How to secure SSH service with Fail2Ban
Fail2Ban scans log files like /var/log/auth.log and bans IP addresses conducting too many failed login attempts. It does this by updating system firewall rules to reject new connections from those IP addresses, for a configurable amount of time. Fail2Ban comes out-of-the-box ready to read many standard log files, such as those for sshd and Apache, and is easily configured to read any log file of your choosing, for any error you wish.
On this post, I’m going guide you on how to secure SSH service with Fail2Ban.
apt–get install fail2ban
[ssh]enabled = trueport = sshfilter = sshdlogpath = /var/log/auth.logmaxretry = 5findtime = 3600bantime = 86400
bantime: blocking time in seconds
Save and restart Fail2ban:
service fail2ban restart
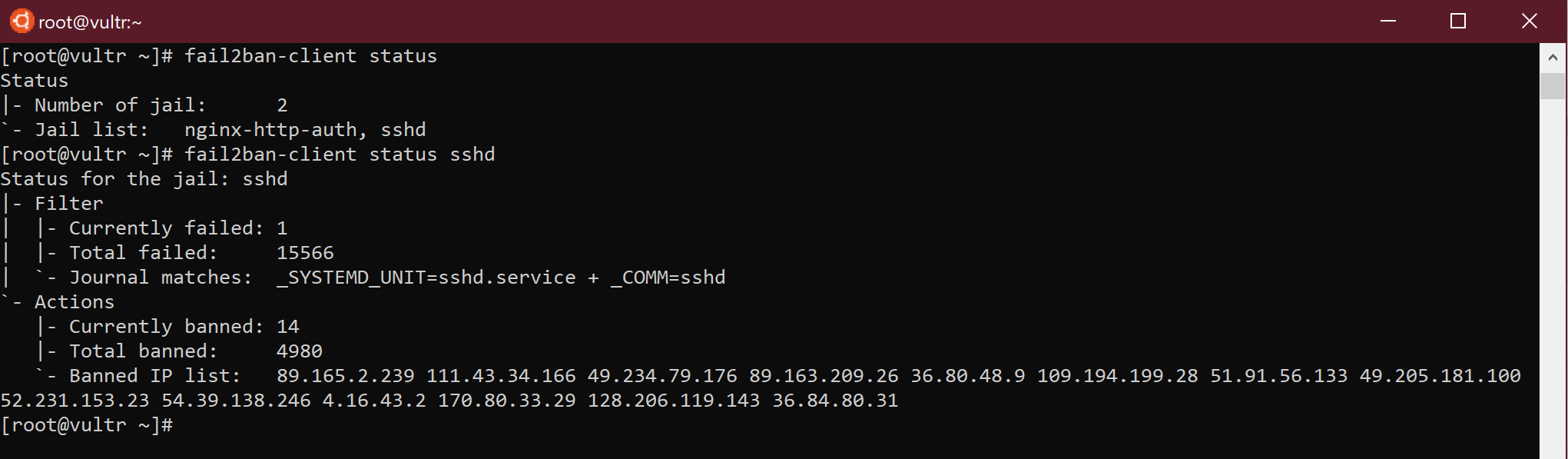
fail2ban–client status
fail2ban–client status service_name