IcedID’s Successor: Latrodectus Targets Users via Phishing
Since the beginning of March this year, cybersecurity researchers have observed a sharp increase in phishing campaigns aimed at distributing a new malware loader, Latrodectus, considered the successor to IcedID.
Experts from Elastic Security Labs, Daniel Stepanic and Samir Bousseaden, reported that these campaigns employ large JavaScript files, utilizing WMI capabilities to launch “msiexec.exe” and install a remotely hosted MSI file via WEBDAV.
Latrodectus possesses standard functionalities typical of malware designed to download additional payloads such as QakBot, DarkGate, and PikaBot, allowing attackers to execute various post-exploitation activities. Analysis revealed that the malware actively enumerates and executes commands, including a self-deletion technique.
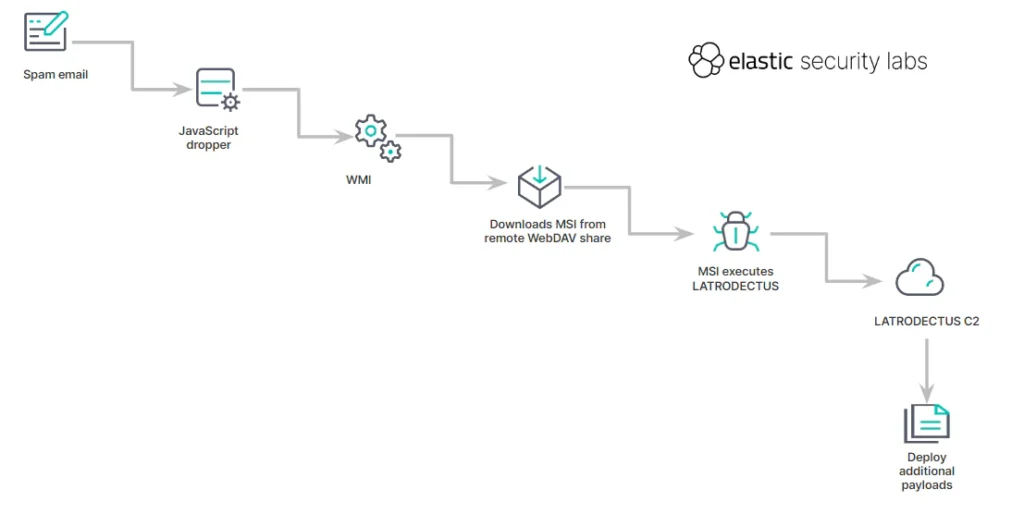
LATRODECTUS campaign overview
Additionally, Latrodectus disguises itself as libraries associated with legitimate software, employs code obfuscation, and performs analysis checks to prevent its operation in a debugging or sandbox environment.
The malware also establishes persistence on Windows systems through scheduled tasks and communicates with a command-and-control (C2) server via HTTPS to receive commands for system information gathering, updates, restarts, termination, shellcode execution, DLL, and executable file launching.
Among the new commands added to Latrodectus since late last year are commands for enumerating desktop files and retrieving the entire process chain on an infected device. The malware also supports a command to download and execute IcedID, although Elastic researchers have not observed this behavior in practice.
“One hypothesis being considered is that LATRODECTUS is being actively developed as a replacement for ICEDID, and the handler (#18) was included until malware authors were satisfied with LATRODECTUS’ capabilities,” the experts stated.
Thus, malicious actors are continuously refining their malware distribution methods, creating sophisticated loaders and bots to infiltrate computer systems. They adapt and utilize advanced masking techniques to evade detection by antivirus programs.
It is crucial to regularly update security tools, enhance user awareness, and implement multi-layered defenses to counter the ever-evolving cyber threats.





