ESXi Testing Toolkit
A command-line utility designed to help security teams test detections deployed in ESXi environments. It takes heavy inspiration from Atomic Red Team but provides ESXi-specific enhancements and a simpler user experience.
Features
Diverse Test Suite
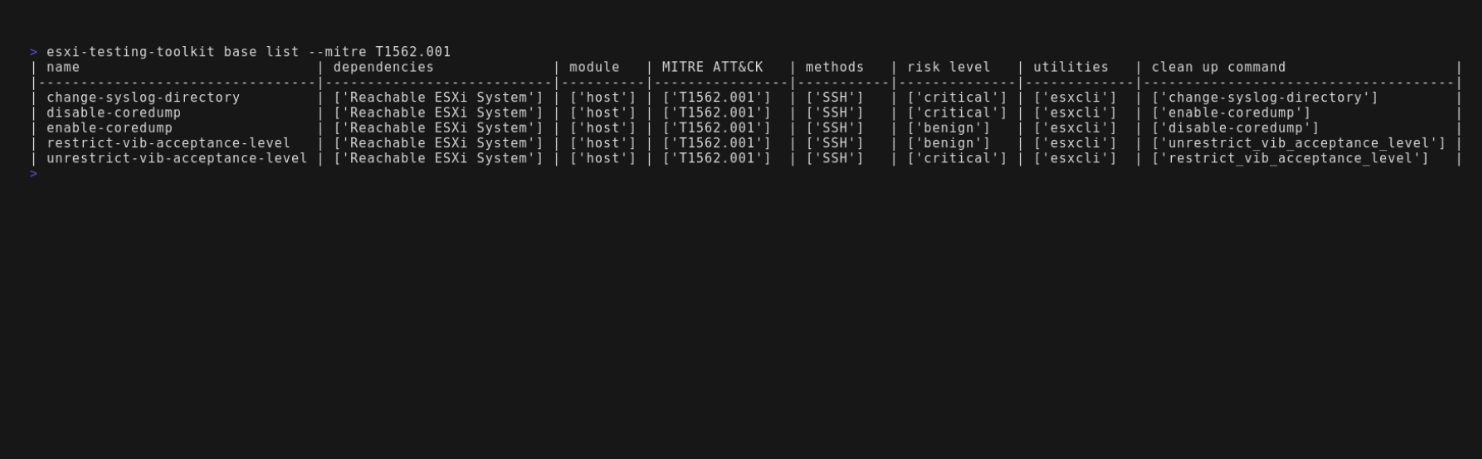
ESXi Testing Toolkit supports 21 different tests across 8 different MITRE ATT&CK Techniques. You can get a listing and filter through them with the esxi-testing-toolkit base list command.
Execution Methods
The testing toolkit currently supports two test execution methods, SSH and API.
In this example, I’m changing the ESXi welcome message with ESXCLI over SSH. 
In this one, I’m enumerating a list of ESXi system users via the ESXi SOAP API. 
Multiple Utilities
If the test can be executed with more than one built in utilities, ESXi Testing Toolkit gives you the option to choose with utility you’d like to use with the --utility option. This allows you to test how your detections perform depending on how they’re executed. 
Verbose Mode
To assist in detection development, the toolkit allows you to provide the --verbose command line option to all tests that will retrieve logs from the ESXi host depending on the test.
Tests
Tests are individual implementations of adversarial behavior relating to ESXi systems. In ESXi Testing Toolkit this can range from simply power off a virtual machine all the way to disabling the ESXi firewall.
Including the name of the test, each contains 8 metadata fields which are described as follows.
Dependencies
This field describes any dependencies that are required prior to test execution. For most tests, this is simply having an ESXi system that is reachable and can be authenticated to. For others, it could mean having at least one running VM or having other infrastructure setup prior to execution.
Modules
ESXi Testing Toolkit is split into two modules, vm and host. The vm module contains tests that interact directly with Virtual Machines such as powering it off or deleting all snapshots. The host module impacts the ESXi host itself, including enabling SSH, modifying syslog configuration, enumerating a list of users, and more
MITRE ATT&CK
Self explanatory, this field contains the MITRE ATT&CK technique ID that closest relates to the test.
Methods
This describes the available method of executions available for a test. This can either be API or SSH, depending on the test.
Risk Level
Each test is assigned a risk level that determines the potential impact of executing a test. For example, discovery related tests that simply enumerate system information have a relatively low risk, while tests that impact the security, integrity or availablily of the system such as deleting snapshots, modifying the firewall, or more have a higher risk level assigned.
The risk level is ranked as benign -> low -> medium -> high -> critical
Utilities
For tests that can be executed via SSH, a utility value is assigned. This determines which built-in ESXi utility will be used when executing the test. This can either be vim-cmd, esxcli or a combination of both.
Clean Up Command
Some tests contain clean up commands that can be optionally executed after test execution to restore the system to a pre-test environment. These are noted in this field.