Ghost in the Machine: Chinese Hackers Hijack Updates, Implant “NSPX30” Spyware
The Slovak cybersecurity firm ESET has uncovered the operations of a previously unknown hacker group linked to China, christening it with the codename Blackwood. Active since 2018, this group has specialized in adversary-in-the-middle (AitM), intercepting legitimate software update requests to deliver the sophisticated NSPX30 implant.
Discovered within the update mechanisms of well-known programs such as Tencent QQ, WPS Office, and Sogou Pinyin, the attacks targeted manufacturing, commerce, and engineering companies, as well as private individuals across China, Japan, and the United Kingdom.
NSPX30 is a multistage implant that includes a dropper, installer, loader, orchestrator, and backdoor, each with its own set of plugins, according to security researcher Facundo Muñoz.
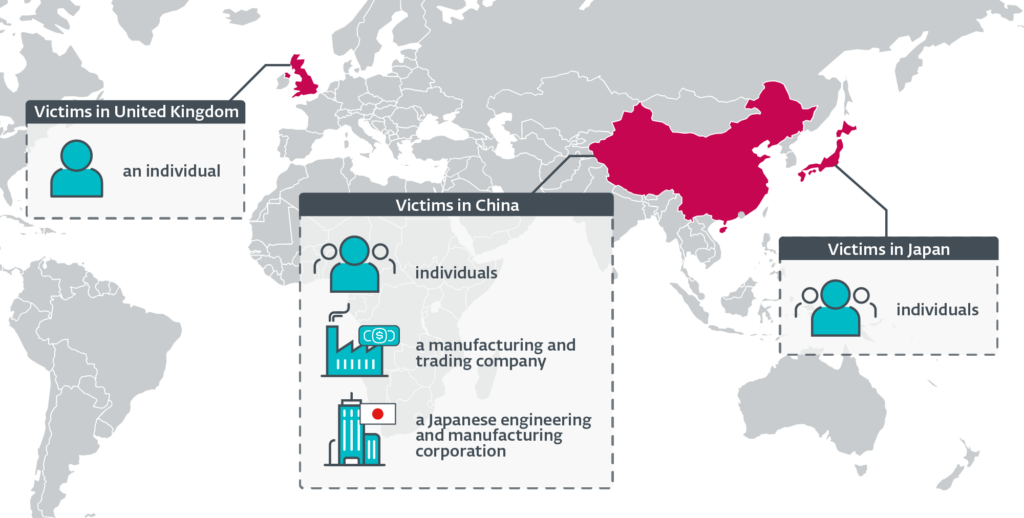
Geographical distribution of Blackwood victims
Capable of intercepting data packets, NSPX30 operators can conceal their infrastructure. The backdoor also evades a range of antivirus solutions by adding itself to whitelists.
The backdoor’s origins are linked to another malware, named Project Wood (2005), used for collecting system and network information, keystroke logging, and creating screenshots on infected systems.
NSPX30 is triggered when attempting to download software updates from legitimate servers via the unencrypted HTTP protocol, compromising the system and deploying malicious DLL.
The malicious dropper created during the compromised update process generates several files on disk and initiates “RsStub.exe” to activate “comx3.dll” through DLL Sideloading.
NSPX30’s orchestrator establishes two threads for receiving the backdoor and downloading its plugins, adding exceptions to bypass Chinese antivirus solutions.
The backdoor is downloaded via an HTTP request to the Chinese search engine Baidu, disguising the request as coming from Internet Explorer on Windows 98. The response from the server is saved to a file from which the backdoor component is extracted and loaded.
NSPX30 also creates a passive UDP socket for receiving commands from the controller and exfiltrating data, likely intercepting DNS request packets to anonymize its C2 infrastructure.
Backdoor commands enable the creation of a reverse shell, file information gathering, termination of specific processes, screenshot taking, keystroke logging, and even self-deletion from the infected machine.
This discovery serves as a crucial reminder that cyber threats are constantly evolving and require ongoing vigilance and refinement of protective mechanisms by organizations worldwide, especially in the realm of critical infrastructures.





