IRIS – Incident Response Investigation System
IRIS is a web collaborative platform for incident response analysts allowing them to share investigations at a technical level.
It’s a web application, so it can be either installed on a fixed-server, or on a laptop for roaming investigations where the internet might not be available.
It is born following the struggle to share long and complex investigations among analysts. Most of the current similar platforms are either commercial or targeting the incident handling and triage steps, not the investigation itself.
What can I do with Iris?
You can :
- Run investigations with as many analysts as you want. Everyone has its own account
- Run as many investigations as you want in parallel
-
- For each investigation:
-
- Associate a customer
- Create a high-level summary
- Create notes under the form of a Kandan board
- Create IOCs
- Create assets (computers, servers, accounts, firewalls, or anything you want)
- Associate IOCs with assets
- Obtain insights on assets and IOCs previously encountered in investigations
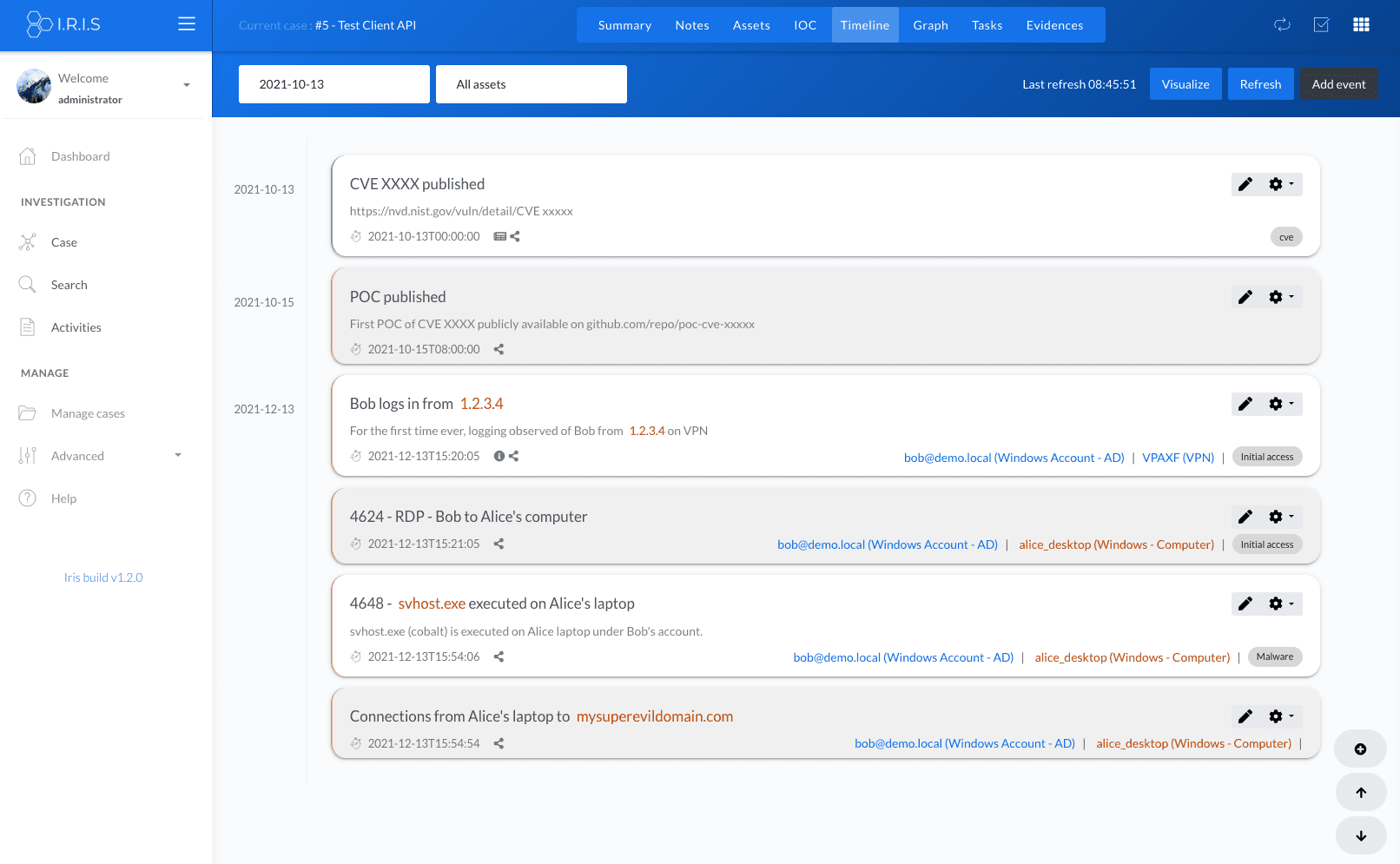
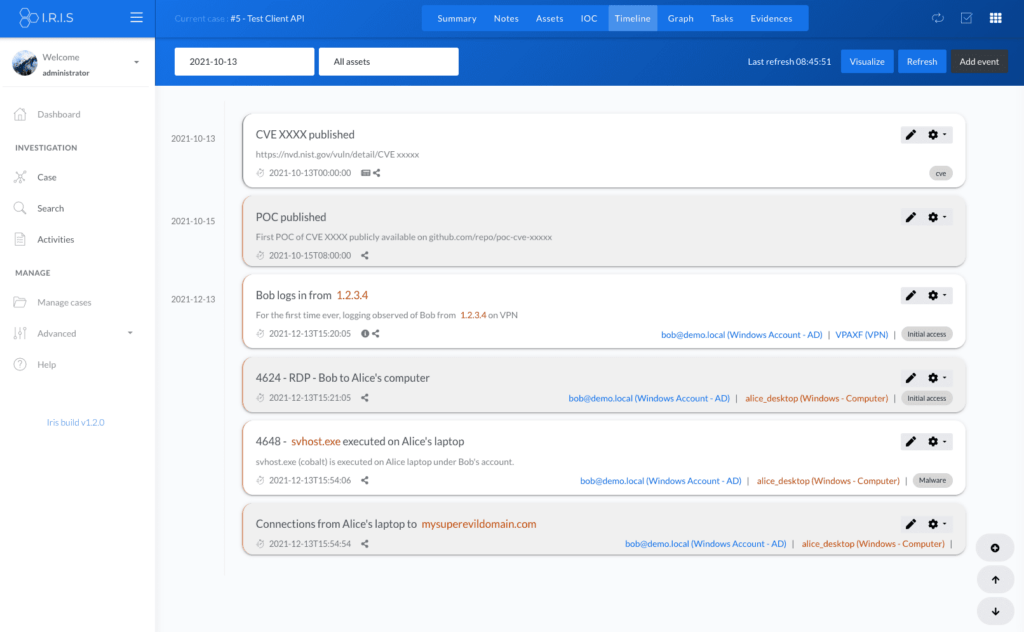
- Create a proper timeline referencing assets and IOCs
- Create an automated graph of the attack from the timeline
- Register evidences
- Upload and process of evidences through modular pipelines (eg: EVTX parsing and injection into a database or data visualiser)
- Set and attribute tasks to people to keep track of everything
- Register every steps of the investigation
- Generate a report based on templates, automatically filled with the elements registered in the investigation
- Generate a report of activity with every steps registered as well as the auto-registered entries for each analyst
- Search notes and IOCs across all investigations
- Develop your own module and pipeline to process evidences and fit your needs. These are processed through RabbitMQ.
Install & Use
© Copyright 2021, Airbus CyberSecurity.





