guac: Graph for Understanding Artifact Composition
GUAC: Graph for Understanding Artifact Composition
Graph for Understanding Artifact Composition (GUAC) aggregates software security metadata into a high-fidelity graph database—normalizing entity identities and mapping standard relationships between them. Querying this graph can drive higher-level organizational outcomes such as audit, policy, risk management, and even developer assistance.
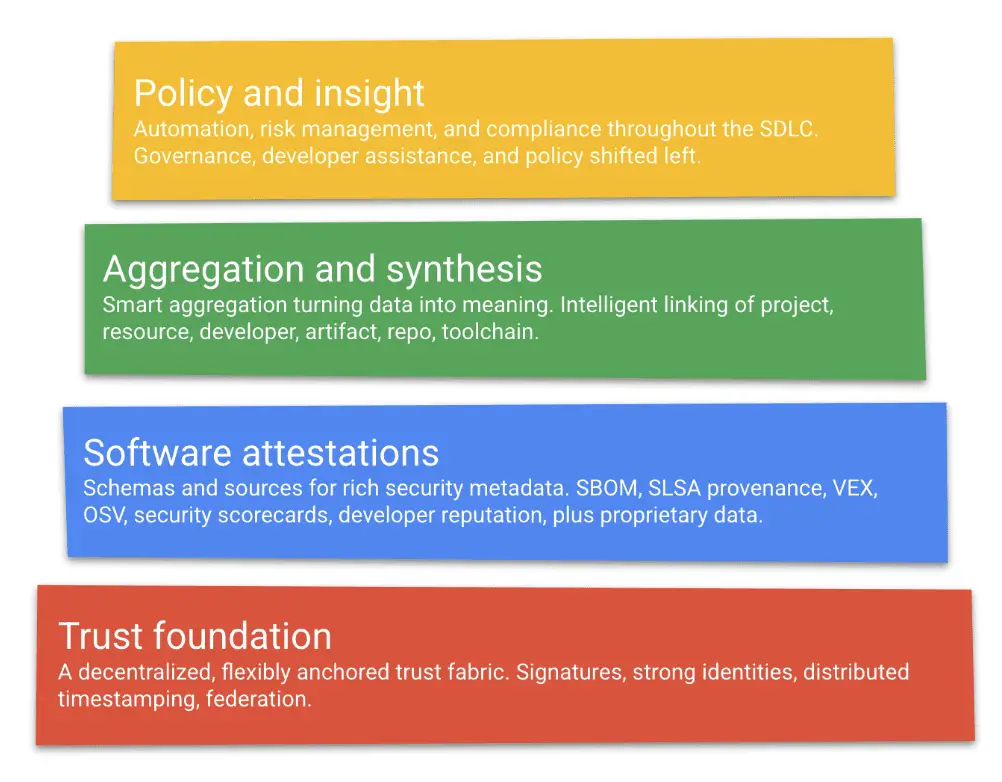
Conceptually, GUAC occupies the “aggregation and synthesis” layer of the software supply chain transparency logical model:
A few examples of questions answered by GUAC include:

GUAC has four major areas of functionality:
- Collection
GUAC can be configured to connect to a variety of sources of software security metadata. Some sources may be open and public (e.g., OSV); some may be first-party (e.g., an organization’s internal repositories); some may be proprietary third-party (e.g., from data vendors). - Ingestion
From its upstream data sources, GUAC imports data on artifacts, projects, resources, vulnerabilities, repositories, and even developers. - Collation
Having ingested raw metadata from disparate upstream sources, GUAC assembles it into a coherent graph by normalizing entity identifiers, traversing the dependency tree, and reifying implicit entity relationships, e.g., project → developer; vulnerability → software version; artifact → source repo, and so on. - Query
Against an assembled graph one may query for metadata attached to, or related to, entities within the graph. Querying for a given artifact may return its SBOM, provenance, build chain, project scorecard, vulnerabilities, and recent lifecycle events — and those for its transitive dependencies.
Install & Use
Copyright 2022 The GUAC Authors





