Flow Analyzer: help in testing and analyzing OAuth 2.0 Flows
Flow Analyzer
Flow Analyzer is designed for helping in low-level understanding and testing of OAuth 2.0 Grants/Flows.

OpenID Connect (OIDC)
OAuth 2.0 was designed for authorization. OpenID Connect (OIDC) extends the OAuth 2.0 functionality to provide authentication. There are a few different components that are necessary to understand if you are interested in knowing how it works and what is happening at a lower level as they interact with each other.
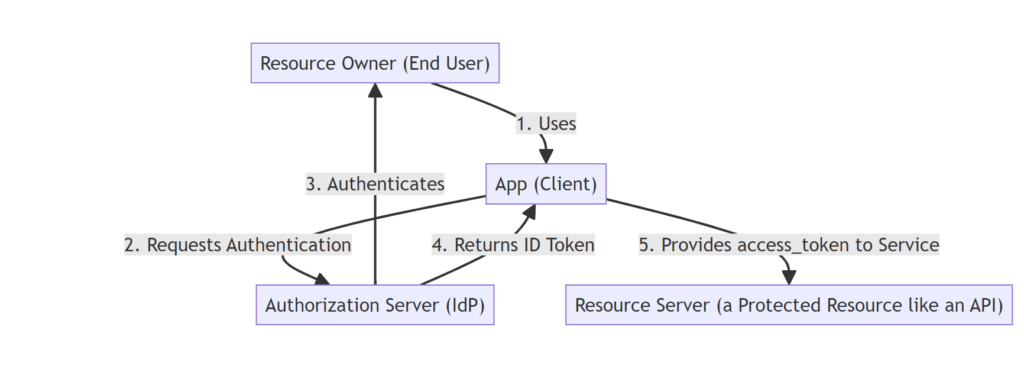
The diagram shows a high level view of how OIDC works
There are four essential parties involved in the authentication & authorization flows:
- Resource owner (End user)
- Client (The App the user is trying to use)
- Authorization Server (Identity Provider aka IdP)
- Resource Server (The API/Resource we are attempting to access)
JSON Web Tokens aka JWT(s)
JWTs are the token type that OAuth uses. What that really means, is that each time we execute a flow and request a token in OAuth, we will get back a JWT for all three types of security tokens (id_token, access_token, refresh_token).
There are three components to a JWT:
- Header
- Payload
- Signature.
The three components are separated by a dot “.” character, which looks like this {Header}.{Payload}.{Signature}.
Further, each of the three components is base64url encoded to make it safe to travel the interwebs, because bas64 is a proven method to transfer data using the HTTP protocol. Base64 helps deliver special characters and binary data which HTTP may not agree with directly.
The first 2 components are JSON objects containing the necessary information to identify how to handle the token via the Header, while the Payload contains the Claims contain critical data that allow the application to perform it’s duties. Last but not least, the third component is the signature calculated most often by the IdP.





