Juniper Support Portal Leaks Sensitive Customer Data
A 17-year-old researcher discovered that through the Juniper customer support portal, information about devices and support contracts for numerous clients could be accessed. The data leak has been ongoing since September 2023.
Esteemed cybersecurity journalist Brian Krebs shared in his blog that in early February 2024, 17-year-old intern Logan George, working at an unnamed organization utilizing Juniper products, uncovered a significant data breach on the Juniper customer support portal.
According to George, he stumbled upon the leak accidentally while seeking support information for a Juniper product. It turned out that after logging into the system with a standard client account, detailed information about virtually any Juniper device purchased by other companies could be found on the support site.
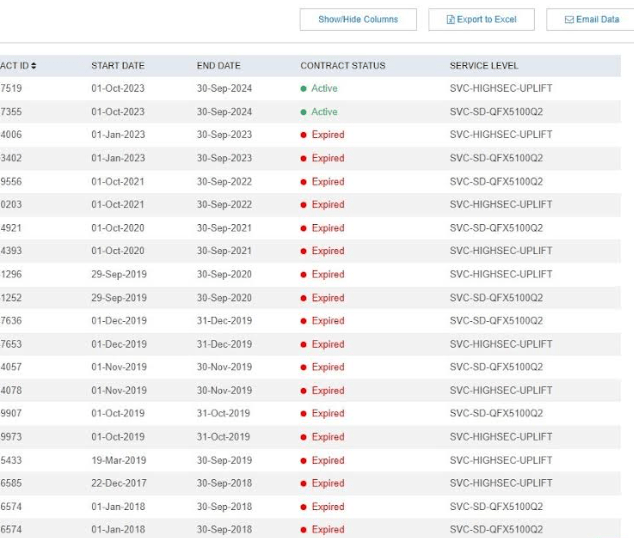
Information exposed by the Juniper support portal. Columns not pictured include Serial Number, Software Support Reference number, Product, Warranty Expiration Date and Contract ID.
For instance, searching for “Amazon.com” on the Juniper portal revealed tens of thousands of records. Each record contained details about the device’s model and serial number, its approximate installation location, as well as the device’s status and information about the corresponding support contract.
The researcher notes that the exposed information about contracts is particularly important as it indicates which Juniper products are most likely missing critical patches.
“If you don’t have a support contract you don’t get updates, it’s as simple as that,” George said. “Using serial numbers, I could see which products aren’t under support contracts. And then I could narrow down where each device was sent through their serial number tracking system, and potentially see all of what was sent to the same location. A lot of companies don’t update their switches very often, and knowing what they use allows someone to know what attack vectors are possible.”
Juniper representatives informed Krebs that the data leak resulted from a recent upgrade to the support portal.
“We were made aware of an inadvertent issue that allowed registered users to our system to access serial numbers that were not associated with their account,” the statement reads. “We acted promptly to resolve this issue and have no reason to believe at this time that any identifiable or personal customer data was exposed in any way. We take these matters seriously and always use these experiences to prevent further similar incidents. We are actively working to determine the root cause of this defect and thank the researcher for bringing this to our attention.”
However, the company did not disclose when the error occurred or how long user information was accessible to third parties. It is presumed that the bug was related to changes made in September 2023, when Juniper announced the reconstruction of its customer support portal.
George believes that the backend of Juniper’s support site is maintained by Salesforce and that Juniper specialists likely forgot to set appropriate user rights on Salesforce resources.





