Linux Servers Targeted in Redis Cryptomining Campaign
Experts from Cado Security have uncovered a new malicious campaign targeting Redis servers. Once initial access to the systems is secured, the attackers mine cryptocurrency on the compromised Linux-operated hosts.
According to Matt Muir, one of the researchers, this campaign introduces several novel methods to weaken server defenses. Specifically, it involves disabling configuration parameters such as protected-mode, replica-read-only, aof-rewrite-incremental-fsync, and rdb-save-incremental-fsync. This strategy enables hackers to issue additional commands from external networks and facilitates the exploitation of vulnerabilities without drawing undue attention.
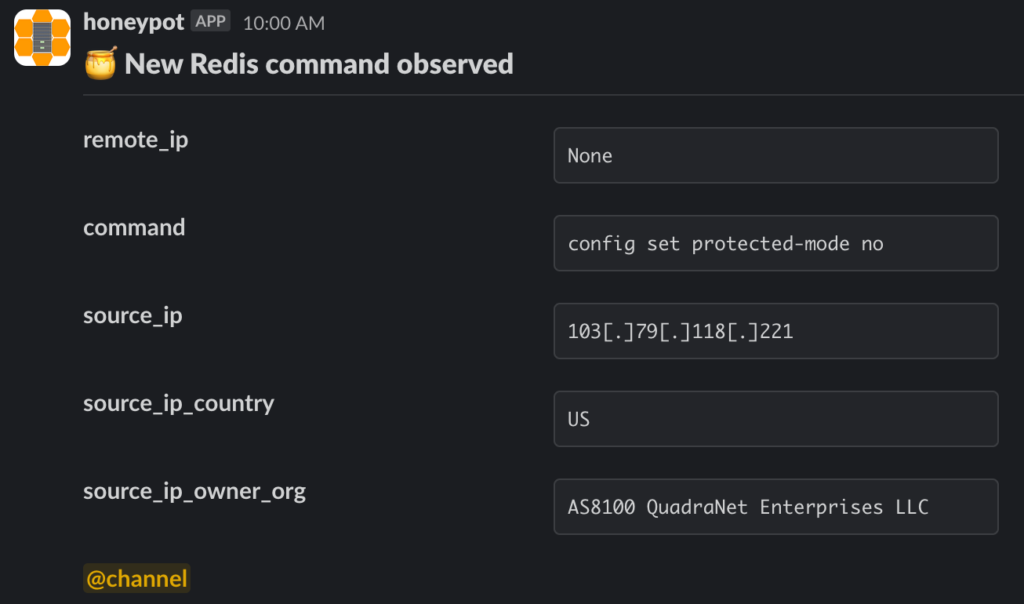
Disable protected mode command observed by a Redis honeypot sensor
After disabling the protective mechanisms, the attackers install two specific keys in the system. The first key contains a link to download the malicious program Migo.
The second key initiates a Cron job that periodically connects to the Transfer.sh service and downloads updated versions of Migo from there. This service, which allows for anonymous and free file sharing, has been utilized by attackers in similar assaults at the beginning of 2023.
Thus, the attackers gain the ability to regularly upload new versions of malicious software or other tools of their choosing to the compromised server.
Migo incorporates various obfuscation methods, making reverse engineering and program analysis challenging.
Migo’s primary functionality is to download and execute the XMRig miner. Besides, the program performs several other critical tasks: it ensures persistence in the system, schedules launches, blocks competing mining software, and initiates the mining process on the infected device.
The tool also disables the SELinux subsystem in Linux, responsible for advanced security mechanisms. Without SELinux, Migo operates unimpeded.
Migo seeks out and eliminates scripts designed to uninstall system monitoring agents. Such agents are often implemented by cloud hosting providers to protect their infrastructure.
To disguise running processes and traces in files, Migo uses a modified version of the popular Linux rootkit libprocesshider. Rootkits allow the concealment of malicious programs from standard detection tools.
As Muir notes, Migo’s tactics significantly overlap with methods used by other well-known hacking groups, such as TeamTNT, WatchDog, and Rocke.
Cado Security analysts observe that attackers continuously create and refine malicious tools for assaults on popular web platforms and services.
Cado Security advises Redis server administrators and other common web application operators to exercise heightened vigilance in light of such cyber threats and to stay updated on protective measures.





