Kaspersky Warns: LockBit 3.0 Leak Makes Ransomware Worse
The latest study by Kaspersky Lab delves into the ramifications of the LockBit 3.0 builder leak that occurred in 2022. This event significantly empowered cybercriminals to create highly customizable malicious software versions, enhancing the threat of infection as it allowed hackers to tailor the virus spread across networks, disable security systems of target enterprises, encrypt data, and erase event logs to conceal their activities.
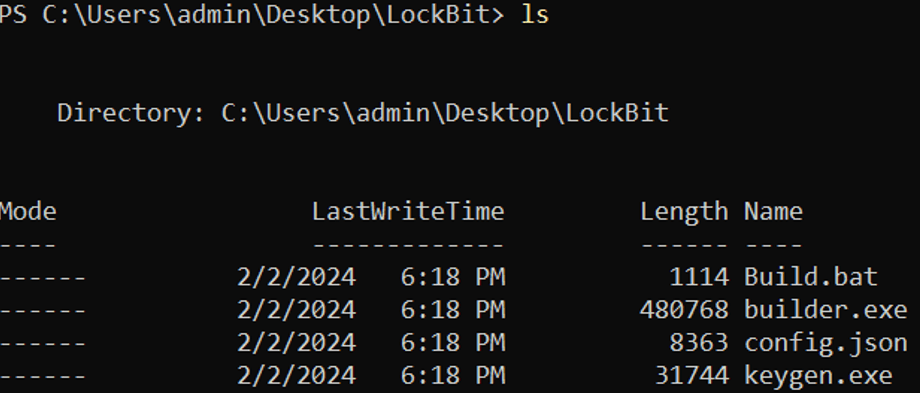
LockBit builder files
The LockBit 3.0 builder files greatly simplify the process of creating the necessary virus. Users can generate public and private keys for encrypting and decrypting data, as well as craft customized malware versions using the “Build.bat” script.
The configuration file enables the activation of functions such as spoofing identifiers, encrypting network drives, disabling security, and network propagation. This allows criminals to create a virus that can be precisely adapted to the architecture of the targeted network.
In February 2024, international law enforcement agencies conducted an operation to dismantle the LockBit infrastructure; however, the group soon announced its resurgence. Research indicated that files created using the leaked builder were utilized for attacks worldwide, including in CIS countries.
During the investigation of the incident, various techniques and tools used by the criminals to spread and manage the attack were identified, including the use of the SessionGopher script to extract saved credentials.
To mitigate the risk of similar attacks, it is recommended to utilize reliable antivirus solutions, disable unused services and ports, update systems and software, conduct regular penetration tests and vulnerability scans, and provide cybersecurity training for employees.
The analysis of the LockBit 3.0 builder file demonstrates how easily criminals can create new malware. This underscores the need for comprehensive protective measures and the development of a cybersecurity culture among employees to effectively counter such threats.





