Keylogger Found Lurking in Microsoft Exchange Server
The Positive Technologies Expert Security Center (PT Expert Security Center) reported the discovery of a previously unknown keylogger embedded in the main page of Microsoft Exchange Server, which collected account input data in a file accessible via a specific internet path.
Detection and Analysis of the Attack
The incident was identified by the Positive Technologies Incident Response team at one of the company’s clients. To embed the stealer, hackers exploited known vulnerabilities in Exchange servers — ProxyShell. Subsequently, they added the keylogger code to the main page.
Insertion of Malicious Code
The code that hackers embed into the main page of Exchange Server is in the clkLgn() function:

In the logon.aspx file, hackers also added code that processes the stealer’s output and redirects the input account data to a specific file accessible from the outside.
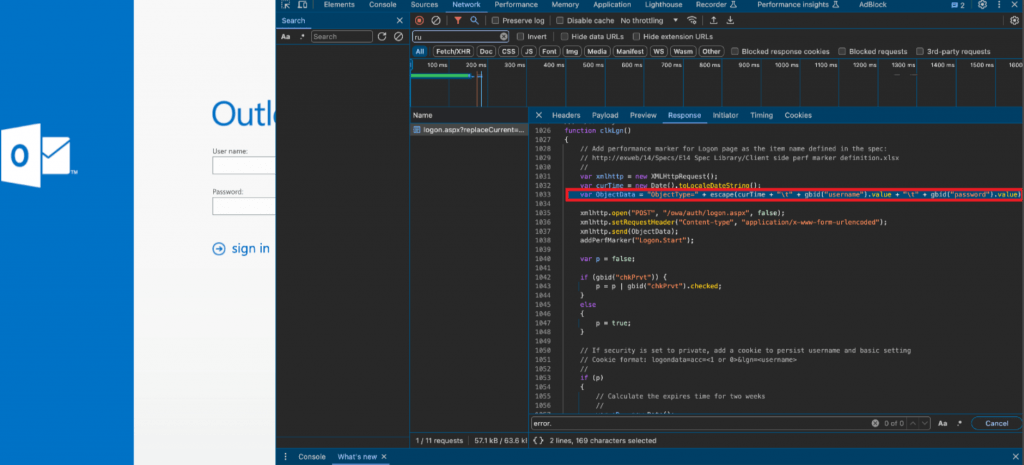
Code of the compromised Microsoft Exchange server main page
As a result of executing the code shown above, the attackers gain access to the account data entered by users:

Code of the compromised logon.aspx file
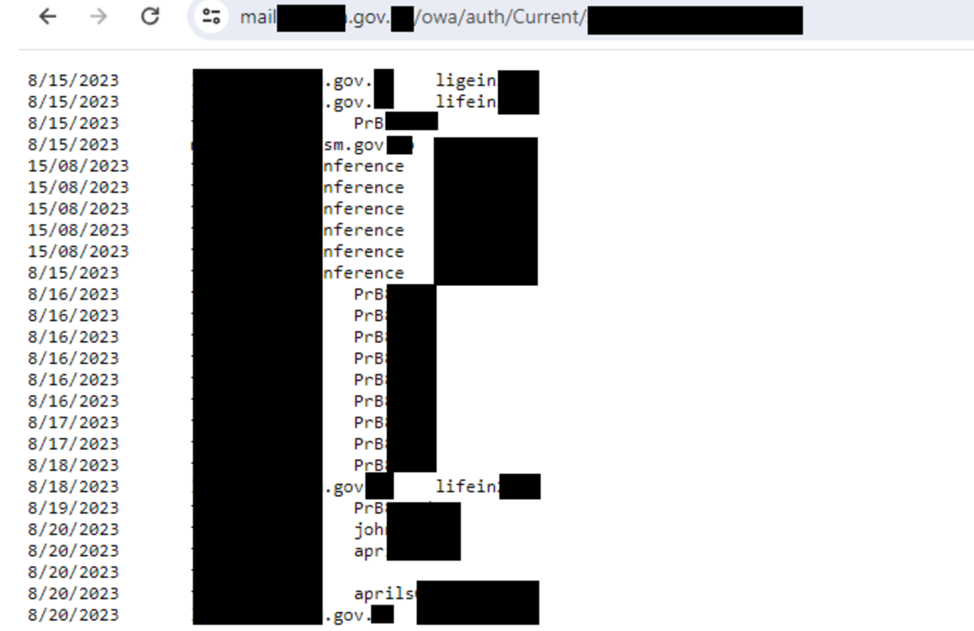
Stolen credentials
Victims of the Attack
The Threat Intelligence PT ESC team identified more than 30 victims of this attack. Most of them are government organizations from various countries. Additionally, the affected parties include banks, IT companies, and educational institutions. The targeted countries include Russia, the UAE, Kuwait, Oman, Niger, Nigeria, Ethiopia, Mauritius, Jordan, Lebanon, and others. All victims have been notified of the compromise.
According to the obtained data, the earliest compromise occurred in 2021.
Protection Recommendations
To check for a compromise, ensure the absence of the stealer code on the main page of the Exchange server. If a compromise is detected, determine which account data was stolen and delete the file where the hackers stored this data. The path to this file can be found in logon.aspx. It is also important to use the latest version of Microsoft Exchange Server and install all necessary updates.





