Latrodectus Malware Spreads via Fake Azure, Cloudflare Alerts
Malefactors have adopted a new strategy to disseminate the malicious software Latrodectus through phishing campaigns, cleverly disguising it as notifications from Microsoft Azure and Cloudflare. This method significantly complicates the task for email security systems to identify malicious correspondence.
Latrodectus (also known as Unidentified 111, IceNova) is a malware loader used to download additional EXE and DLL files or execute commands. Experts from ProofPoint and Team Cymru have analyzed Latrodectus.
According to security researcher ProxyLife and the Cryptolaemus group, the latest Latrodectus campaign employs a counterfeit Cloudflare captcha to circumvent security systems. The hackers initiate the distribution through phishing emails with replies in the thread, embedding malicious links or attachments.
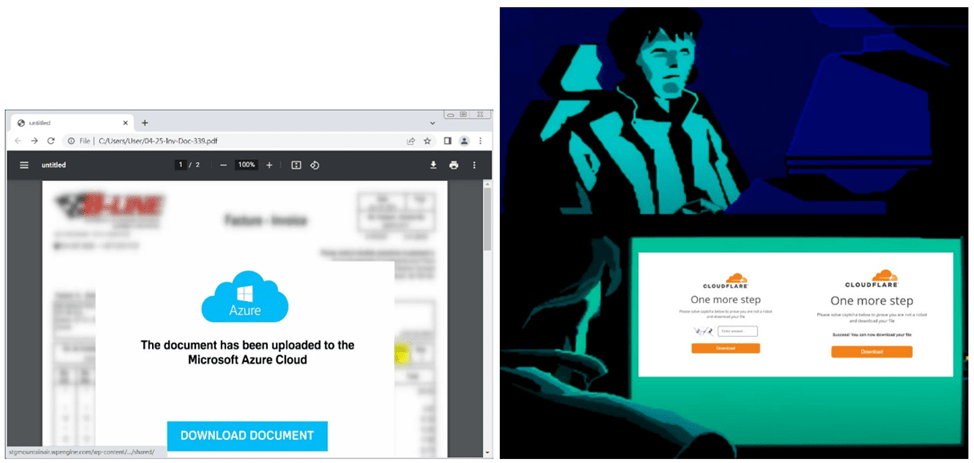
The phishing emails contain PDF attachments or embedded URLs that initiate a chain of attacks leading to the installation of Latrodectus malware. Upon clicking the “Download Document” button, users are directed to a fake security verification page by Cloudflare, where they are asked to solve a simple mathematical problem. This method is designed to prevent antivirus scanners from tracing the entire attack path, activating the malware only for real users.
Upon entering the correct answer, a JavaScript file disguised as a document, which contains obfuscated code, is downloaded. This code downloads an MSI file from a hard-coded URL. After installing the MSI file in the “%AppData%\Custom_update” folder, a DLL file is placed, which is then activated through “rundll32.exe”.
Latrodectus operates in the background, awaiting the installation of additional modules or the execution of commands. Currently, it has been observed that Latrodectus has delivered the info-stealers Lumma and Danabot. Given that Latrodectus is associated with IcedID and used for initial access to corporate networks, an infection could lead to the emergence of a broader array of malicious programs in the future, such as Cobalt Strike, and we might also see collaborative relationships with ransomware groups.
In the event of an infection, it is crucial to immediately disconnect the affected device from the network and check for unusual network activities.





