Hacking Google: From Password Resets to Persistent Access
According to a report presented by CloudSEK, a new hacking method enables hackers to exploit the OAuth 2.0 authorization protocol functionality to compromise Google accounts. This technique maintains valid sessions by regenerating cookie files, even after changing the IP address or password.
The attack, executed via an undocumented Google Oauth access point named “MultiLogin,” was identified by the CloudSEK research team. “MultiLogin” is an internal mechanism designed for synchronizing Google accounts across various services, ensuring the alignment of account states in the browser with Google authentication cookies.
It is noted that the exploit developer expressed a willingness to collaborate, which expedited the discovery of the access point responsible for cookie file regeneration.
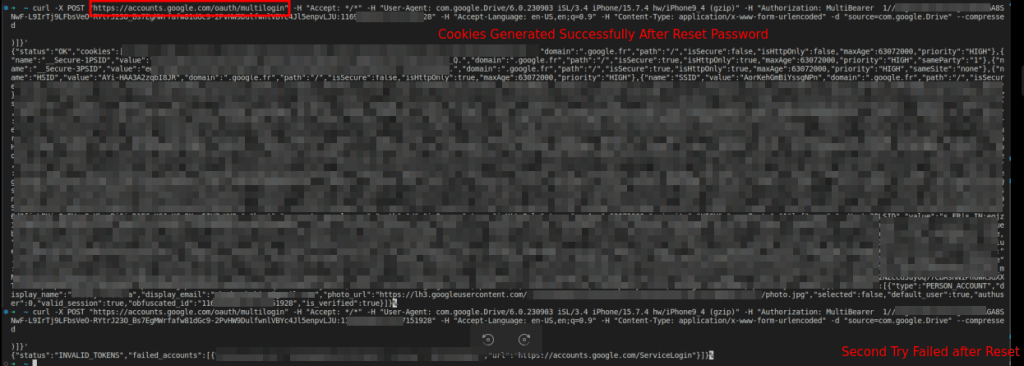
Successful Regeneration of Cookies after Resetting Password. | Image: Cloudsek
The exploit was integrated into the malicious Lumma Infostealer software on November 14th. Key features of Lumma include session persistence and cookie file generation. The program targets the extraction of essential secrets, tokens, and account identifiers, attacking the token_service table in WebData of logged-in Chrome profiles.
“The session remains valid even when the account password is changed, providing a unique advantage in bypassing typical security measures. The capability to generate valid cookies in the event of a session disruption enhances the attacker’s ability to maintain unauthorized access,” quotes the report from PRISMA, the exploit’s author.
Researchers highlight a concerning trend towards the rapid integration of exploits among various cybercriminal groups. The exploitation of the undocumented Google OAuth2 MultiLogin access point exemplifies complexity, as the approach is based on the delicate manipulation of the GAIA ID token (Google Accounts and ID administration). The malware conceals the exploit mechanism using an encryption layer.
This exploitation technique demonstrates a high level of sophistication and understanding of Google’s internal authentication mechanisms. “By manipulating the token:GAIA ID pair, Lumma can continuously regenerate cookies for Google services. Even more alarming is the fact that this exploit remains effective even after users have reset their passwords. This persistence in access allows for prolonged and potentially unnoticed exploitation of user accounts and data,” concluded the CloudSEK team.





