Iran-Linked Hackers Target Middle East Defense Firms
According to the latest insights from analysts at Mandiant, the Middle East has become the focal point of an ongoing cyber espionage operation utilizing distinctive malware targeting the aerospace, aviation, and defense industries. The traces of this operation lead back to Iran, as noted by researchers.
The campaign’s activities are primarily directed against Israel and the United Arab Emirates, with potential implications for Turkey, India, and Albania as well. Experts believe this operation is linked to the Iranian group UNC1549, previously implicated in cyber attacks against American and Israeli companies within the maritime, aerospace, and defense sectors.
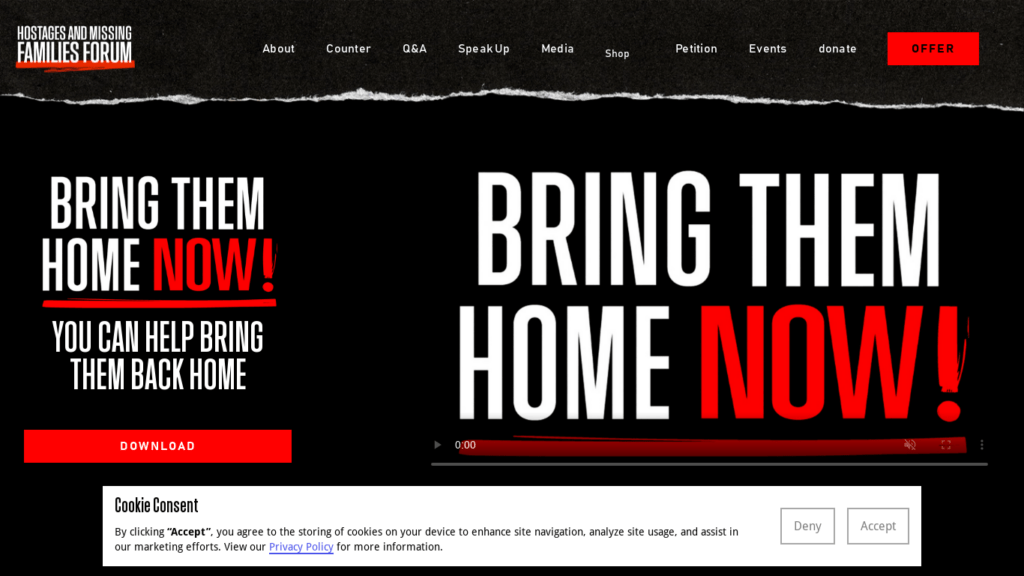
Fake website posing as the “Bring Them Home Now” movement, calling for the return of Israelis kidnapped by Hamas
The potential connection of this campaign to the Islamic Revolutionary Guard Corps (IRGC) of Iran, especially amidst the recent tensions stemming from the war between Israel and the Hamas movement, which Iran overtly supports, is particularly noteworthy.
The campaign has been characterized by the use of numerous evasion techniques, including the extensive use of Microsoft Azure cloud infrastructure and social engineering to disseminate two unique backdoors: MINIBIKE and MINIBUS. These malicious programs enable a range of actions from file theft to the execution of arbitrary commands and enhanced reconnaissance.
Additionally, researchers discovered LIGHTRAIL—a specialized tunneling software that conceals malicious activity by “wrapping” malicious traffic in regular internet traffic.
It is important to highlight that the campaign’s inception dates back to June 2022, with the latest activities recorded in January of this year, indicating the prolonged and deliberate nature of this operation.
The sophistication and high skill level of the hackers underscore the serious threat Advanced Persistent Threat (APT) groups pose to states and major companies in critical industries.
To counter this threat, a comprehensive approach is required, encompassing the strengthening of cybersecurity measures, the adoption of advanced technologies, and the enhancement of employee awareness regarding cyber hygiene practices. These measures are pertinent to both governmental and private sector entities.





