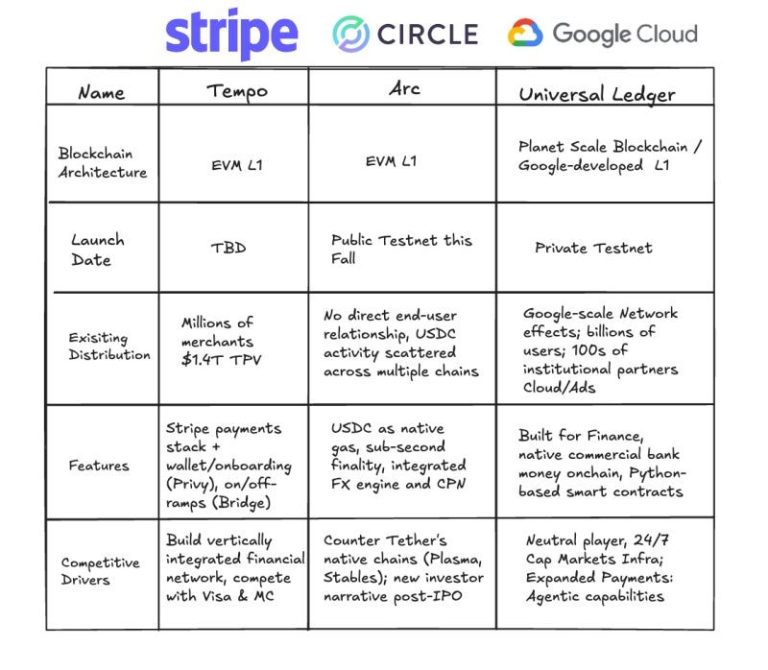
Open-source software forms the bedrock of today’s digital infrastructure, powering 77% of all applications and valued at over $12 trillion. Yet its widespread adoption renders it an increasingly attractive target for supply chain attacks, in which malicious actors inject harmful code into trusted components. Such intrusions can erode the confidence of both developers and users, potentially stalling the growth of entire ecosystems.
In recent years, several high-profile incidents have underscored the severity of the threat. In the solana/webjs project, attackers leveraged a compromised npm account to introduce a backdoor capable of exfiltrating cryptographic keys. In the tj-actions/changed-files GitHub repository, a malicious GitHub Action was embedded, leading to the leakage of sensitive secrets. One of the most sophisticated examples was the backdoor planted in xz-utils, which enabled remote access through a compromised archiving utility.
To enhance transparency within the open-source ecosystem, Google has introduced OSS Rebuild, a tool designed to recreate package builds and verify their fidelity to the original source code. This process automatically generates metadata compliant with SLSA Build Level 3 standards, eliminating the need for direct involvement from project maintainers.
According to Google, the goal is to empower community members to examine package provenance and more effectively track changes throughout the build process.
The tool is tailored for both security professionals and project maintainers. For the former, it assists in identifying code discrepancies, build environment anomalies, and covert behaviors. For the latter, it offers a means to append integrity and reproducibility information to published versions.
At present, OSS Rebuild supports packages from PyPI (Python), npm (JavaScript/TypeScript), and Crates.io (Rust), with plans to expand into additional ecosystems.
Access to OSS Rebuild is provided via the command line. Using the utility, users can retrieve provenance details, inspect reconstructed builds, or initiate their own rebuilds.