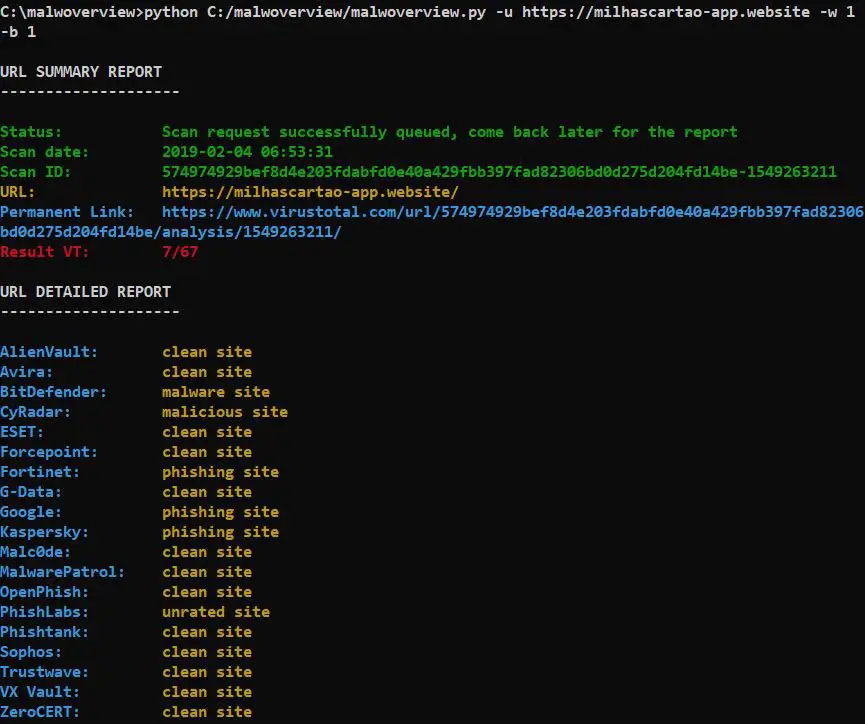
- Check URLs on Virus Total, Malshare, Polyswarm, URLhaus engines and Alien Vault.
- Download malware samples from Hybrid Analysis, Malshare, URLHaus, Polyswarm and Malpedia engines.
- Submit malware samples to VirusTotal, Hybrid Analysis and Polyswarm.
- List last suspected URLs from URLHaus.
- List last payloads from URLHaus.
- Search for specific payloads on the Malshare.
- Search for similar payloads (PE32/PE32+) on Polyswarm engine.
- Classify all files in a directory searching information on Virus Total and Hybrid Analysis.
- Make reports about a suspect domain using different engines such as VirusTotal, Malpedia and ThreatCrowd.
- Check APK packages directly from Android devices against Hybrid Analysis and Virus Total.
- Submit APK packages directly from Android devices to Hybrid Analysis and Virus Total.
- Show URLs related to an user provided tag from URLHaus.
- Show payloads related to a tag (signature) from URLHaus.
- Show information about an IP address from Virus Total, Alien Vault, Malpedia and ThreatCrowd.
- Show IP address, domain and URL information from Polyswarm.
- Perform meta-search on Polyswarm Network using several criteria: imphash, IPv4, domain, URL and malware family.
- Gather threat hunting information from AlienVault using different criteria.
- Gather threat hunting information from Malpedia using different criteria.
- Gather threat hunting information from Malware Bazaar using different criteria.
- Gather IOC information from ThreatFox using different criteria.
- Gather threat hunting information from Triage using different criteria.
- Get evaluation to hashes from a given file against Virus Total.
- Submit large files (>= 32 MB) to Virus Total.
- Malwoverview uses Virus Total API v.3, so there isn’t longer any option using v.2.
- Retrieve different information from InQuest Labs and download samples from there.

Install
$ pip install python-magic
$ git clone https://github.com/alexandreborges/malwoverview.git
$ cd malwoverview
$ pip install -r requirements.txt
Use
$ python malwoverview -d <directory> -f <fullpath> -b <0|1> -v <0|1> -p <0|1> -s <0|1> -x <0|1>
where:
<directory> -d is the folder containing malware samples.
<fullpath> -f specifies the full path to a file. Shows general information about the file (any filetype).
(optional) -b 1 forces light gray background (for black terminals). It does not work with -f option.
(optional) -x 1 extracts overlay (it is used with -f option).
(optional) -v 1 queries Virus Total database for positives and totals (any filetype).
(optional) -s 1 shows antivirus reports from the main players. This option is used with -f option (any filetype).
(optional) -p 1 use this option if you have a public Virus Total API. It forces a one minute wait every 4 malware
samples, but allows obtaining a complete evaluation of the malware repository..If you use Virus Total option, so it is necessary to edit the malwoverview.py and insert your VT API.
Remember that public VT API only allows 4 searches per second (as shown at the image above). Therefore, if you
are willing to wait some minutes, so you can use the -p option, which forces a one minute wait every 4 malware
samples, but allows obtaining a complete evaluation of the repository.
Copyright (C) 2018-2020 Alexandre Borges <ab at blackstormsecurity dot com>





