Fraud-as-a-Service: The Rise of Cybercrime Gangs on Online Marketplaces
Fraud on classifieds and marketplaces has become a serious issue due to the emergence of organized criminal groups operating under a “Fraud-as-a-Service” model. These groups continuously refine their methods to steal money and personal data from unsuspecting users.
Phishing ad
There are two main fraud schemes:
- Buyer Scam (scam 1.0) – The scammer poses as a seller and offers to ship the item to the buyer. When the buyer inquires about the shipping and payment conditions, the scammer (acting as the seller) requests the buyer’s full name, address, and phone number, along with payment on a specified website. If the victim agrees, they are sent a phishing link for payment (via a third-party messenger or directly in the marketplace dialogue if the platform does not block such links). Once the user enters their card details on the fake site, the scammer gains access to the card and drains all funds.
- Seller Scam (scam 2.0) – A more common scheme where the scammer poses as a buyer and deceives the seller into shipping the item with a promise of a “secure transaction” or using a “safe payment method.” Like scam 1.0, the scammer sends the seller a phishing link through a third-party messenger or directly in the marketplace dialogue. The page at the link requests the payment card details. If the seller enters them, the scammer drains the account.
Original ad
In both cases, the victim is redirected to a fake website that visually mimics the real one, but its sole purpose is to steal information. Below is a detailed breakdown of the scam 2.0 scheme.
Scam 2.0 Details
The scammers meticulously select potential victims, targeting ads where the seller has paid for promotion, posted high-quality photos, and is willing to communicate via messengers. They also look for sellers who use third-party messengers and are willing to provide a phone number, which they ascertain during initial communications.
The primary goal of the scammers is to convince the victim to click on a phishing link and enter their payment details. Communication begins with standard questions about the item, its condition, reasons for selling, etc. Experienced scammers ask no more than three questions to avoid raising suspicion.
The scammer then expresses interest in purchasing but claims they cannot collect the item in person or pay in cash due to being in another city (or some other reason). They propose using “secure delivery.”
The scammer elaborates on the fictitious payment scheme, asking the victim to follow a phishing link and enter their details for money transfer. The payment process typically looks like this:
- I pay for the item on [name of site].
- You get a link to receive the money.
- You follow the link and enter your card details to receive the payment.
- Once you receive the money, the delivery service will contact you to establish your preferred shipping method. Shipping will already be paid for. The delivery service will pack and document the item for you.
If the seller agrees, the scammers gain access to their payment details and clean out the accounts. The item’s value does not matter; even if the seller lists a small amount, the scammers will take everything they can.
If the victim resists or insists on an official payment method, the scammer disappears to avoid wasting time. If the seller requests to continue communication on the official marketplace site, the scammer assumes they are aware of the scam and will not click the phishing link, thus ending the conversation and seeking a new target.
Types of Phishing Pages in Scam 2.0
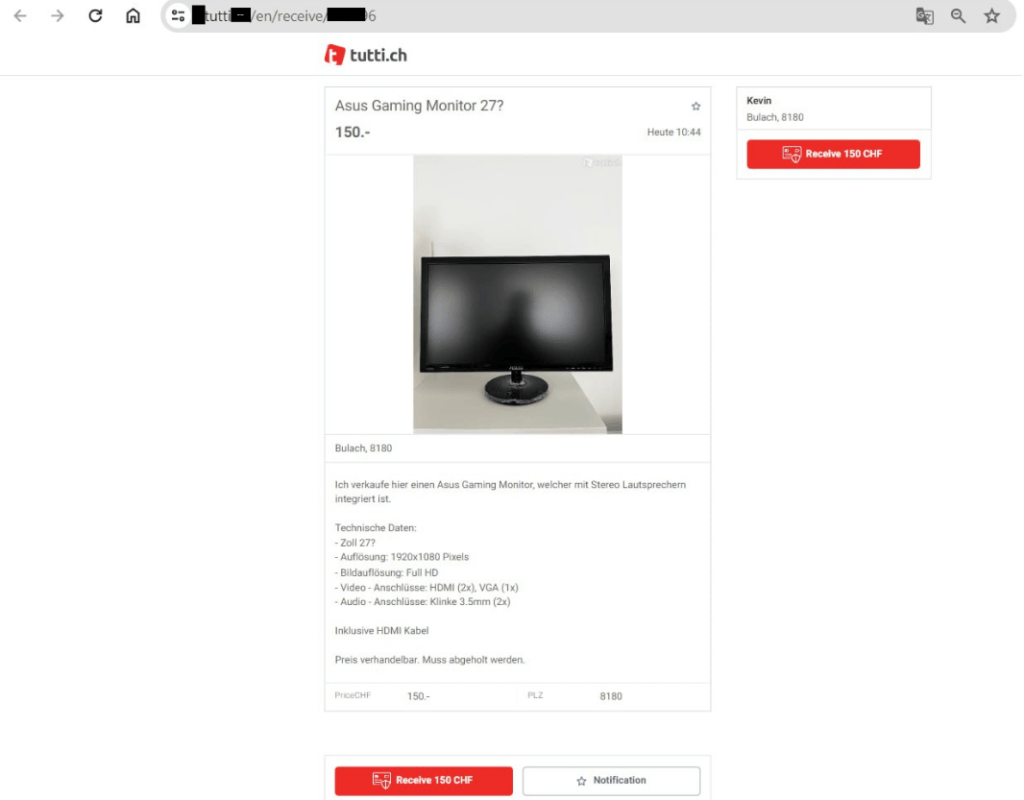
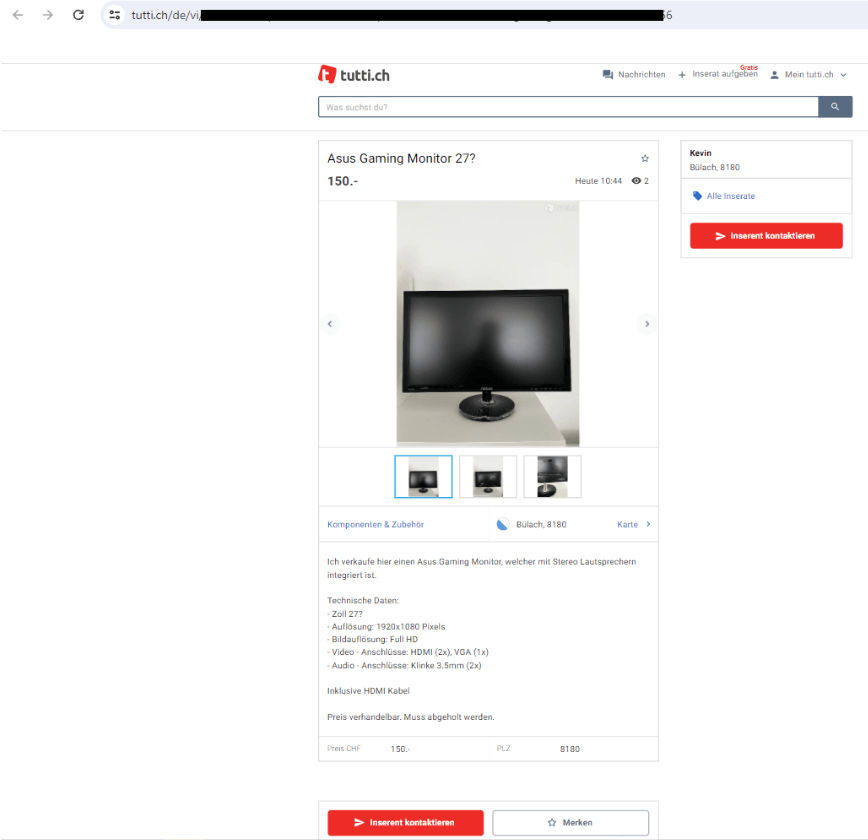
There are two main types of phishing pages: one that replicates the marketplace’s ad page, and another that mimics secure payment services like Twin. The fake page differs from the original only in minor details. For instance, instead of the “Contact Advertiser” button, the phishing page may have a “Receive 150 CHF” button.
Structure of Fraudulent Groups
Recently, entire groups of scammers have emerged, specializing in classifieds fraud, practicing both scam 1.0 and scam 2.0. These criminal groups have well-defined roles:
- Organizers manage the group’s overall activities.
- Coders are responsible for developing and maintaining the technical infrastructure.
- Support Staff assist victims with their “issues” until their money is stolen.
- Withdrawers handle the direct theft of money from stolen accounts.
- Field Agents directly interact with the victims.
- Others with various roles.
A deceived user is referred to as a “mammoth,” the amount on the bank card provided by the victim is called “logs,” and the stolen amount is called “profit.”
Communication and Operational Geography
Scammers communicate in closed chats, maintain statistics, and constantly improve their methods. Scam 1.0 and scam 2.0 schemes have been around for several years and are still common on Russian-speaking classifieds. However, scammers have recently shifted focus to foreign countries, particularly Switzerland, where the population is less familiar with these fraud schemes. To gain trust, they study local languages and customs. The group also operates in Canada, Austria, France, and Norway.
Fraud as a Service (FaaS)
The groups operate on a “Fraud-as-a-Service” model, where the main service consumer is the field agent. Organizers ensure the functioning of services (channels/chats/bots in Telegram, phishing websites, payment processing, money laundering), provide moral support, and manuals for the field agents, taking a commission from each transaction.
Detailed manuals are available for novice agents on how to register, ensure anonymity, conduct dialogues with victims, bypass platform security restrictions, etc. After obtaining payment details, “withdrawers” use various methods to steal money—applying for loans, transferring to e-wallets, buying electronics, etc.
Automation Tools
Special Telegram bots are used to automate the process, quickly creating phishing links that mimic real site interfaces, tracking victim clicks, and receiving notifications of “successful” payments. These bots are constantly updated with new statistics, tools, and functions.
Preventive Measures
To avoid falling victim to such scams, it is crucial to trust only official websites, avoid clicking on links from unreliable sources, refrain from entering card details until the item is received, and avoid QR codes from suspicious places.





