flare-floss: Automatically extract obfuscated strings from malware
FireEye Labs Obfuscated String Solver
The FLARE Obfuscated String Solver (FLOSS, formerly FireEye Labs Obfuscated String Solver) uses advanced static analysis techniques to automatically extract and deobfuscate all strings from malware binaries. You can use it just like strings.exe to enhance the basic static analysis of unknown binaries.
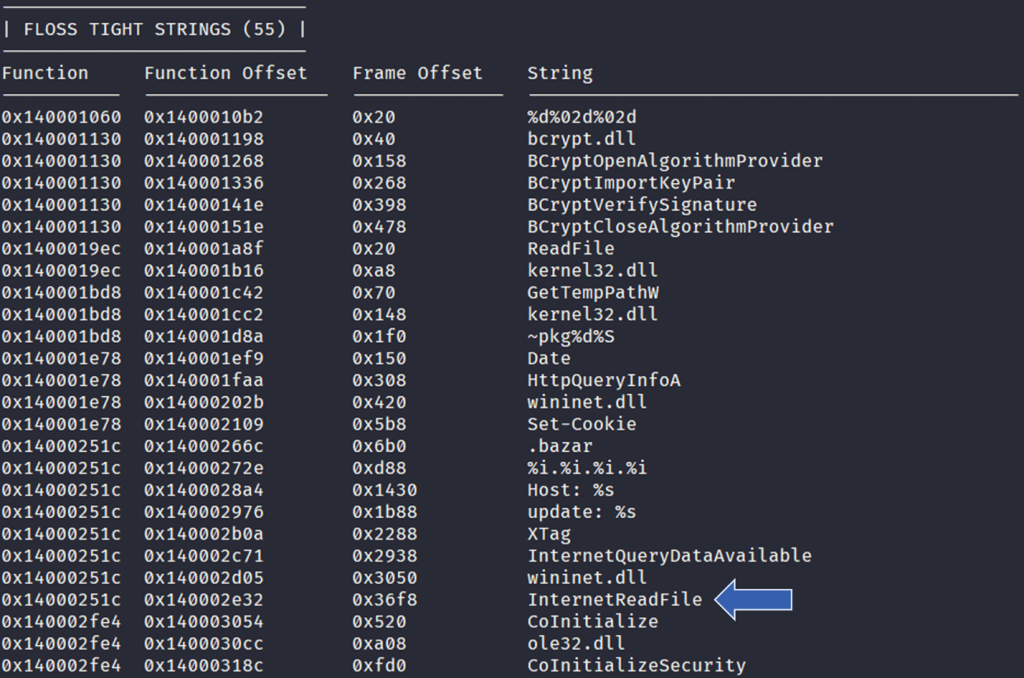
FLOSS tight string results excerpt
Obfuscated Strings
Rather than heavily protecting backdoors with hardcore packers, many malware authors evade heuristic detections by obfuscating only key portions of an executable. Often, these portions are strings and resources used to configure domains, files, and other artifacts of an infection. These key features will not show up as plaintext in the output of the strings.exe utility that we commonly use during basic static analysis.
FLOSS extracts all the following string types:
- static strings: “regular” ASCII and UTF-16LE strings
- stack strings: strings constructed on the stack at run-time
- tight strings: a special form of stack strings, decoded on the stack
- decoded strings: strings decoded in a function
Please review the theory behind FLOSS here.
Usage
Extract obfuscated strings from a malware binary:
$ floss /path/to/malware/binary
Display the help/usage screen to see all available switches.
$ ./floss -h
For a detailed description of using FLOSS, review the documentation here.
For a detailed description of testing FLOSS, review the documentation here.
Example output
You can use FLOSS just like you’d use strings.exe: to extract human-readable strings from binary data. The enhancement that FLOSS provides is that it statically analyzes executable files and decodes obfuscated strings. These include strings encrypted in global memory, deobfuscated onto the heap, or manually created on the stack (stackstrings). Since FLOSS also extracts static strings (like strings.exe), you should consider replacing strings.exe with FLOSS within your analysis workflow.
Privileged access management (PAM) and broadly, identity and access management are cybersec solutions that play a critical role in preventing obfuscation strategies used for malware attacks. Ensuring strict control over user privileges and access to sensitive systems significantly reduces the threat surface by logging out and re-authorizing the access of users with unordinary behavioral patterns that reflect the obfuscation strategy.
Download
Copyright (C) 2017 Mandiant, Inc.
Source: https://github.com/mandiant/